当前位置:网站首页>Construction of middleman environment mitmproxy
Construction of middleman environment mitmproxy
2022-04-23 08:02:00 【Xihang】
List of articles
Requirements and hardware environment
Simulated man in the middle attack :
- mitmproxy Software acts as a middleman agent
- wireshark Capture traffic Check the protocol name and version
- Two sets of Vmware virtual machine , All systems are ubuntu20.04
- Two wireless network cards :
- One for middleman equipment , Turn on hot spots , Do gateway use
- One for the client , Connect hot , Initiate traffic
The network of man in the middle equipment is in bridge mode , You need to turn on the hotspot . When bridging , The host machine ( The real host environment cannot connect to the server that needs authentication WIFI, That is, the campus network of the school WIFI Can't connect , You can connect to... Using password wifi)
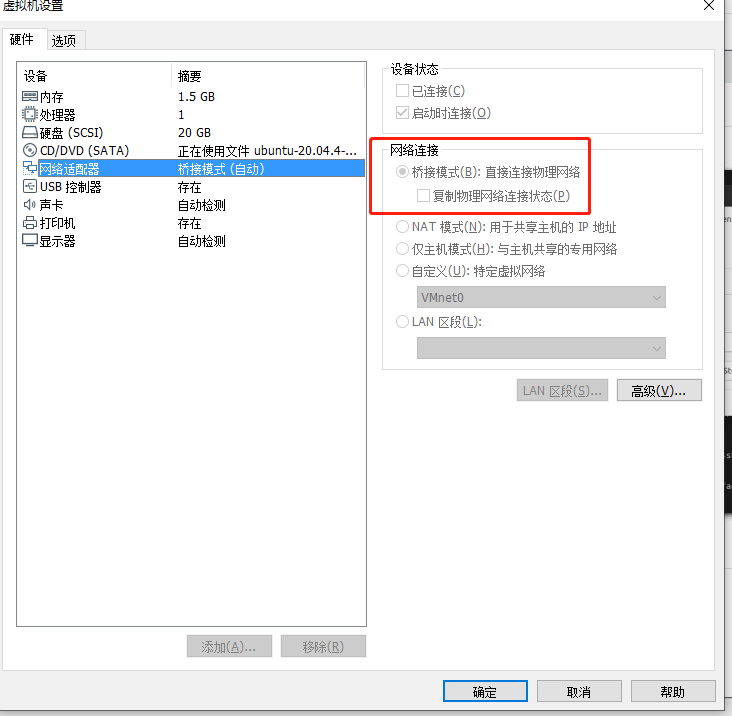
The client network is set to NAT that will do
Configure the wireless network card driver on the client and the middleman
The author's wireless network card is TP-LINK Manufacturer's TL-WN726N Drive free version , But drive free is right windows No drive , stay ubuntu I can't help but drive , Therefore, you need to download the driver .
https://blog.csdn.net/zhou_438/article/details/116297868
Installation driver :
https://github.com/McMCCRU/rtl8188gu
sudo apt-get install git
git clone https://github.com/McMCCRU/rtl8188gu
cd rtl8188gu
make
sudo make install
Plug in the wireless card , Select connect to virtual machine
Middleman end
Verify whether the wireless network card can turn on the hotspot

install AP
https://github.com/lakinduakash/linux-wifi-hotspot
sudo add-apt-repository ppa:lakinduakash/lwh
sudo apt install linux-wifi-hotspot
Turn on hot spots
wihotspot
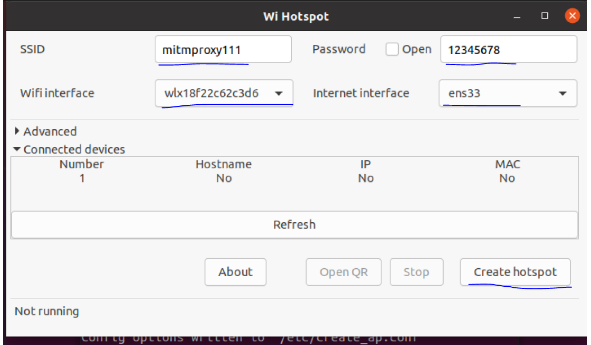
- SSID Is the hotspot name
- password It's a password
- wifiinterface Is the name of the wireless network card
- internet interface Is the normal network card of the virtual machine
- create hotspot Turn on hot spots
install mitmproxy
Middleman equipment
https://blog.csdn.net/qq_39889867/article/details/83477480
Installation dependency
sudo apt-get install openssl
sudo apt-get install libssl-dev
sudo apt-get install libc6-dev gcc openssl
sudo apt-get install -y make build-essential zlib1g-dev libbz2-dev libreadline-dev libsqlite3-dev wget curl llvm tk-dev
sudo apt-get update
install mitmproxy
sudo pip3 install mitmproxy
Use
mitmproxy
( Default port number 8080, Level is equivalent to mitmproxy -p 8080)
Test for successful installation

If you encounter some agents https Failure situation , In the start command mitmproxy -p 8080 Followed by --ssl-insecure Will solve some problems
mitmproxy When reporting a mistake , Check the event log :
from Mitmproxy The console type :console.view.eventlog
mitmproxy Configure transparent agents
Middleman equipment
https://docs.mitmproxy.org/stable/howto-transparent/
sysctl -w net.ipv4.ip_forward=1
sysctl -w net.ipv6.conf.all.forwarding=1
sysctl -w net.ipv4.conf.all.send_redirects=0
iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 80 -j REDIRECT --to-port 8080
iptables -t nat -A PREROUTING -i eth0 -p tcp --dport 443 -j REDIRECT --to-port 8080
ip6tables -t nat -A PREROUTING -i eth0 -p tcp --dport 80 -j REDIRECT --to-port 8080
ip6tables -t nat -A PREROUTING -i eth0 -p tcp --dport 443 -j REDIRECT --to-port 8080
mitmproxy --mode transparent --showhost
eth0 Is the specified network card , After turning on the hotspot , The specified network card should be a wireless network card wlx18f22c620f72
Wireshark
Client installation wireshark
https://www.cnblogs.com/or2-/p/7813446.html
sudo apt-get install libcap2-bin wireshark
sudo chgrp gmz /usr/bin/dumpcap
sudo chmod 750 /usr/bin/dumpcap
sudo setcap cap_net_raw,cap_net_admin+eip /usr/bin/dumpcap
client
Client shutdown NAT network connections , Select hotspot connection
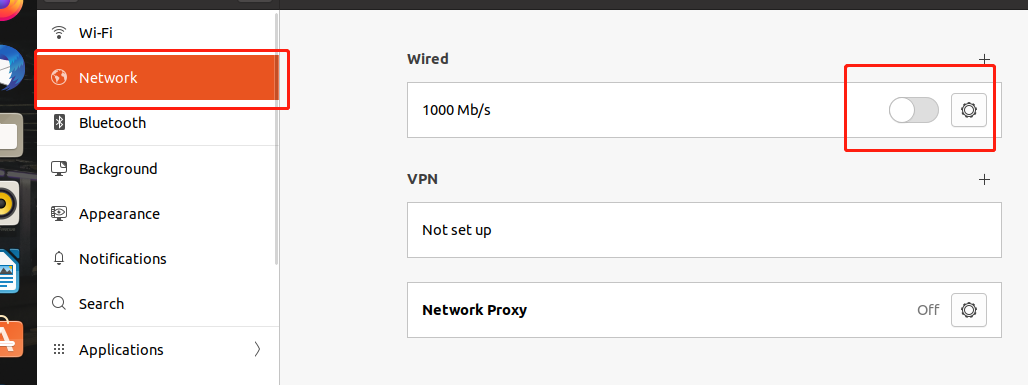


Configure certificate
Middleman end
Two ways :
- Open the browser and type mitm.it, choice linux

sudo mv mitmproxy-ca-cert.pem /usr/local/share/ca-certificates/mitmproxy.crt
sudo update-ca-certificates
The certificate configuration may fail in the above way
- The second way
https://blog.csdn.net/u013091013/article/details/101430260
mitm@ubuntu:~/Desktop$mitmproxy # Run the middleman
mitm@ubuntu:~/Desktop$ cd ~/.mitmproxy/
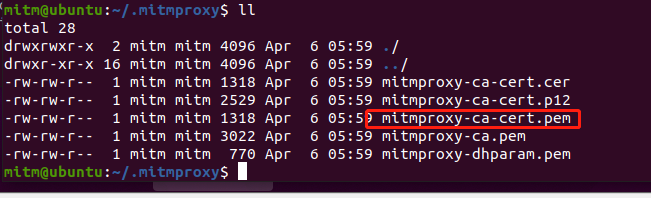
openssl x509 -in mitmproxy-ca-cert.pem -inform PEM -out mitmproxy-ca-cert.crt
sudo mkdir /usr/share/ca-certificates/extra
sudo cp mitmproxy-ca-cert.crt /usr/share/ca-certificates/extra/mitmproxy-ca-cert.crt
sudo dpkg-reconfigure ca-certificates
Just return all the way
ubuntu20.04 The certificate can be added successfully
Test success
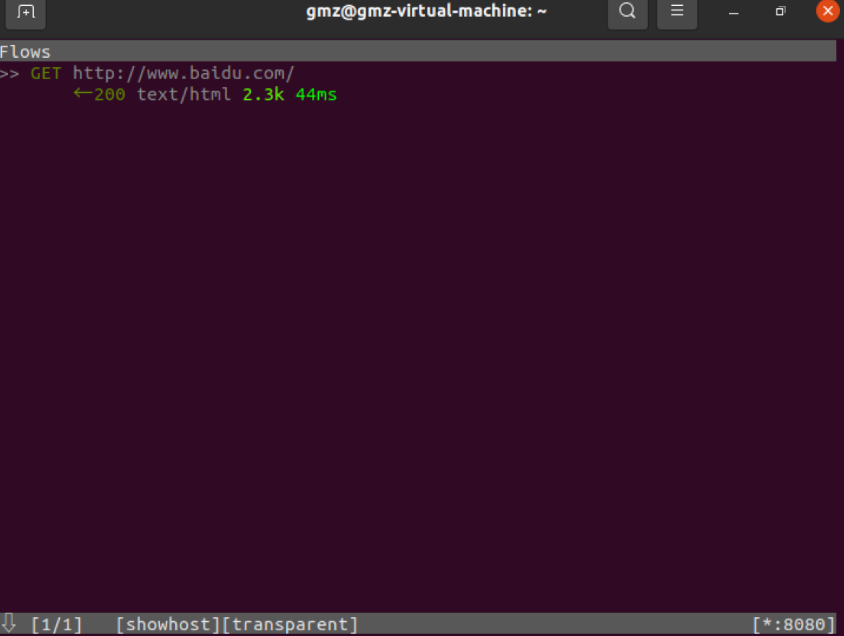
client curl www.baidu.com
The middleman checks to see if
版权声明
本文为[Xihang]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230625153532.html
边栏推荐
- Reptile learning notes, learning reptile, read this article is enough
- KCD_EXCEL_OLE_TO_INT_CONVERT报错SY-subrc = 2
- Houdini fluid > > particle fluid export to unity note
- About USB flash drive data prompt raw, need to format, data recovery notes
- nacos源码分析思路
- SAP Query增强开发介绍
- Unity gets the resources that a file depends on
- Houdini>刚体, 刚体破碎RBD
- Search and replacement of C text file (WinForm)
- IT高薪者所具备的人格魅力
猜你喜欢

Unity获取真实地理地图应用Terrain笔记

Intranet penetration series: dnscat2 of Intranet tunnel

Intranet penetration series: icmpsh of Intranet tunnel
![[unity VFX] Introduction notes of VFX special effects - spark production](/img/bb/a6c637d025dfb8877e6b85e7f39d6b.png)
[unity VFX] Introduction notes of VFX special effects - spark production

Houdini流体>>粒子流体导出到unity笔记

SAP sto with billing process and configuration

【编程实践/嵌入式比赛】嵌入式比赛学习记录(一):TCP服务器和web界面的建立

CTF attack and defense world brush questions 51-

ABAP ALV显示金额与导出金额不一致
Chapter IV intangible assets
随机推荐
CTF-MISC总结
Buctf MISC brossage
VBA调用SAP RFC实现数据读取&写入
Intranet penetration series: icmptunnel of Intranet tunnel (by master dhavalkapil)
Série de pénétration Intranet: icmpsh du tunnel Intranet
《内网安全攻防:渗透测试实战指南》读书笔记(七):跨域攻击分析及防御
Research on system and software security (3)
05 use of array
Personality charm of high paid it workers
Intranet penetration series: icmpsh of Intranet tunnel
Intranet penetration series: dns2tcp of Intranet tunnel
The displayed amount of ABAP ALV is inconsistent with the exported amount
Essays (updated from time to time)
Research on system and software security (2)
sentinel集成nacos动态更新数据原理
攻防世界MISC刷题1-50
The problem of exporting excel form with wireframe and internal spacing of form by using web form
Chapter V investment real estate
云计算技能大赛 -- openstack私有云环境 第一部分
Chapter VII asset impairment