当前位置:网站首页>Redis cache penetration, cache breakdown, cache avalanche
Redis cache penetration, cache breakdown, cache avalanche
2022-04-23 20:07:00 【Handsome that handsome】
Although we are using redis It's very cool when caching , It greatly improves the performance and efficiency of our applications , Especially in data query , We don't need to query data in the persistent database directly , Instead, you can query data in memory
There are always two sides to everything , While using it well , We must also face the problems it brings , It's about data consistency , This problem , It's a matter of weighing the pros and cons , Let's go on
redis When the cache is used with some persistent databases , There will be some high availability problems , Such as :
- Cache penetration
- Cache breakdown
- Cache avalanche
We can solve the above problems , That solves the problem of high availability of some servers
What is cache penetration
Let's learn some first , On the underlying principles and actual source code analysis , Let's watch it later

Cache penetration , That is, the user wants to query a data , stay redis Can't find , That is, no hits in the cache , Then it will be directly de persistent mysql Query in , There is no such data , Then this query fails
When there are many users , The query cache did not find , Then all these are to query the persistent mysql database , All the pressure hit mysql above , This is cache penetration
The solutions are generally 2 Ways of planting
- Using the bloon filter
- Cache empty objects
Using the bloon filter
A bloom filter is a data structure , For all possible query parameters, use hash How to store , It will be verified at the control layer first , If it doesn't fit , Then discard , This avoids the pressure on the underlying storage system

Bloom filters are deployed in redis In front of , To intercept data , Reduce to redis The impact of , Thus reducing the impact on Impact of persistence layer
Cache empty objects
Caching empty objects , That is, when we do not query the data we expect in the persistent database , Then an empty object is returned , And cache the empty object , Then set an expiration time
When there is a request to access this object later , The cache can directly access the empty object , This protects the persistent data layer , Reduce the impact pressure on him

By caching empty objects as described above , It seems to solve the problem , But use lasts , Will find key Values correspond to more and more empty objects , There will be the following 2 A question
- Very many empty objects are cached , Then there are many corresponding key Occupy Memory space , Occupancy resources , Memory pressure rises sharply
- If the expiration time of an empty object is up , Then the pressure of the request will still hit the persistent database , This will affect the consistency of data business
What is cache breakdown

Cache breakdown occurs when the amount of data is too large , Or the cache has expired
When a key At the moment of expiration , There are a lot of requests for this key The data of , This kind of data is hot data , Because at the moment when the cache expires , The request will also access the persistent database to query the data , And the data will be written to the cache , At this point, it will lead to excessive pressure on the database in an instant , Cause breakdown
It can be understood here that The difference between breakdown and penetration :
breakdown , It's a key Very hot , A lot of interviews are in this key above , stay key The moment of failure , All requests are typed on the database , Just make a hole , Breakdown
Penetration is more about the absence of accessed data , A large number of requests for access are non-existent data
Buffer breakdown solution
- Set hotspot data to not expire , Do not set expiration time , There will be no hot spots key The moment of expiration causes problems
- Plus distributed locks , Guarantee for every key , At the same time, there is only one service to access , Other services did not get the lock , You can't access redis This key, Then you need to wait to get the lock
This way, , The pressure of the lock is very great , visit redis Access the lock first , Equivalent to locking to redis Blocked a layer
What is a cache avalanche

Cache avalanche Is in a certain period of time , Cache set expired , perhaps redis Downtime can occur
for example :
In some hot events , Some goods will be set to expire within a fixed time , So in redis Inside , This fixed point in time , a large number of key Be overdue , This leads to... During this time period Cache failed ,
And a large number of request data are printed on the persistent database , It's hard , Under this pressure peak , The pressure is all on the persistent database , This will cause the persistent database to go down
The above ,key The problem of centralized expiration is not very painful , What hurts most is redis It's down. , Natural periodic peak pressure , Our persistent database can withstand the pressure , It happened to be redis Abnormal downtime , Hang one piece at a time , This is likely to hang up all the persistent databases in the rear , This is a devastating crushing
Cache avalanche solution :
- take redis Make it highly available
build redis colony , Different live , Since I'm worried redis Can hang , Then let's prepare more redis , Make it active and standby , Or live more in a different place - Current limiting the drop
When the cache fails , Restrict the order of accessing data by locking , Or turn off some unimportant Services , Let resources and performance fully provide our main services - Do data preheating
Data preheating is before we officially go online , Let's first access the data we need to access in advance , In this way, a large amount of data to access the database can be written to the cache
In this way, you can manually trigger and load different data before the upcoming high concurrency data access key , And different expiration times will be set , The main thing is to balance the cache invalidation , In this way, try to avoid losing a lot of key Focus on overdue situations
版权声明
本文为[Handsome that handsome]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204210557450646.html
边栏推荐
- How to create bep-20 pass on BNB chain
- R语言ggplot2可视化:ggplot2可视化散点图并使用geom_mark_ellipse函数在数据簇或数据分组的数据点周围添加椭圆进行注释
- Build intelligent garbage classification applet based on Zero
- Inject Autowired fields into ordinary beans
- Shanda Wangan shooting range experimental platform project - personal record (IV)
- 【webrtc】Add x264 encoder for CEF/Chromium
- Grafana 分享带可变参数的链接
- Kubernetes入门到精通-在 Kubernetes 上安装 OpenELB
- LeetCode动态规划训练营(1~5天)
- Openharmony open source developer growth plan, looking for new open source forces that change the world!
猜你喜欢
Project training of Software College of Shandong University - Innovation Training - network security shooting range experimental platform (6)
Grafana shares links with variable parameters
![[webrtc] add x264 encoder for CEF / Chromium](/img/3f/9bf73d6d2aec14ba94dfc6734eb6ac.png)
[webrtc] add x264 encoder for CEF / Chromium

The textarea cursor cannot be controlled by the keyboard due to antd dropdown + modal + textarea
Kubernetes入门到精通-裸机LoadBalence 80 443 端口暴露注意事项
No, some people can't do the National Day avatar applet (you can open the traffic master and earn pocket money)
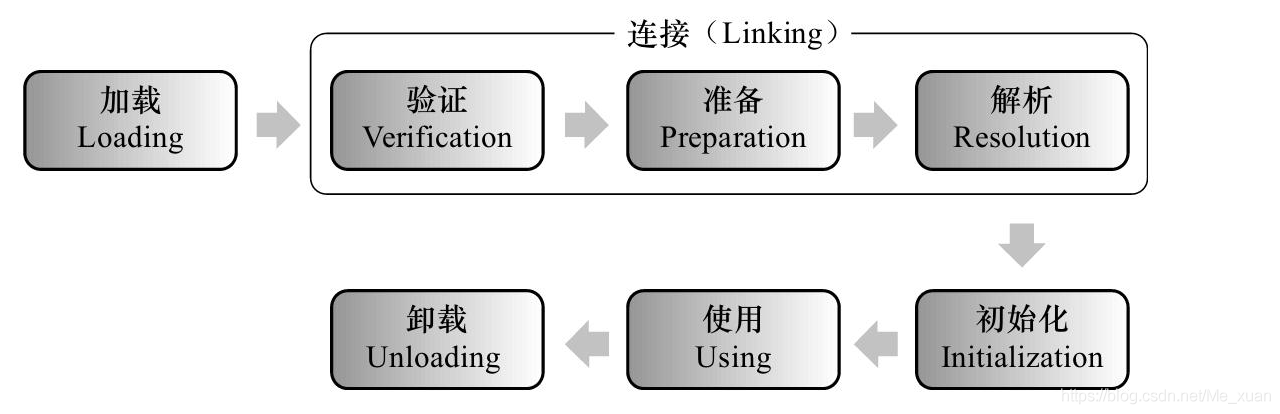
Class loading mechanism
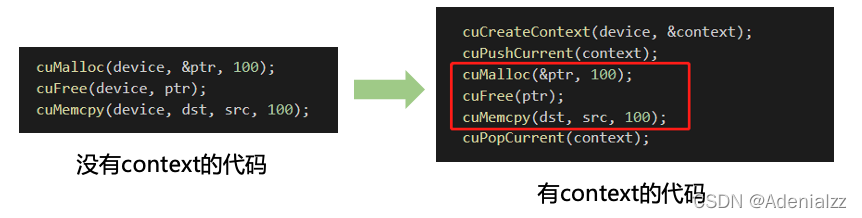
Compact CUDA tutorial - CUDA driver API
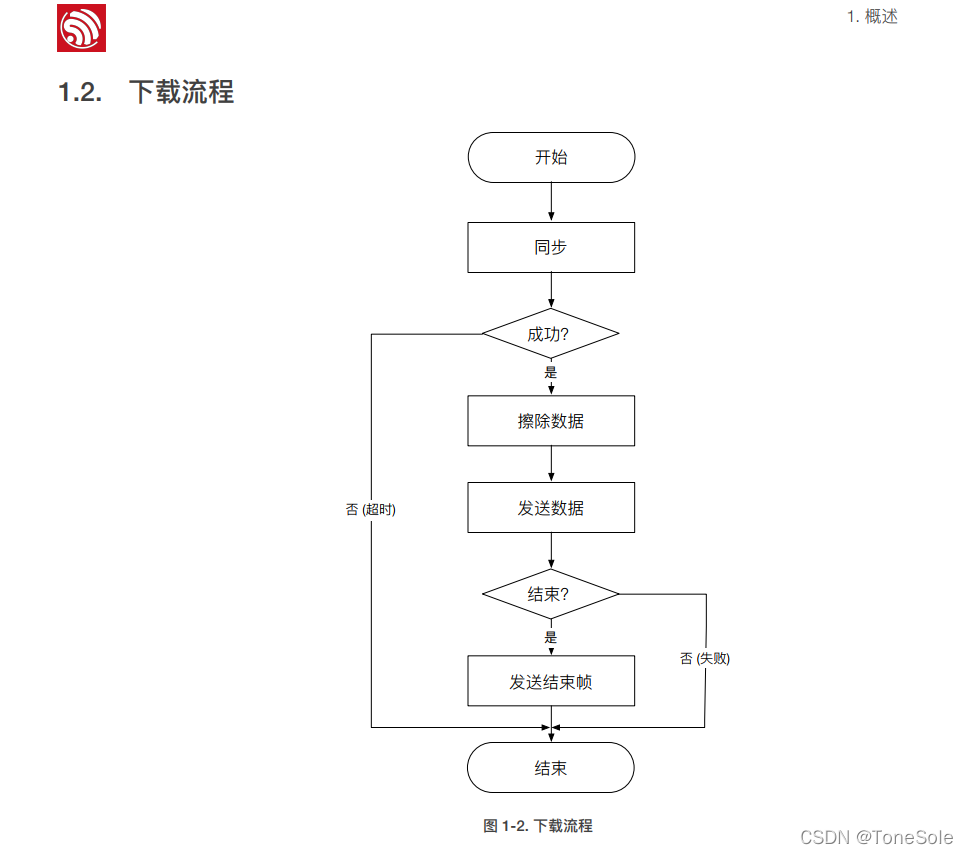
ESP8266-入门第一篇
LeetCode动态规划训练营(1~5天)
随机推荐
[webrtc] add x264 encoder for CEF / Chromium
Kubernetes introduction to mastery - ktconnect (full name: kubernetes toolkit connect) is a small tool based on kubernetes environment to improve the efficiency of local test joint debugging.
使用 WPAD/PAC 和 JScript在win11中进行远程代码执行
aqs的学习
山大网安靶场实验平台项目-个人记录(五)
NC basic usage 1
Kubernetes入门到精通-裸机LoadBalence 80 443 端口暴露注意事项
LeetCode动态规划训练营(1~5天)
How to use go code to compile Pb generated by proto file with protoc Compiler Go file
Video understanding
MySQL advanced lock - overview of MySQL locks and classification of MySQL locks: global lock (data backup), table level lock (table shared read lock, table exclusive write lock, metadata lock and inte
ESP8266-入门第一篇
Golang timer
Kubernetes getting started to proficient - install openelb on kubernetes
仓库管理数据库系统设计
Why is the hexadecimal printf output of C language sometimes with 0xff and sometimes not
【h264】libvlc 老版本的 hevc h264 解析,帧率设定
Fundamentals of programming language (2)
C学习完结
MySQL数据库 - 单表查询(二)