当前位置:网站首页>Introduction to intrusion detection data set
Introduction to intrusion detection data set
2022-04-23 20:31:00 【zjt597778912】
KDDCup 99
- Download url :http://kdd.ics.uci.edu/databases/kddcup99/kddcup99.html
NSL-KDD
- Download url :https://www.unb.ca/cic/datasets/nsl.html
UNSW-NB 15
- Put the official website first :https://research.unsw.edu.au/projects/unsw-nb15-dataset
- Download address :https://cloudstor.aarnet.edu.au/plus/index.php/s/2DhnLGDdEECo4ys
Time :
- Did not find , But no later than 2015 year
background :
- UNSW-NB 15 The original network packets of the data set were generated by the network wide Laboratory of the Australian network security center IXIA PerfectStorm Tool created , It can be used to generate mixed data of modern normal activity and synthetic contemporary attack behavior . Use TCPDUMP Tool capture 100 GB The original flow ( for example ,PCAP file ).
The file is introduced
- contain 2540044 Data records .
- UNSW-NB15_1.csv:700000 strip
- UNSW-NB15_2.csv:700000 strip
- UNSW-NB15_3.csv:700000 strip
- UNSW-NB15_4.csv:440044 strip
- UNSW-NB15_GT.csv: Mark the table correctly (ground truth table)
- UNSW-NB15_LIST_EVENTS.csv: List of events (the list of event file)
- a part of training and testing set:
- UNSW_NB15_training-set.csv:175341 strip
- UNSW_NB15_testing-set.csv:82332 strip
Feature introduction
- Reference resources :https://mathpretty.com/11062.html#UNSW-NB15%E6%80%BB%E4%BD%93%E4%BB%8B%E7%BB%8D
- common 49 Features
Label Introduction
- ditto
Extended information
- The official website consists of references to the dataset .
- Github Summary of this dataset on :https://github.com/topics/unsw-nb15
- Do a good job in data processing ( Did data preprocessing ):https://github.com/InitRoot/UNSW_NB15
- Use SVM and Naive Bayes Come on UNSW-NB15 To deal with :https://github.com/Nir-J/ML-Projects
Kyoto
- Put the official website first :http://www.takakura.com/Kyoto_data/
- Download address :
Time :
background :
The file is introduced
Feature introduction
Label Introduction
Extended information
WSN-DS
- Put the official website first :
- Download address :
Time :
background :
The file is introduced
Feature introduction
Label Introduction
Extended information
CICIDS 2017
- Put the official website first :https://www.unb.ca/cic/datasets/ids-2017.html
- Download address :
Time :
background :
The file is introduced
Feature introduction
Label Introduction
Extended information
CIDDS
- Put the official website first :https://www.hs-coburg.de/index.php?id=927
- Download address :
Time :
background :
The file is introduced
Feature introduction
Label Introduction
Extended information
Dataset set
- Reference resources https://blog.csdn.net/Naristilia/article/details/103900130
- From the data set compiled by the Canadian Institute of network security :https://www.unb.ca/cic/datasets/index.html
- Data mining and network security resource network :http://users.cis.fiu.edu/~lpeng/
- [ Intrusion detection ] DARPA Intrusion detection data set
- [ Intrusion detection ] KDD Cup 99 Data sets
- [ Intrusion detection ] NSL-KDD Data sets
- [ Hacker attack data set ] Honeynet Data sets ( The data set includes data from 2000 year 4 Month to 2011 year 2 month , Cumulative 11 Months Snort Alarm data , About every month 60-3000 multiple Snort Alarm records , Its network consists of 8 individual IP Address through ISDN Connect to ISP)
- [ Log data ] Challenge 2013 Data sets ( Provides a two-week running log of the internal network of a fictitious multinational company , Log types include 3 Kind of , Network traffic Netflow Log data and Big Brother Network health and status data , Logs include : First of all 、 Two week Netflow and Big Brother journal , Intrusion prevention system log data for the second week , Through log analysis, we can find out the anomalies in the network , The network contains about hosts and servers 1100 platform , The number of original logs is close to 10 GB, Number of records exceeds 9000 Line ten thousand )
- Malware data set
- Vizsec:https://vizsec.org/data/
- At home 360Netlab:http://blog.netlab.360.com/tag/ddos/
版权声明
本文为[zjt597778912]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204210550240921.html
边栏推荐
- Servlet learning notes
- How to do after winning the new debt? Is it safe to open an account online
- Resolve the error - error identifier 'attr_ id‘ is not in camel case camelcase
- The construction and use of Fortress machine and springboard machine jumpserver are detailed in pictures and texts
- Numpy mathematical function & logical function
- GO語言開發天天生鮮項目第三天 案例-新聞發布系統二
- Numpy Index & slice & iteration
- 上海回應“面粉官網是非法網站”:疏於運維被“黑”,警方已立案
- LeetCode 1337、矩阵中战斗力最弱的 K 行
- How to use PM2 management application? Come in and see
猜你喜欢

Come in and teach you how to solve the problem of port occupation
Installation and use of NVM
Leetcode 74. Search two-dimensional matrix
Commit and rollback in DCL of 16 MySQL
Resolve the eslint warning -- ignore the warning that there is no space between the method name and ()
![[graph theory brush question-4] force deduction 778 Swimming in a rising pool](/img/e3/a8cd9fc7773843e9e8ee6a6eba123f.png)
[graph theory brush question-4] force deduction 778 Swimming in a rising pool

DOS command of Intranet penetration
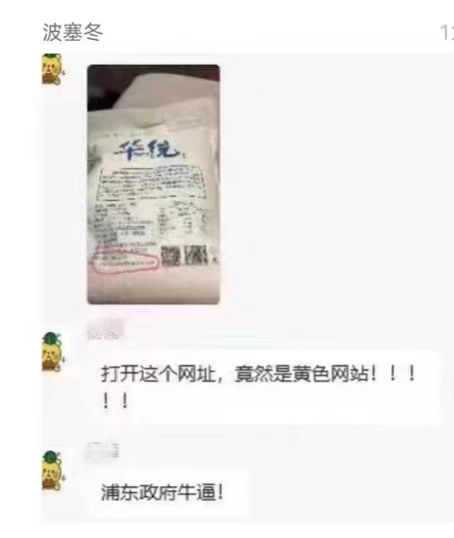
上海回应“面粉官网是非法网站”:疏于运维被“黑”,警方已立案

Shanghai a répondu que « le site officiel de la farine est illégal »: l'exploitation et l'entretien négligents ont été « noirs » et la police a déposé une plainte
Install MySQL 5.0 under Linux 64bit 6 - the root password cannot be modified
随机推荐
SQL gets the latest record of the data table
Identification of bolt points in aerial photography based on perception
Vscode download speed up
Preliminary understanding of cache elimination algorithm (LRU and LFU)
Come in and teach you how to solve the problem of port occupation
UnhandledPromiseRejectionwarning:CastError: Cast to ObjectId failed for value
Leetcode 232, queue with stack
Experience of mathematical modeling in 18 year research competition
JDBC tool class jdbcconutil gets the connection to the database
SQL: query duplicate data and delete duplicate data
JDBC database addition, deletion, query and modification tool class
【PTA】L1-006 连续因子
[latex] 5 how to quickly write out the latex formula corresponding to the formula
Use the rolling division method to find the maximum common divisor of two numbers
Use of node template engine
Solution: NPM err! code ELIFECYCLE npm ERR! errno 1
PIP installation package reports an error. Could not find a version that satisfies the requirement pymysql (from versions: none)
bounding box iou
Commande dos pour la pénétration de l'Intranet
【PTA】L1-002 打印沙漏