当前位置:网站首页>Ctf-misc learning from start to give up
Ctf-misc learning from start to give up
2022-04-23 08:00:00 【Five five six six 0524】
The whole learning process follows Hetian Wangan Laboratory
2021.1.5 No. updated for the first time
Learn the common routine of compressed package tonight



1、 Use binary conversion to hide information
The title gives a document , There are hexadecimal numbers
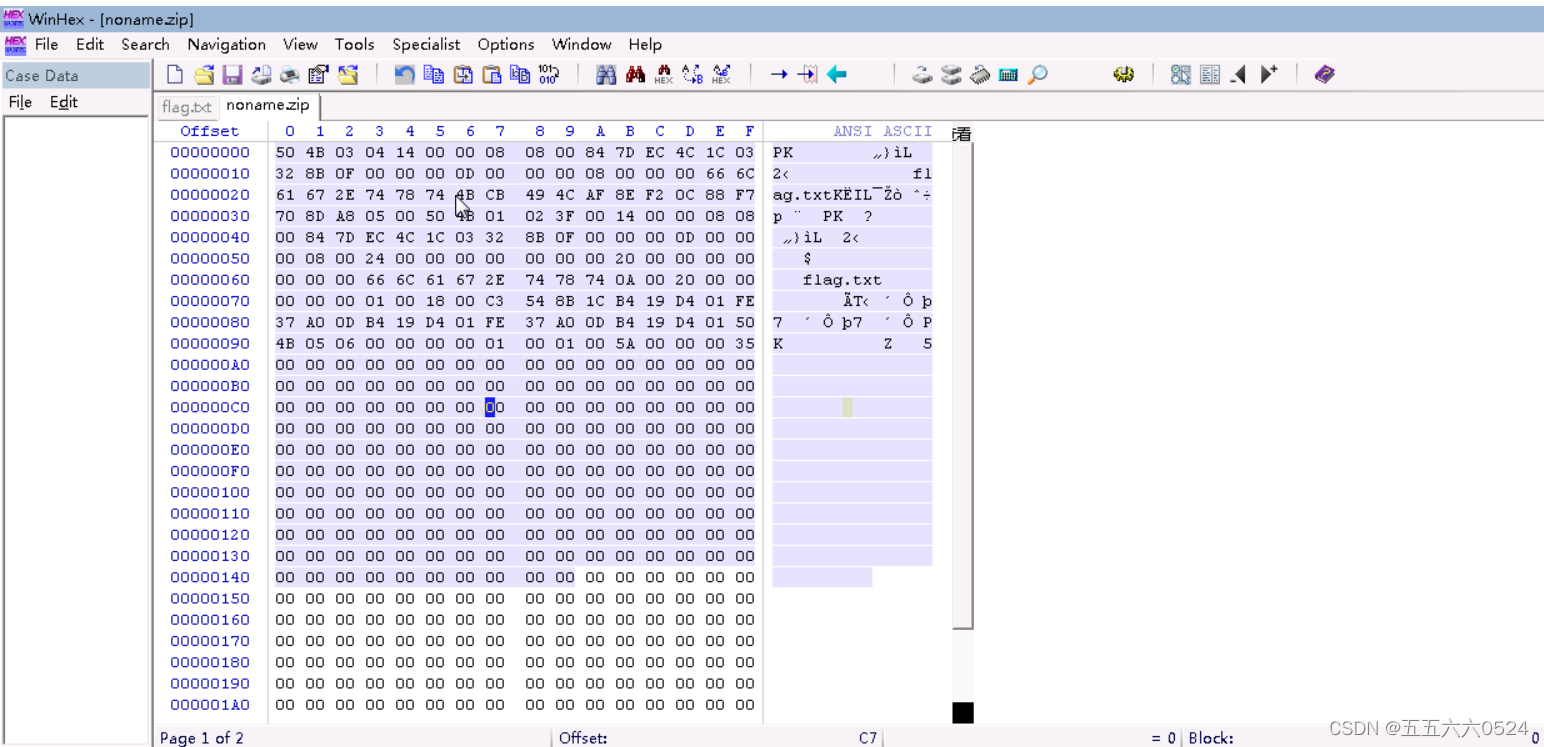
 Look at the file header and you know it's a compressed package , Copy it , use winhex To open the first flag.txt, Get the file size , Create a file of the same size , Paste the hexadecimal numbers on it , And save it as zip Format to open
Look at the file header and you know it's a compressed package , Copy it , use winhex To open the first flag.txt, Get the file size , Create a file of the same size , Paste the hexadecimal numbers on it , And save it as zip Format to open
2、 Steganograph the compressed package in the picture , test method :1、kail Under the binwalk,2、 use winhex After opening , Found to have flag.txt A hint of , And there are zip The file header of
 Separation method :1.linux Of foremost Tools ,2. Change the suffix directly , Change to zip,3.stegslove Tools
Separation method :1.linux Of foremost Tools ,2. Change the suffix directly , Change to zip,3.stegslove Tools
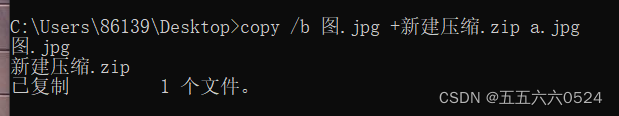
How to hide the compressed package in the picture ?
answer : Use copy Command is enough , As shown in the figure below
3、zip encryption : Code explosion , There are also passwords in the comments or in the details of attributes
4、zip Pseudo encryption
principle : Pseudo encryption is to modify the encryption flag bit of the directory area , Make what was not encrypted ZIP file , When decompressing , The user needs to enter a password to decompress , But the password doesn't exist .
We use the same compressed file without encryption 、 Pseudo encryption 、 Three forms of true encryption are compared , Pictured , The red box is the encryption flag bit of the data area , The green box is the encryption flag bit of the directory area . From the comparison in the figure, we can know , Really encrypted ZIP file , Both encryption flag bits should indicate encryption ( Generally, the first digit is an odd number, which can be expressed as encryption ), Unencrypted ZIP file , Both flag bits indicate that there is no encryption , The pseudo encryption only indicates the encryption flag bit of the directory area as encryption .

Judgment method : use winhex After opening, look at the compression method of the data area and directory area
resolvent : Change the odd number of directory area to even number
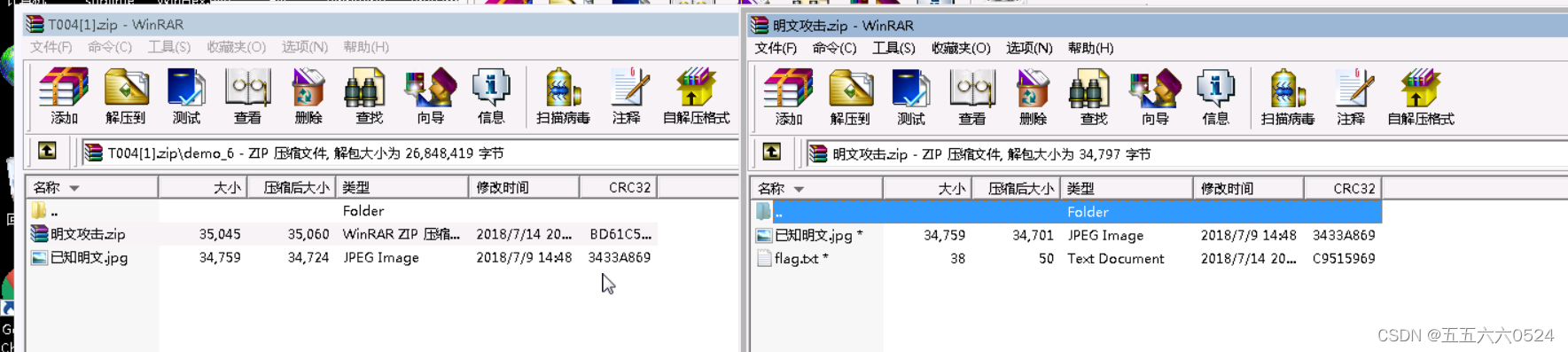
5、 Plaintext attack
The general principle is when you don't know a zip Password , But you have zip A known file in ( The file size should be larger than 12Byte) when , Because the same zip All files in the compressed package are encrypted with the same encryption key , So you can use known files to find the encryption key , Use the key to unlock other encrypted files .
Generally, the author gives you a compressed package and a clear text file , You compress the plaintext file and compare it with the encrypted file , Compare them CRC32 value , If the same , Can carry out plaintext attack
6、CRC Collision (zip)
# -*- coding:utf-8 -*-
import zipfile
import string
import binascii
# Construct character set , Because the title refers to base64 character string , So use upper and lower case letters + Numbers +‘+/=’
dic = string.ascii_letters + string.digits + '+/='
# Specific collision CRC Function of
def CrackCRC32(crc_str):
# Take out the characters from the character set in turn to form a four digit string for collision
for i in dic:
for j in dic:
for p in dic:
for q in dic:
s = i + j + p + q
'''
stay Python 2.x In the version of the ,binascii.crc32 Calculated
CRC The value range is [-2^31,2^31-1] Signed integers between , In order to be with
commonly CRC Compare the results , You need to convert it to an unsigned integer , So add
& 0xffffffff To switch . If it is Python 3.x Version of , Its
The calculation result is [0, 2^32-1] Unsigned integer between , Therefore, there is no need to add
On & 0xffffffff .
'''
if crc_str == (binascii.crc32(s) & 0xffffffff):
print "Cracking Successfuly"
# After the collision is successful, write the contents of the collision to flag.txt In file
flag.write(s)
return
# choice ZIP Functions of files
def CrackZIP():
for i in range(1,5):
file = str(i) + ".zip"
# Get the file in the compressed package CRC32 value
f = zipfile.ZipFile(file,'r')
GetCRC32 = f.getinfo(str(i) + ".txt")
crc_str = GetCRC32.CRC
print "Cracking........" + file
CrackCRC32(crc_str)
flag = open('flag.txt','wb')
CrackZIP()
flag.closeCRC Collision (png)
#coding=utf-8
import zlib
import struct
# Reading documents
file = '1.png' # Be careful ,1.png The picture should be in the same folder as the script ~
fr = open(file,'rb').read()
data = bytearray(fr[12:29])
crc32key = eval(str(fr[29:33]).replace('\\x','').replace("b'",'0x').replace("'",''))
#crc32key = 0xCBD6DF8A # Fill up 0x,copy hex value
#data = bytearray(b'\x49\x48\x44\x52\x00\x00\x01\xF4\x00\x00\x01\xF1\x08\x06\x00\x00\x00') #hex Next copy grep hex
n = 4095 # Theoretically 0xffffffff, But considering the reality of the screen ,0x0fff It's almost there
for w in range(n):# Height and width burst together
width = bytearray(struct.pack('>i', w))#q by 8 byte ,i by 4 byte ,h by 2 byte
for h in range(n):
height = bytearray(struct.pack('>i', h))
for x in range(4):
data[x+4] = width[x]
data[x+8] = height[x]
#print(data)
crc32result = zlib.crc32(data)
if crc32result == crc32key:
print(width,height)
# Writing documents
newpic = bytearray(fr)
for x in range(4):
newpic[x+16] = width[x]
newpic[x+20] = height[x]
fw = open(file+'.png','wb')# Save copy
fw.write(newpic)
fw.close7、 File repair
Generally, the file header is abnormal “504B0304”, Just change it back
8、 Redundant information splicing
Multiple compressed packages , use winhex After opening, I found... At the end 3 Extra bytes , Put these extra bytes together , Decrypt it flag, Here's the picture

2022.1.6 Update the second time
Today, I added the content of last night , Learning is based on binwalk Realize file extraction , Use binwalk command , Stuck in the beginning kali Configuration of virtual machine , I've measured it before , Lots of tutorials , In the end, it didn't come true
2022.1.9 Update for the third time
Follow the tutorial to the official website , Configuration after downloading , Or not iso, Can't configure , Or there's a problem , I really don't understand , Later, brush to a direct decompression to open .vmx A tutorial for , succeed , Its initial account and password are kali

About Stegsolve: This is a jar package , No installation required , Need to be in java Operation in environment , Have to configure java Environmental Science , then win+R,cmd,“java -jar” This command adds Stegsolve.jar The absolute path to the associated file ( This method can open stegslove), Remember to adjust the opening mode , Otherwise, I can't call you all the time , You can only enter commands over and over again


java -jar +jar The absolute path of the file can be opened jar file
2022.1.10 Update for the fourth time
About stegsolve Specific use of , The boss made it clear stegsolve Usage method - cat47 - Blog Garden
Next, open the way to brush questions
2021.1.15
About steganography , More in The use of common steganography tools _z4yn:) The blog of -CSDN Blog _ Steganography tools
1、steghide
Usage examples :
take secret.txt The file is hidden in text.jpg in :
# steghide embed -cf test.jpg -ef secret.txt -p 123456from text.jpg figure out secret.txt:
#steghide extract -sf test.jpg -p 123456
2、F5 Steganography
install :git clone https://github.com/matthewgao/F5-steganography
Decrypt :java Extract / The absolute path of the picture [-p password ] [-e The output file ]
3、zsteg, To quote Steganography tools zsteg install + Use the tutorial _Amherstieae The blog of -CSDN Blog _zsteg
(1) see lsb data
zsteg xxx.bmp
zsteg xxx.png
zsteg -a ( file name ) # Check the of each channel lsb
(2) testing zlib#-b The number of digits is from 1 At the beginning
zsteg zlib.bmp -b 1 -o xy -v(3) Extract the picture of the channel
zsteg -e b8,a,lsb,xy file .png -> out.png
4、outgess Steganography (2022.2.3 to update )
install :sudo apt install outguess
Extract the hidden content when there is a key :eg:outgess -k 'abc' -r mmm.jpg flag.txt
2022.1.27
Dynamic graph decomposition GIF Dynamic picture decomposition , Multi frame dynamic image is decomposed into multiple static pictures _ Picture tool web version
strings + file name , View the string in the file
QR code 、 Bar code identification Barcode Reader. Free Online Web Application、 Forage QR code decoder
python Decompile python Decompile - Online tools
linux When you delete a file, you delete the file name , The data is still stored on the hard disk , Recovery extundelete command ,
install :sudo apt-get install extundelete application :extundelete file name --restore-allcommand :openssl rsautl -decrypt -in key.txt -inkey pub.key -out flag.txt
-in For the encrypted document to be decrypted -inkey As the key -out For the output documentFor details, see How to use OpenSSL Encrypt and decrypt files _petpig0312 The blog of -CSDN Blog _openssl Encrypt file
Blasting tools ARCHPR
Mask : Already know the character of a certain position in the password
The mask defaults to :?
for example : Mask as :www.?????.com The range is lowercase a-z
from www.aaaaa.com Run to www.zzzzz.com
file + file name Check the nature of the file
Extract files from traffic packets :1、tcpxtract -f + file name 2、 use NetworkMiner 3、 use wireshark 4、foremost -v -i + file name 5、 use Chaosreader
2022.2.3 to update
1、 Tools exiftool, Pictures can be collected exif Information ,binwalk I can see "TIFF" Usually use him , At the same time, in the attribute - There will also be something in the notes
install :apt-get install exiftool
Use :exiftool + file name
2、 Tools stegdetect, Used to detect jpg Whether the type of picture hides other files or content , You can check what kind of steganography
apt-get install stegdetect, This method failed
Other methods have not been found yet
2022.2.8 to update
NTFS Exchange data streams
BUU-MISC- I have a Mario _TzZzEZ-web The blog of -CSDN Blog
NTFS Exchange data streams ( abbreviation ADS) yes NTFS A feature of disk format , stay NTFS Under the file system , Each file can have multiple data streams , In addition to the primary file stream, there can be many non primary file streams hosted in the primary file stream , And we can't see the non main file data stream , Because the folder size always shows 0
Parasitic one :
echo Write content >> Host file : Exchange data stream files ( Parasitic files )
echo ever>>1.txt:2.txt
2.txt by echo Create an exchange data stream file ,ever stay 2.txt inParasitic two :
type Exchange data stream files ( Parasitic files )>> Host folder : Exchange data stream files ( Parasitic files )
type 2.txt>>temp:2.txt
temp Empty folder , After execution 2.txt Parasitic in temp folder
type a.jpg>>temp:a.jpg
temp Empty folder , After execution a.jpg Parasitic in temp foldersee :
notepad Host file : Exchange data stream files ( Parasitic files )
notepad 1.txt:2.txtView picture files :
mspaint Host file : Exchange data stream files ( Parasitic files )
notepad a.jpg:b.jpgMore references NTFS Application of exchange data stream steganography - _chesky - Blog Garden
utilize NTFS Exchange data stream hidden files | QingSword.COM
2022.3.4
base64 To hexadecimal :base64 library ,base64.b64decode() function
AES encryption -AES Decrypt - On-line AES Encryption and decryption tools
Exclusive or operation XOR encryption / Decrypt - A toolbox - All the easy-to-use online tools are here !
Key signal (PT224X) = Synchronous boot code (8bit) + Address bit (20bit) + Data bits (4bit) + Stop code (1bit)
2022.3.17
Virginia code explosion ( Does not provide key)Vigenere Solver - www.guballa.de
uncompyle6 It's a native python Cross Version decompiler and fragment Decompiler , yes decompyle、uncompyle、uncompyle2 Waiting for your replacement .
uncompyle6 Can be python The bytecode is converted back to the equivalent python Source code
install :pip install uncompyle6
Decompile using :uncompyle6 -o . pyc file name
版权声明
本文为[Five five six six 0524]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230628471807.html
边栏推荐
- VBA calls SAP RFC to read & write data
- CTF攻防世界刷题51-
- Houdini>刚体, 刚体破碎RBD
- 从零开始完整学习机器学习和深度学习,包括理论和代码实现,主要用到scikit和MXNet,还有一些实践(kaggle上的)
- MySQL in window10 version does not work after setting remote access permission
- Read and modify the JSON file under the resource folder
- Internal network security attack and defense: a practical guide to penetration testing (IV): Authority improvement analysis and defense
- Interview learning route
- Protobuf use
- Automatically fit single line text into the target rectangle
猜你喜欢

When using flash, the code ends automatically without an error, the connection cannot be maintained, and the URL cannot be accessed.

The projection vector of a vector to a plane

Online Safe Trajectory Generation For Quadrotors Using Fast Marching Method and Bernstein Basis Poly

ABAP ALV显示金额与导出金额不一致

Dictionary & lt; T1,T2> Sorting problem

内网渗透系列:内网隧道之dnscat2

BUUCTF MISC刷题

Research on software security based on NLP (I)

SQL sorts string numbers

Buctf MISC brossage
随机推荐
Série de pénétration Intranet: icmpsh du tunnel Intranet
SAP self created table log function is enabled
Post of experience in preparation for guarantee and research -- the 18th (2021) Central South planning department promoted the exemption to Zhejiang University Institute of Technology
CTF攻防世界刷题51-
Chapter V investment real estate
About USB flash drive data prompt raw, need to format, data recovery notes
內網滲透系列:內網隧道之icmpsh
Plane definition - plane equation
一些靶场的学习记录:sqli-labs、upload-labs、XSS
关于unity获取真实地理地图转3D化的相关链接
面试学习路线
Houdini地形与流体解算(模拟泥石流)
内网渗透系列:内网隧道之dns2tcp
Houdini > rigid body, rigid body breaking RBD
Houdini fluid > > particle fluid export to unity note
STO With Billing 跨公司库存转储退货
Apache Hudi 如何加速传统的批处理模式?
《内网安全攻防:渗透测试实战指南》读书笔记(七):跨域攻击分析及防御
Solve the problem of deploying mysql8 in docker with correct password but unable to log in to MySQL
Research on software security based on NLP (I)