当前位置:网站首页>The R language uses the timeroc package to calculate the multi time AUC value of survival data without competitive risk, and uses the confint function to calculate the confidence interval value of mul
The R language uses the timeroc package to calculate the multi time AUC value of survival data without competitive risk, and uses the confint function to calculate the confidence interval value of mul
2022-04-23 20:09:00 【Data+Science+Insight】
R Language use timeROC The package calculates the survival data without competitive risk for multiple times AUC value 、 Use confint Function to calculate the survival data under the condition of no competitive risk AUC Confidence interval value of index
Catalog
版权声明
本文为[Data+Science+Insight]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204232004476975.html
边栏推荐
- Kubernetes入门到精通-裸机LoadBalence 80 443 端口暴露注意事项
- DTMF dual tone multi frequency signal simulation demonstration system
- C语言的十六进制printf为何输出有时候输出带0xFF有时没有
- Audio editing generation software
- Inject Autowired fields into ordinary beans
- MySQL 进阶 锁 -- MySQL锁概述、MySQL锁的分类:全局锁(数据备份)、表级锁(表共享读锁、表独占写锁、元数据锁、意向锁)、行级锁(行锁、间隙锁、临键锁)
- Kubernetes entry to mastery - bare metal loadbalance 80 443 port exposure precautions
- 波场DAO新物种下场,USDD如何破局稳定币市场?
- NC basic usage
- MySQL数据库 - 数据库和表的基本操作(二)
猜你喜欢
Esp8266 - beginner level Chapter 1
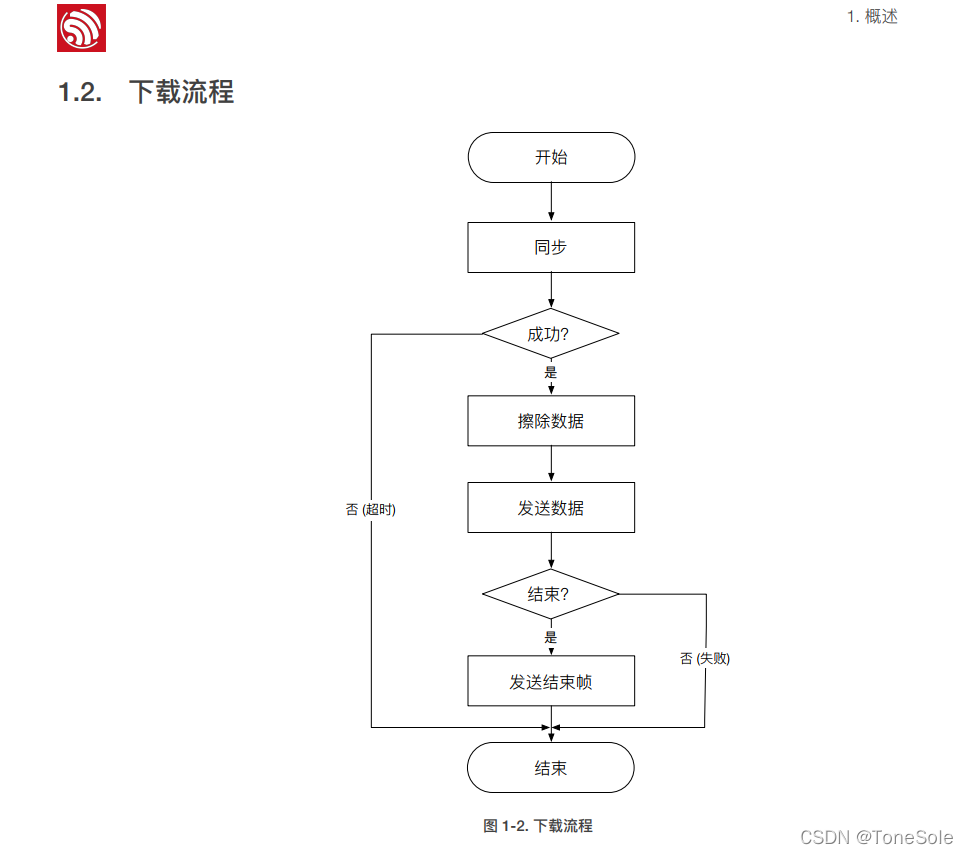
Software College of Shandong University Project Training - Innovation Training - network security shooting range experimental platform (8)
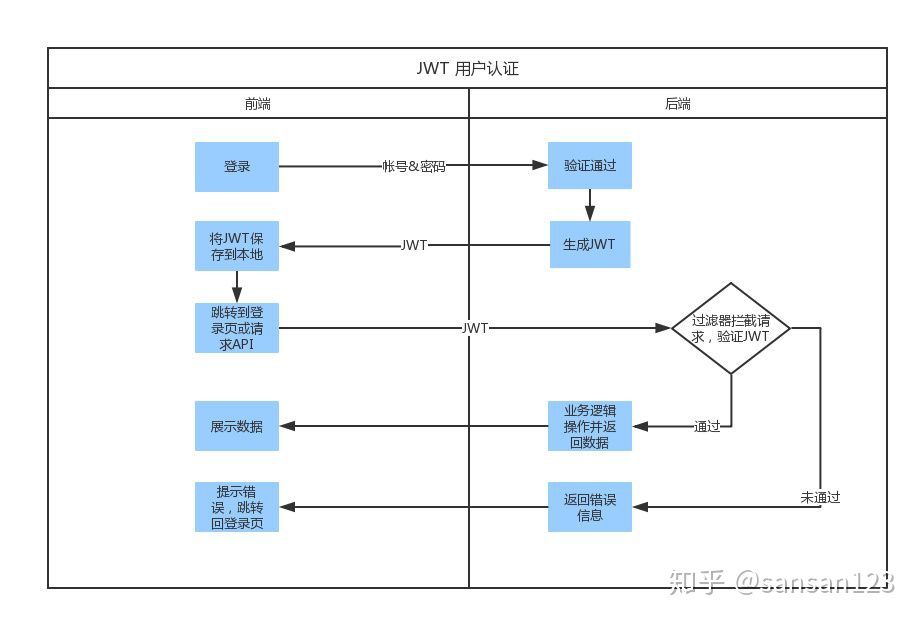
Five minutes to show you what JWT is
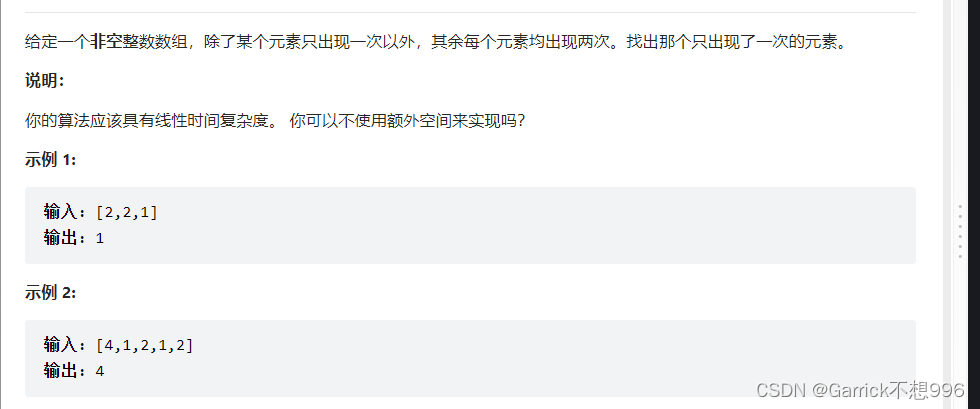
LeetCode异或运算
【文本分类案例】(4) RNN、LSTM 电影评价倾向分类,附TensorFlow完整代码

antd dropdown + modal + textarea导致的textarea光标不可被键盘控制问题

Project training of Software College of Shandong University - Innovation Training - network security shooting range experimental platform (V)
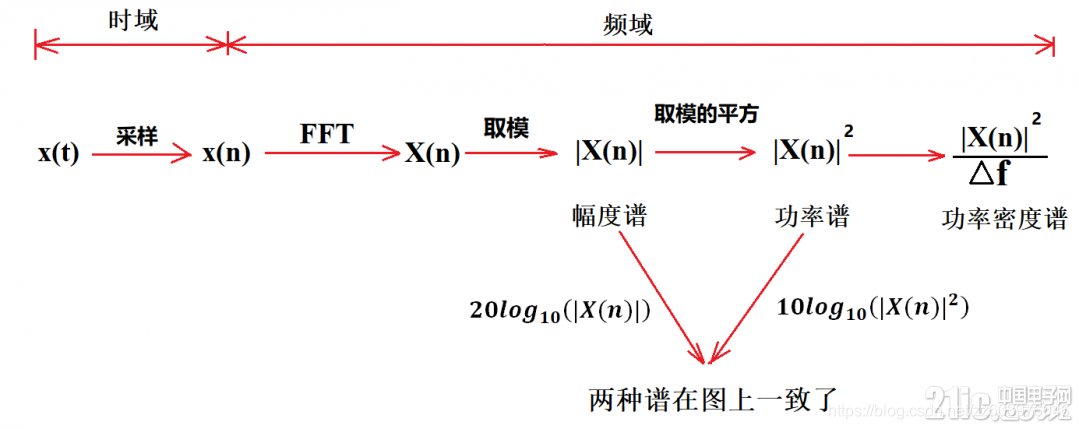
Physical meaning of FFT: 1024 point FFT is 1024 real numbers. The actual input to FFT is 1024 complex numbers (imaginary part is 0), and the output is also 1024 complex numbers. The effective data is
山大网安靶场实验平台项目—个人记录(四)
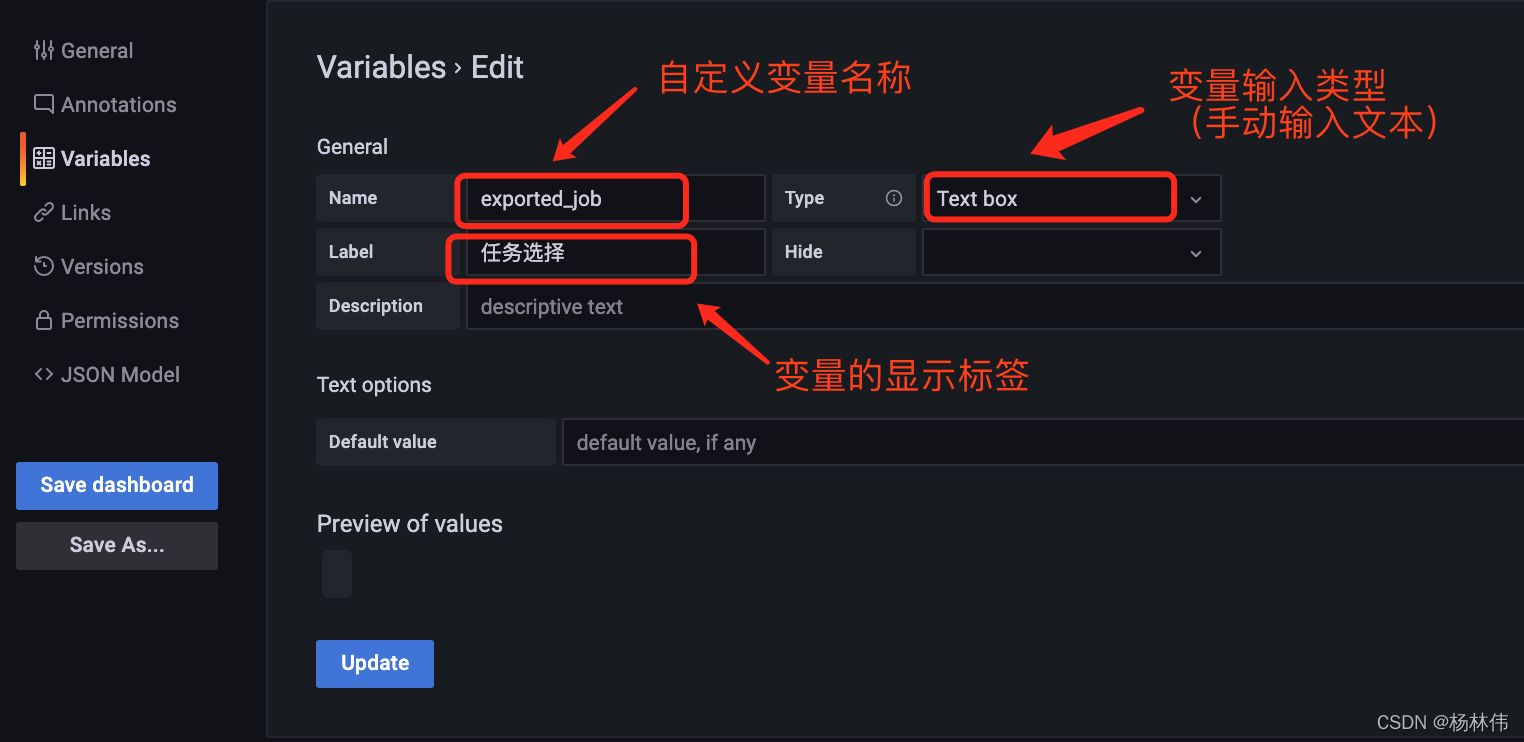
Grafana shares links with variable parameters
随机推荐
Leetcode XOR operation
Redis cache penetration, cache breakdown, cache avalanche
山东大学软件学院项目实训-创新实训-网络安全靶场实验平台(八)
Video understanding
波场DAO新物种下场,USDD如何破局稳定币市场?
NC basic usage 3
山东大学软件学院项目实训-创新实训-网络安全靶场实验平台(五)
Mysql database - single table query (II)
Introduction to electron Tutorial 4 - switching application topics
How to create bep-20 pass on BNB chain
Openharmony open source developer growth plan, looking for new open source forces that change the world!
MFC获取本机IP(网络通讯时用得多)
MySQL数据库 - 连接查询
STM32 Basics
Electron入门教程4 —— 切换应用的主题
Kubernetes入门到精通-在 Kubernetes 上安装 OpenELB
Is the wechat CICC wealth high-end zone safe? How to open an account for securities
中金财富公司怎么样,开户安全吗
视频理解-Video Understanding
山大网安靶场实验平台项目-个人记录(五)