当前位置:网站首页>Phishing for NFT
Phishing for NFT
2022-04-23 04:31:00 【chinadefi】
in the light of NFT Phishing


Fishing mail
Attackers exploit various hotspots (NFT Open to booking 、 Wallet upgrade 、 Airdrop claim 、 Contract upgrade 、 Project change website 、 special NFT) etc. , Send official websites containing elaborate imitations 、 Pre sale platform 、app Download links and other phishing emails .
Example :OpenSea
Description of the incident : according to OpenSea The official reply to , This is a hacker upgrading OpenSea Initiated at the time of the contract .OpenSea Co founder and CEO Devin Finzer On twitter , The attacker stole the value 170 Million dollars of Ethereum .
Attack methods
The attacker uses the formal upgrade contract time node to send a contract upgrade success email to all users . Many users are uncertain about the source of the email . Many users don't determine the source of the email , Can't control your wallet , Which leads to the theft of the wallet .
Social media related phishing
Multiple NFT project
- Attacker’s wallet address
- BAYC
- Doodles
- Nyoki
- Shamanz
- Zooverse
- Dreadfuls
- Freaky Labs
- Kaijukingz
- Maison Ghost
- MekaVerse
- The Heart Project
- Monkey Kindom
- Fractal
- Phantom Galaxies
- Axie Infinity
- Cryptovoxel
Attack methods
- Attackers gain access to project members Discord account .
- The attacker used the account of the project party to publish a new announcement on the channel , The content of the announcement is a fake official website created by the attacker , And announce that some things can be purchased exclusively .
- Victims visit websites , Click the link , And try to buy . After authorization ,ETH Will be transferred to the attacker's wallet .
- The attacker joins a new discord Account or impersonate the victim's account , And say you're a liar , And say you're a liar , Then put your id To the server . The server prohibits the victim's account .
- The attacker requires remote desktop or screen sharing to show your innocence , They will let you Ctrl+Shirt+I View console , stay discord The console will display the authentication pass .
- Once you get a pass , An attacker can take over the account .
- because NFT Characteristics , Some trading platforms , Such as sudoswap、Nfttrader Will encourage users to trade privately NFT.
- The attacker will generate a transaction confirmation platform . After confirmation by both parties , Smart contracts will be executed automatically .
- In the process of communication , The attacker will negotiate with the victim in exchange for these NFT. When a transaction occurs , The attacker suggested modifying the data , Then send a fraud link to the victim .
- After confirmation by both parties , In the purse NFT Will be transferred to the attacker's wallet .
- The attacker took advantage of discord The server sends private messages to members of different communities in batches , Or cheat by pretending to be an administrator to solve the problem .
- Take the private key of the wallet , Or send a fake phishing website , Say you can get... For free NFT. Once the user authorizes the fake website , In the account NFT Will be stolen .
- In some mature NFT In the project , After the collection was released for some time , Announce that the attacker will make similar collections and use the official website in discord Send purchase links on websites such as communities , When the real NFT Not online , They will first search for... With similar names NFT, Some attackers will create several transactions in advance . In order to save the Commission of the platform and the project party , There will be private transactions between community members , At this time, users often ignore NFT Authenticity .
The project involved in the scam
- REALSWAK
- NFTflow
- Mercenary
- Blockverse
- Frosties
- Bored Bunny
- Evolved Apes
- Iconics
- Banksy
Suggest
- Do not click on any links or attachments in suspicious emails . If you receive suspicious email from your organization , And doubt whether the email is legal , Please open the web browser , And open a new tab . Then click from your saved favorites or search through the Internet to the organization's website .
- If the suspicious information seems to come from someone you know , By other means ( Such as text messages or phone calls ) Contact this person to confirm .
- Do not use your computer to log in to email in public places 、 Using instant messaging software 、 Online banking or other activities involving sensitive information . Without being sure of its safety , Connect WiFi Please do not log in and send or receive email after , Pay attention to using free WiFi. Due to management negligence , Some people with ulterior motives use data interception and monitoring methods to obtain user information .
- Don't send sensitive information to the Internet , The information and data published by users on the Internet may be collected by attackers . By analyzing this information and data , Send targeted phishing emails to users .
- If the email requires downloading attachments or installing some software , Please judge carefully .
- For asking for a password through a social media platform 、 Verification Code 、2fa People who , Identify yourself carefully , Judge whether it is forged for others 、 Whether the account is stolen, etc .
- Regularly change the frequently used account password 、 Increase complexity 、 Multi step verification, etc .
Source:https://medium.com/coinmonks/nft-phishing-96aa6488ae7e
About
ChinaDeFi - ChinaDeFi.com It's a research driven DeFi Innovation organizations , We are also a blockchain development team . From all over the world every day 500 Close to a good source of information 900 In the content , Looking for deeper thinking 、 Sort out more systematic content , Provide decision-making assistant materials to the Chinese market at the fastest speed .
Layer 2 friends sharing same hobby - Welcome to Layer 2 Interested blockchain technology enthusiasts 、 Study and analyze people and Gavin( WeChat : chinadefi) contact , Discuss together Layer 2 Landing opportunities . Please pay attention to our official account of WeChat “ Decentralized financial community ”.

版权声明
本文为[chinadefi]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230426454641.html
边栏推荐
- QT program integration easyplayer RTSP streaming media player screen flicker what is the reason?
- Introduction to Cortex-M3 register set, assembly language and C language interface
- Supplément: annotation
- 【李宏毅2022 机器学习春】hw6_GAN(不懂..)
- VHDL语言实现32位二进制数转BCD码
- 第四章 --- 了解标准设备文件、过滤器和管道
- 1个需求的一生,团队协作在云效钉钉小程序上可以这么玩
- STM32 MCU ADC rule group multi-channel conversion DMA mode
- [echart] Introduction to echart
- 优麒麟 22.04 LTS 版本正式发布 | UKUI 3.1开启全新体验
猜你喜欢

Set classic topics

兼容NSR20F30NXT5G的小体积肖特基二极管

A function second kill 2sum 3sum 4sum problem

Bridge between ischemic stroke and intestinal flora: short chain fatty acids

Single chip microcomputer serial port data processing (2) -- ucosiii + cyclic queue receiving data

优麒麟 22.04 LTS 版本正式发布 | UKUI 3.1开启全新体验

Network principle | connection management mechanism in TCP / IP important protocol and core mechanism
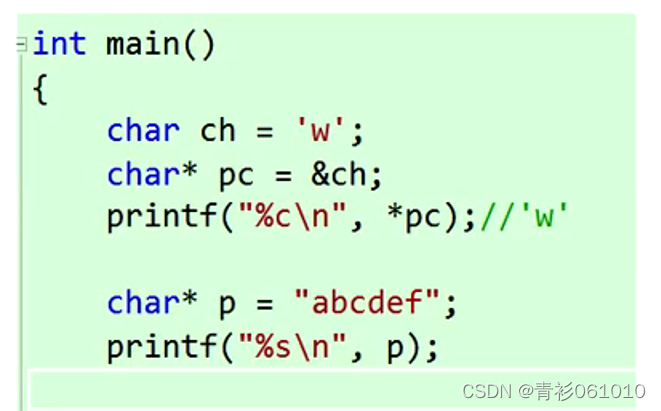
C语言: 指针的进阶
![[BIM introduction practice] Revit building wall: detailed picture and text explanation of structure, envelope and lamination](/img/cb/86b5898609800a80592fceb782503f.png)
[BIM introduction practice] Revit building wall: detailed picture and text explanation of structure, envelope and lamination
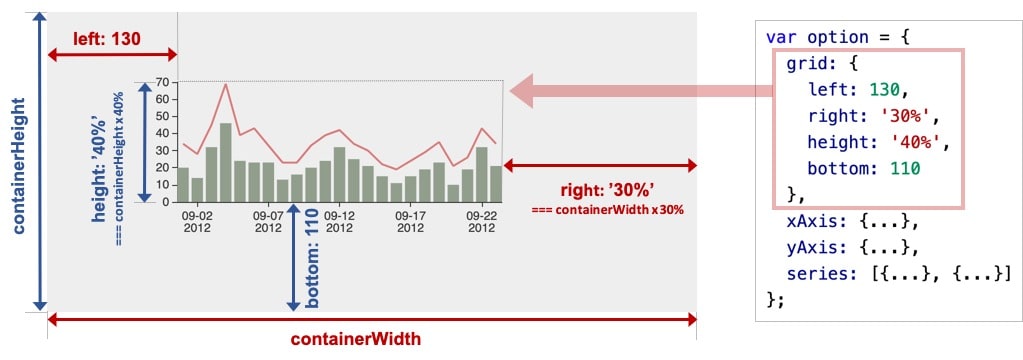
【Echart】echart 入门
随机推荐
Interaction of diet gut microbiota on cardiovascular disease
STM32单片机ADC规则组多通道转换-DMA模式
Network principle | connection management mechanism in TCP / IP important protocol and core mechanism
Leetcode->1 两数之和
【时序】基于 TCN 的用于序列建模的通用卷积和循环网络的经验评估
洛谷P1858 【多人背包】 (背包求前k优解)
[echart] Introduction to echart
Chapter 4 - understanding standard equipment documents, filters and pipelines
Kotlin. The binary version of its metadata is 1.6.0, expected version is 1.1.15.
【Pytorch基础】torch.split()用法
Chlamydia infection -- causes, symptoms, treatment and Prevention
matlab讀取多張fig圖然後合並為一張圖(子圖的形式)
C语言常用字符串处理函数
Bridge between ischemic stroke and intestinal flora: short chain fatty acids
創下國產手機在海外市場銷量最高紀錄的小米,重新關注國內市場
中国移动日赚2.85亿很高?其实是5G难带来更多利润,那么钱去哪里了?
Mysql---数据读写分离、多实例
補:注解(Annotation)
补:注解(Annotation)
Hard core chip removal