当前位置:网站首页>[popular science] CRC verification (I) what is CRC verification?
[popular science] CRC verification (I) what is CRC verification?
2022-04-23 18:35:00 【Linest-5】
Catalog
CRC( Cyclic redundancy check )
Schematic diagram of division XOR operation
CRC( Cyclic redundancy check )
CRC(Cyclic Redundancy Check) Cyclic redundancy test , Is a technology used to detect digital data errors . As a checksum type ,CRC Generate fixed length data sets based on the construction of files or larger data sets . As far as its purpose is concerned ,CRC It's a hash function , Used to detect unexpected changes in raw computer data commonly used in storage devices such as digital telecommunications networks and hard drives .
In cyclic redundancy check , A fixed number of check bits are appended to the message to be transmitted . The data receiver receives data , And check the check bit for any errors . In Mathematics , The data receiver evaluates the additional check value by looking for the rest of the polynomial division of the transmitted content . If something seems to have gone wrong , A negative confirmation will be sent , Request retransmission of data .
Cyclic redundancy check is also applicable to storage devices such as hard disks . under these circumstances , The check bit will be assigned to each block in the hard disk . When the computer reads a corrupted or incomplete file , A cyclic redundancy error will be triggered .CRC It can come from other storage devices or CD/DVD. Common causes of errors include system crashes , The document is incomplete or damaged , Or there are many wrong files .
CRC The polynomial design depends on the length of the block that should be protected . The error protection function can also determine CRC Design . Can be used for CRC The resources implemented may have an impact on performance . understand CRC Another way is to look at a specific word in its name . Experts point out that ,CRC go by the name of “ redundancy ”, Because it increases the size of the dataset without adding new information , and “ periodic ” Because it is suitable for periodic implementation systems .
As mentioned earlier , Pointed out that CRC Is a specific type of checksum, which is also helpful , Where a data set of any size is mapped to a fixed size string , It can be called a hash function . by comparison , The checksum itself can be very simple , for example , The primitive checksum can be just the sum of the relevant byte values . Using its periodic setting CRC It is generally considered a very good strategy for checking errors and verifying data integrity . It is part of an evolving toolkit for checksum usage and hashing, as well as general file checking .
CRC Check code generation
CRC The generation of check code mainly includes the following processes :
- Find the length of the divisor , This divisor is defined by ourselves .
- The number of digits of the divisor is reduced by one to CRC The number of digits of the check code , Suppose the number of digits of the divisor is 5, Then the number of digits of the check code is 4, The number of digits of the check code is added to the divisor, that is, the number of information to be transmitted 0, If the number of digits of the check code is 4, Then add... Directly after the divisor 4 individual 0
- Perform a division operation , Add 4 individual 0 As the new divisor , Divided by the divisor we define , After the division operation is completed , You will get two results : One is business , The other is the remainder .( Be careful : The division operation adopts XOR operation )
- The remainder we get, even if we want CRC Check code
CRC Sender and receiver of
The sender
The sender gives the data to be transmitted (Data), And define polynomials (polynomial), Get... As a polynomial (n+1) Bit divisor (divisor), Add... At the end of the data n position 0, As divisor , Divide the divisor by the divisor , The remainder is what you need to calculate n position CRC Check code , What will be obtained CRC The check code is spliced to the end of the original data to generate new data , Send this data to the receiver .
The receiving party
What the receiver needs to do is simpler , Take the whole block of data as the divisor , Use the divisor obtained at the sender to remove the divisor , If the remainder of the result is 0 Words , Represents that there is no error in the transmission of data , The data obtained is correct and effective .
The receiver has another way , Even if the sender sends data and CRC data , The end party gets the data, and the end is filled with n individual 0 As divisor , Divide the divisor by a polynomial , If the remainder is the receiver's CRC Check code , How the recipient gets CRC Data and from the sender CRC In agreement , It can also be proved that there is no problem with data transmission .

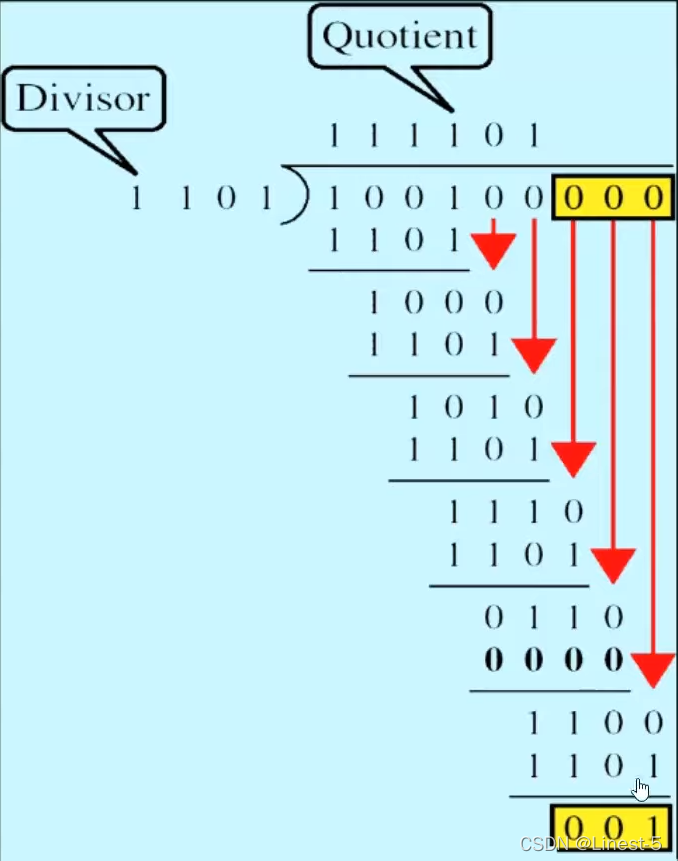
Schematic diagram of division XOR operation
You can see , The message we want to convey is 100100, That is, the divisor , Our custom divisor is 1101, Its digits are 4, So add... After the divisor 3 individual 0, Then divide and XOR , The final quotient is 111101, The remainder is 001, According to the previous definition , This remainder 001 That's what we want CRC Check code .
And then what will be generated CRC The check code is added after the original divisor , That is to say 100100 Fill in the back 001 have to 100100001, This is the new data we want to send. The information contains CRC Check code , The receiver can perform corresponding analysis .
More specific CRC The calculation method of check code can refer to one digit B standing up Main teaching video
[CRC check ] Manual calculation and visual demonstration
Show the customized polynomial in the form of circuit , The original data plus the corresponding number of digits 0, Enter the circuit in turn , The final generation is what we need CRC Check code . More detailed calculation methods can be learned in the video .

版权声明
本文为[Linest-5]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204231833552135.html
边栏推荐
- Connection mode of QT signal and slot connect() and the return value of emit
- Halo 开源项目学习(七):缓存机制
- 【ACM】455. Distribute Biscuits (1. Give priority to big biscuits to big appetite; 2. Traverse two arrays with only one for loop (use subscript index -- to traverse another array))
- os_authent_prefix
- 根据快递单号查询物流查询更新量
- Quantexa CDI(场景决策智能)Syneo平台介绍
- From introduction to mastery of MATLAB (2)
- Function recursion and solving interesting problems
- Deep learning classic network analysis and target detection (I): r-cnn
- Domestic GD chip can filter
猜你喜欢

使用晨曦记账本,分析某个时间段每个账户收支结余
Use stm32cube MX / stm32cube ide to generate FatFs code and operate SPI flash
视频边框背景如何虚化,简单操作几步实现
logstash 7. There is a time problem in X. the difference between @ timestamp and local time is 8 hours
The vivado project corresponding to the board is generated by TCL script
硬核解析Promise對象(這七個必會的常用API和七個關鍵問題你都了解嗎?)
ctfshow-web362(SSTI)
os_authent_prefix
MATLAB小技巧(6)七种滤波方法比较

Use Chenxi bookkeeping book to analyze the balance of revenue and expenditure of each account in a certain period of time
随机推荐
【ACM】455. 分发饼干(1. 大饼干优先喂给大胃口;2. 遍历两个数组可以只用一个for循环(用下标索引--来遍历另一个数组))
Log4j2 cross thread print traceid
硬核解析Promise對象(這七個必會的常用API和七個關鍵問題你都了解嗎?)
Linux installs MySQL in RPM (super simple)
PowerDesigner various font settings; Preview font setting; SQL font settings
数据库上机实验四(数据完整性与存储过程)
Spark performance optimization guide
MATLAB小技巧(6)七种滤波方法比较
ESP32 LVGL8. 1 - event (event 17)
QT reading and writing XML files (including source code + comments)
K210 serial communication
Install the yapiupload plug-in in idea and upload the API interface to the Yapi document
Keil RVMDK compiled data type
CISSP certified daily knowledge points (April 13, 2022)
Serial port debugging tools cutecom and minicom
CISSP certified daily knowledge points (April 12, 2022)
JD freefuck Jingdong HaoMao control panel background Command Execution Vulnerability
Using transmittablethreadlocal to realize parameter cross thread transmission
In win10 system, all programs run as administrator by default
Daily CISSP certification common mistakes (April 15, 2022)