当前位置:网站首页>Huawei router clock near the drainage experiment (using stream strategy)
Huawei router clock near the drainage experiment (using stream strategy)
2022-08-10 21:26:00 【Lay Master Wen Tao】
Router bypass experiment.
The purpose of the experiment, as shown in the figure, this experiment needs to draw the traffic from the address 10.1.2.1 to the side-mounted AR1 device when accessing two PCs, and then the AR1 device will be injected back to the AR3equipment.
The method of drainage can be used flexibly according to the specific environment. This experiment adopts the method of flow strategy.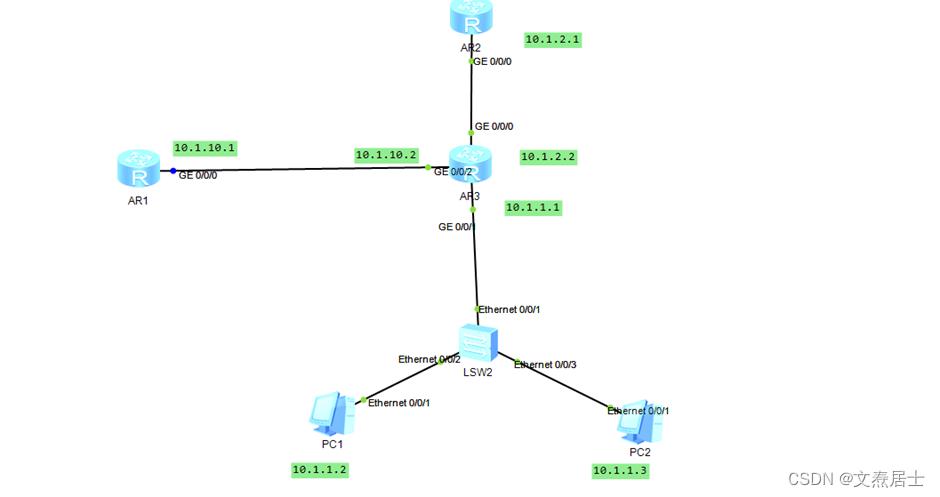
Specific configuration:
AR1:
interface GigabitEthernet0/0/0ip address 10.1.2.1 255.255.255.0ip route-static 0.0.0.0 10.1.2.2AR2:
interface GigabitEthernet0/0/0ip address 10.1.10.1 255.255.255.0ip route-static 10.1.1.0 24 10.1.10.2ip route-static 10.2.1.0 24 10.1.10.2It is also possible to use a default route for the connected device.AR2:
traffic classifier c1 operator or Create a traffic classifier to match traffic characteristics.The or guess here should be similar to the OR operation in programming, which is used to specify how to match the flow classification.(corrections are welcome)if-match anytraffic behavior b1 Creates a flow behavior that changes the direction of data flow.redirect ip-nexthop 10.1.10.1traffic policy p1 Creates a traffic policy and associates the created traffic classification with traffic behavior.classifier c1 behavior b1interface GigabitEthernet0/0/0ip address 10.1.2.2 255.255.255.0traffic-policy p1 inbound Finally, you need to apply this policy to the interface, paying attention to the direction.AR2 device address planning is as follows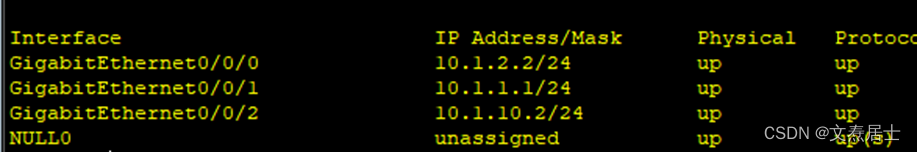
Finally, twoThe address and gateway are configured on a PC and it is OK.
Verification:
Use the device of 10.1.2.1 to ping two PCs, and perform packet capture verification on the interface of the connected device.
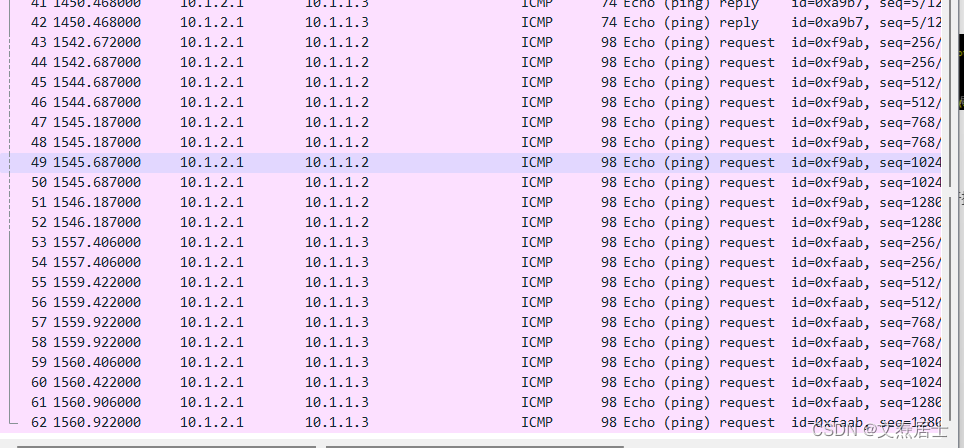
It can be seen that the drainage strategy is successful, and the device is attachedThe packet was successfully captured on the interface.
When the packet is returned, the data does not pass through the bypass device.If you want the return packet to also pass through the side-connected device, you should also need a flow strategy.
边栏推荐
猜你喜欢
随机推荐
npm WARN config global `--global`, `--local` are deprecated. Use `--location=global` instead.
突破次元壁垒,让身边的玩偶手办在屏幕上动起来!
扩展中国剩余定理
数据标注太昂贵?这个方法可以用有限的数据训练模型实现基于文本的ReID!
直播课堂系统08-腾讯云对象存储和课程分类管理
win7开机有画面进系统黑屏怎么办
参天生长大模型:昇腾AI如何强壮模型开发与创新之根?
关于 NFT 版权保护的争议
设备管理中数据聚类处理
将视图模型转换为使用 Hilt 依赖注入
Auto.js中APP应用相关指令
ArcMap创建镶嵌数据集、导入栅格图像并修改像元数值显示范围
快消品行业经销商协同系统:实现经销商可视化管理,提高沟通执行效率
labelme-屏蔽拖拽的事件
日期选择器组件(限制年份 设定仅展示的月份)
Introduction to PostgreSQL
Go程序员进化史
论配置化系统的配置
ansible各个模块的详解和使用
ctfshow-osint