当前位置:网站首页>Implementation principle of instanceof
Implementation principle of instanceof
2022-04-23 08:05:00 【Pen drawing Acacia】
function instanceOf(left, right) {
let leftValue = left.__proto__;
let rightValue = right.prototype;
while (true) {
if (leftValue === null) {
return false;
}
if (leftValue === rightValue) {
return true;
}
leftValue = leftValue.__proto__;
}
}
版权声明
本文为[Pen drawing Acacia]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230624332681.html
边栏推荐
- Interview learning route
- Talk about the essence of interface idempotent and consumption idempotent
- FUEL: Fast UAV Exploration using Incremental Frontier Structure and Hierarchical Planning
- yum源仓库本地搭建的两种方法
- Export all SVG files in the specified path into pictures in PNG format (thumbnail or original size)
- How does Apache Hudi accelerate traditional batch mode?
- Anti shake and throttling
- C # control the camera, rotate and drag the observation script (similar to scenes observation mode)
- 以下程序实现从字符串str中删除第i个字符开始的连续n个字
- BUUCTF MISC刷題
猜你喜欢

Intranet penetration series: ICMP of Intranet tunnel_ Tran
![[programming practice / embedded competition] learning record of embedded competition (II): picture streaming based on TCP](/img/6c/7408180d0c24560b4a68982635520e.jpg)
[programming practice / embedded competition] learning record of embedded competition (II): picture streaming based on TCP

内网渗透系列:内网隧道之icmp_tran
![[NLP notes] preliminary study on CRF principle](/img/8c/2717aeee2e75bdae97d2bacd362e53.png)
[NLP notes] preliminary study on CRF principle
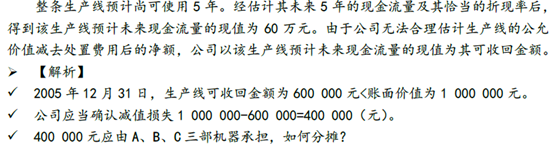
Chapter VII asset impairment

云计算技能大赛 -- openstack私有云环境 第一部分
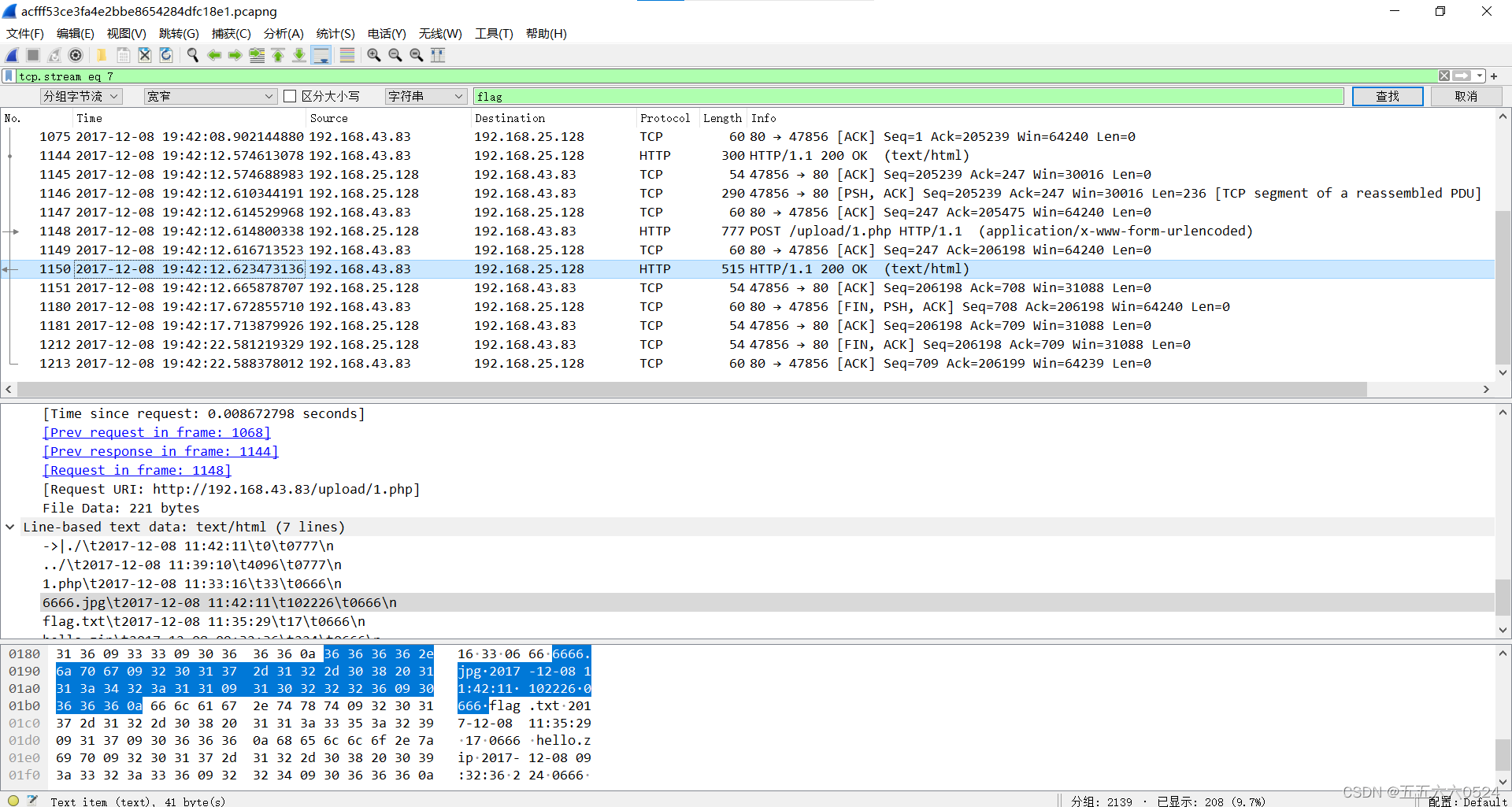
攻防世界MISC刷题1-50

国基北盛-openstack-容器云-环境搭建

巨头押注的全屋智能,正在驱动海信、华为、小米们「自我革命」

Feign source code analysis
随机推荐
《内网安全攻防:渗透测试实战指南》读书笔记(四):权限提升分析及防御
惨了,搞坏了领导的机密文件,吐血分享备份文件的代码技巧
CTF-MISC总结
Move layout (Flex layout, viewport label)
Buctf MISC brossage
Internal network security attack and defense: a practical guide to penetration testing (VII): cross domain attack analysis and defense
Ctf-misc summary
学fpga(从verilog到hls)
内网渗透系列:内网隧道之icmpsh
LeetCode15. 三数之和
数据库之MySQL——基本常用查询命令
Complete color conversion formulas and conversion tables (31 kinds)
Intranet security attack and defense: a practical guide to penetration testing (6): domain controller security
输入 “ net start mysql ”,出现 “ 发生系统错误 5。 拒绝访问 ” 。问题详解
Internal network security attack and defense: a practical guide to penetration testing (5): analysis and defense of horizontal movement in the domain
Talk about the essence of interface idempotent and consumption idempotent
三星,再次“西征”
Export all SVG files in the specified path into pictures in PNG format (thumbnail or original size)
CTF attack and defense world brush questions 51-
Cloud computing skills competition -- the first part of openstack private cloud environment