当前位置:网站首页>What if the server is poisoned? How does the server prevent virus intrusion?
What if the server is poisoned? How does the server prevent virus intrusion?
2022-04-23 15:34:00 【IDC02_ FEIYA】
How does the server prevent virus intrusion ?
- Scheme 1 : Use a strong login password , Avoid weak password , And change the password regularly
- Option two : Enforce password policy through group policy , Stop when the number of errors reaches a certain number
- Option three : Turn off unnecessary ports
- Option four : Use 360 Safety guard “ Black proof reinforcement ” Turn off file sharing 、admin$ Manage sharing 、 Remote service, etc
- Summary
As a The server Administrators , You should know the harmfulness of server poisoning and how to deal with it after server poisoning , First, install anti-virus software , Antivirus in safe mode . At ordinary times, we should pay attention to strengthening the awareness of anti-virus , Do a good job of prevention in advance, such as : Update virus library , Kill virus regularly , Update patches regularly 、 Back up data regularly .
Today, Feifei mainly shares with you several solutions to strengthen server security , I hope I can help you ~
Scheme 1 : Use a strong login password , Avoid weak password , And change the password regularly
1、 High strength password :8 Above position , Use capital letters + Lowercase + Numbers + Symbol ( give an example :CWidc02@!#¥@)
2、 Do not use weak passwords : As the name suggests, weak password means that there is no strict and accurate definition , It is generally believed that passwords that are easy to be guessed by others or cracked by cracking tools are weak passwords ( give an example :123456;abcdefg;admin)
3、 Change password regularly : The normal system login password needs to be in 3-6 Change the password once a month
4、 In addition, if there are multiple servers in the organization, you must not use the same password , In this way, if one server falls, other servers will also be poisoned
5、 Try not to open DMZ Host or desktop mapping function , Avoid computers IP Burst and leak on the public network
Option two : Enforce password policy through group policy , Stop when the number of errors reaches a certain number
1、win+r Turn on run , Input gpedit.msc
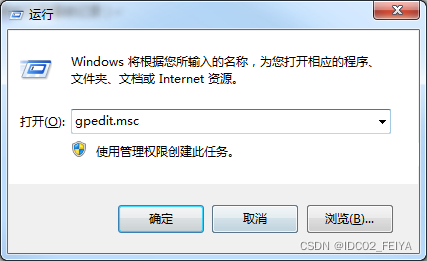
2、 Computer settings —Windows Set up — Security Settings — Account Strategy — Account locking strategy ”, Then go to... In the right pane “ Account lock threshold ” term , The number of failed login attempts of the user can be set here , The value is 0 To 999 Between , The default is 0 Indicates that the number of logins is unlimited , We can change it to 3 or 10.( After setting up , You can also set the time of account locking )
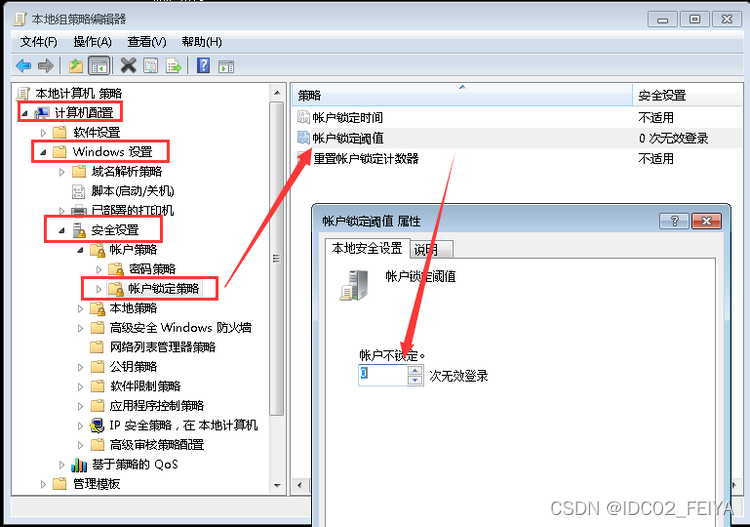
3、 Note after modification : When the number of times a user tries to log in to the system and enters the wrong password reaches a certain threshold, the account will be locked automatically , Before the account lock expires , This user will not be able to use , Unless the administrator manually unlocks .
Option three : Turn off unnecessary ports
Such as :445、135,139 etc. , Yes 3389 The port can be configured with a white list , Only those in the white list are allowed ip Connection landing
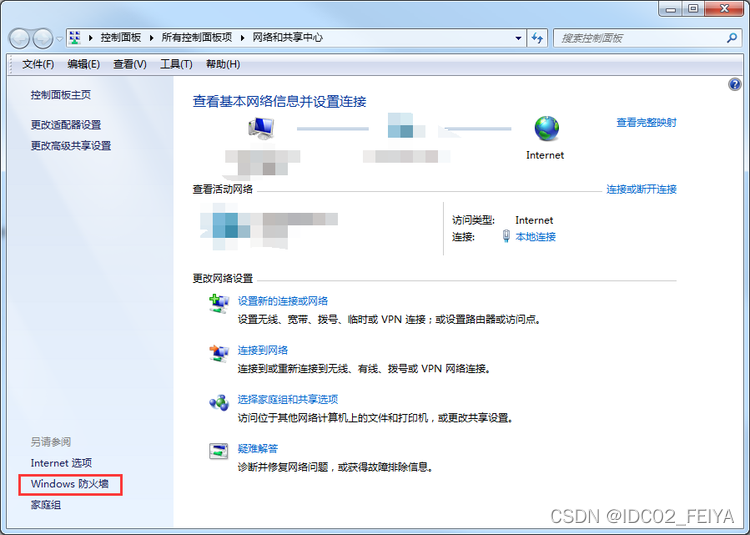
1、 First, right-click the taskbar network icon , choice “ Open the network and Sharing Center ” Click in the lower left corner of the network and sharing center “Windows A firewall ”
2、 stay Windows Click... In the firewall “ Advanced settings ”, Click on the top left corner “ Inbound rules ”, Then select the new rule in the upper right corner
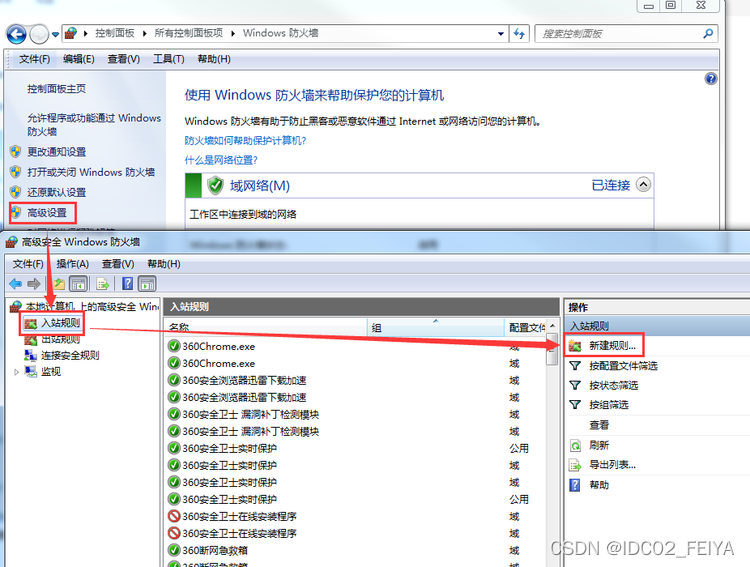
3、 Rule type click port , Select next
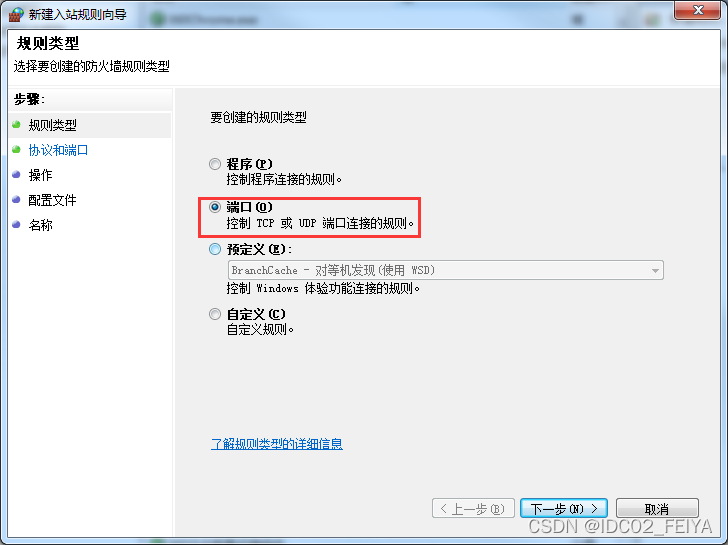
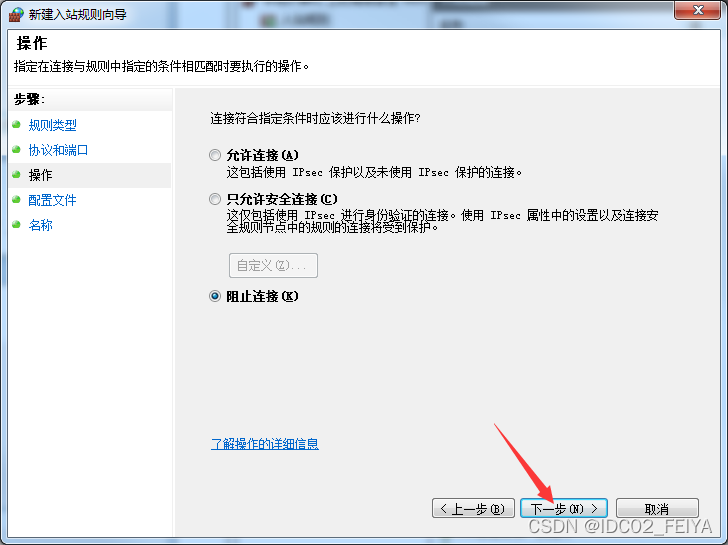
4、 stay “ Specific local port ” Input in “445”, Click to go to the next step , Then select... In the operation “ Block connection ”, Click to go to the next step
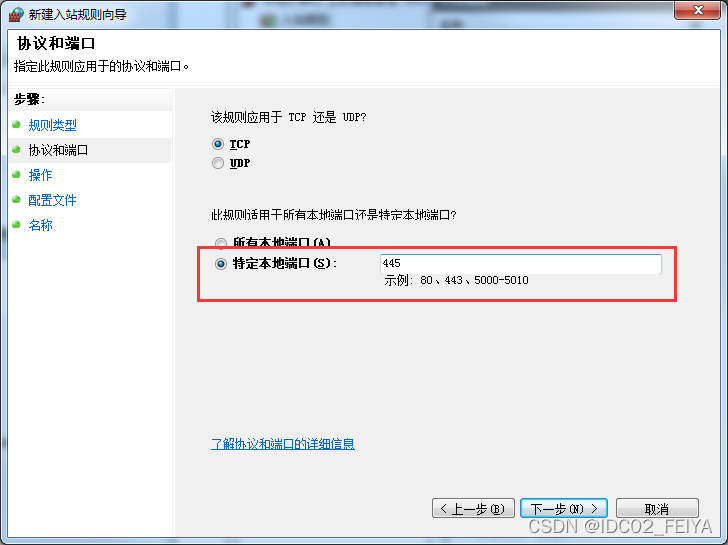
5、 Click to go to the next step , Click Finish to finish the 445 Port closure , Similarly, other ports can be disabled in the same way
Option four : Use 360 Safety guard “ Black proof reinforcement ” Turn off file sharing 、admin$ Manage sharing 、 Remote service, etc
1、 open 360 The security guard searches at the top right “ Black proof reinforcement ” Open this tool
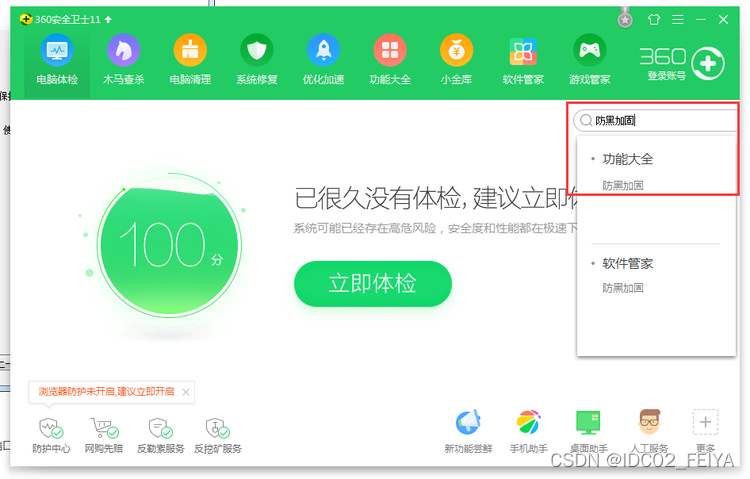
2、 Prompt detection after opening , Click on “ Detect immediately ”
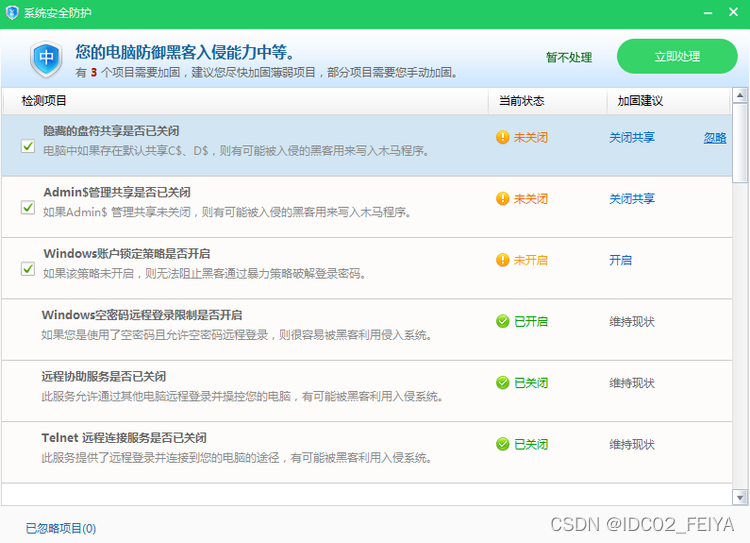
3、 The inspection results will prompt relevant reinforcement suggestions , Follow the recommendations , Can effectively protect against attack
Summary
Through the above four methods , Can effectively protect the server from remote attacks , If you are worried that your computer or the company's computer will be attacked, then quickly set the protection manually according to the above methods
版权声明
本文为[IDC02_ FEIYA]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204231526479336.html
边栏推荐
- Have you really learned the operation of sequence table?
- 函数(第一部分)
- 码住收藏▏软件测试报告模板范文来了
- Deeply learn the skills of parameter adjustment
- fatal error: torch/extension.h: No such file or directory
- Connectez PHP à MySQL via aodbc
- PSYNC synchronization of redis source code analysis
- Crawling fragment of a button style on a website
- 考试考试自用
- Explanation of redis database (III) redis data type
猜你喜欢
Tun equipment principle

TLS / SSL protocol details (30) RSA, DHE, ecdhe and ecdh processes and differences in SSL
setcontext getcontext makecontext swapcontext
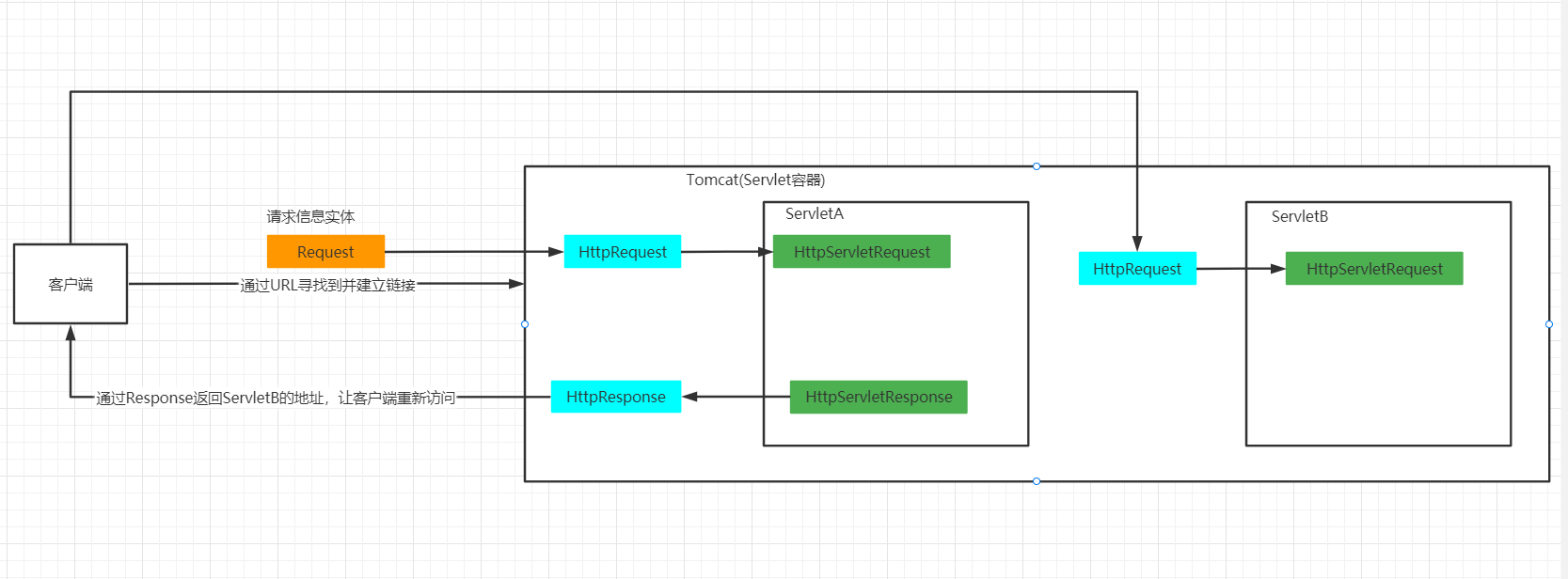
重定向和请求转发详解

移动金融(自用)
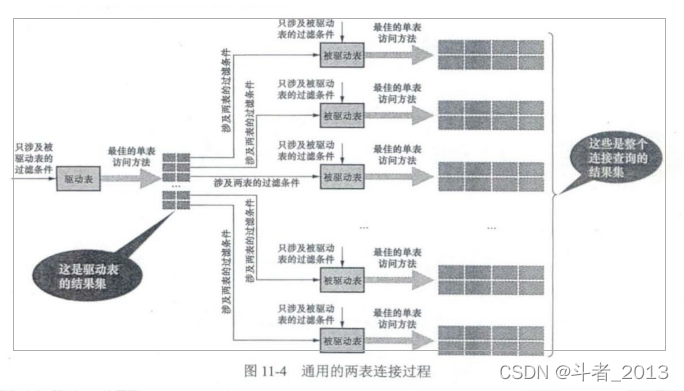
Mysql连接查询详解
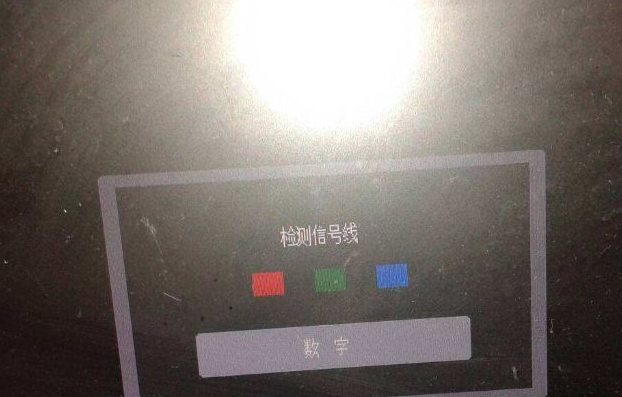
电脑怎么重装系统后显示器没有信号了
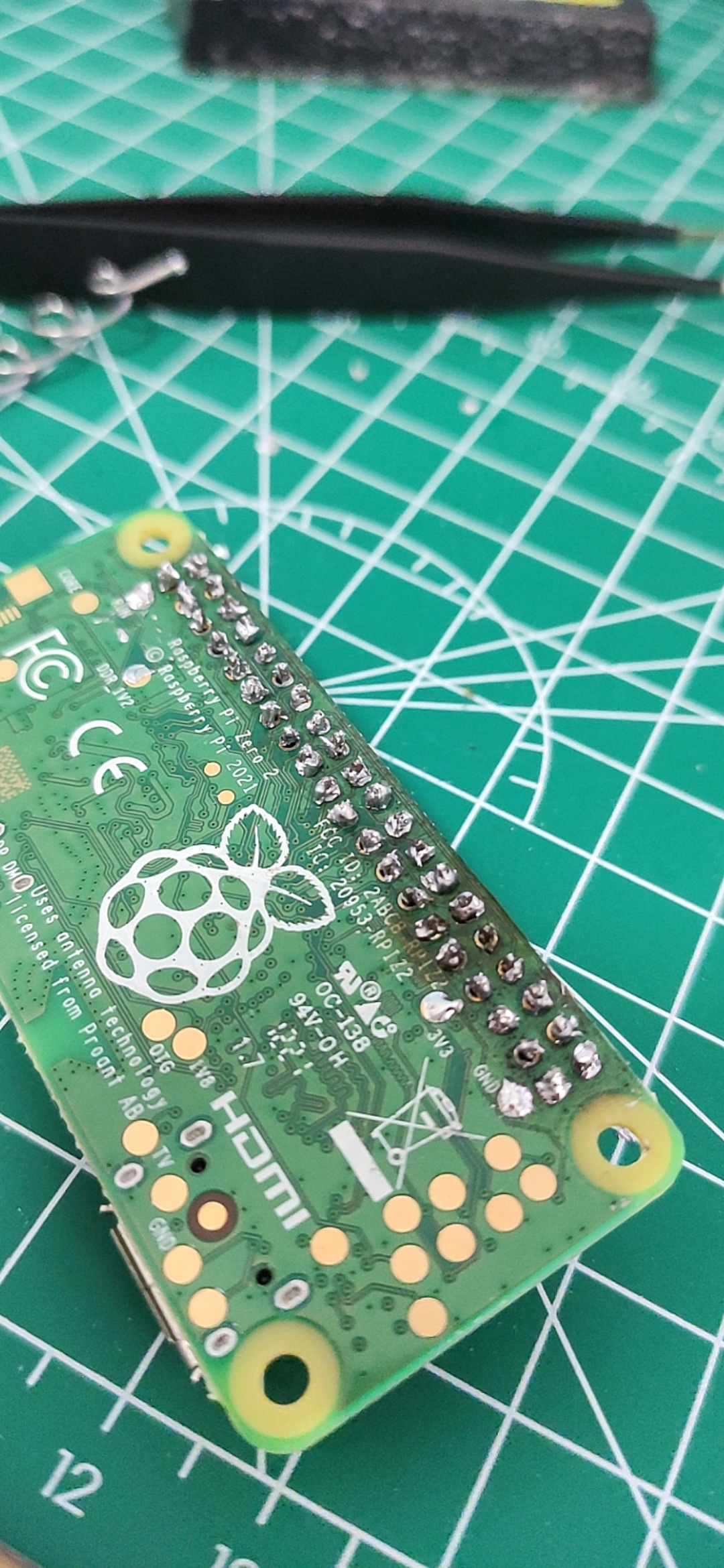
我的树莓派 Raspberry Pi Zero 2W 折腾笔记,记录一些遇到的问题和解决办法
Krpano panorama vtour folder and tour
API gateway / API gateway (II) - use of Kong - load balancing
随机推荐
Nacos程序连接MySQL8.0+ NullPointerException
如果conda找不到想要安装的库怎么办PackagesNotFoundError: The following packages are not available from current
Connect PHP to MSSQL via PDO ODBC
Common types of automated testing framework ▏ automated testing is handed over to software evaluation institutions
Squid agent
MultiTimer v2 重构版本 | 一款可无限扩展的软件定时器
控制结构(二)
Leetcode学习计划之动态规划入门day3(198,213,740)
setcontext getcontext makecontext swapcontext
What is CNAs certification? What are the software evaluation centers recognized by CNAs?
Reptile exercises (1)
Advantages, disadvantages and selection of activation function
Multitimer V2 reconstruction version | an infinitely scalable software timer
网站压测工具Apache-ab,webbench,Apache-Jemeter
Today's sleep quality record 76 points
Three uses of kprobe
cadence SPB17.4 - Active Class and Subclass
C language super complete learning route (collection allows you to avoid detours)
编译,连接 -- 笔记
MySQL query library size