当前位置:网站首页>Solidity IDE Remix中文版使用手册
Solidity IDE Remix中文版使用手册
2022-04-23 06:42:00 【ZhangJiQun.】
目录
版权声明
本文为[ZhangJiQun.]所创,转载请带上原文链接,感谢
https://zhangjq.blog.csdn.net/article/details/124355967
边栏推荐
- 高精度焊接机械臂定位
- Expression related to month, year and day in SVG
- Link to some good tutorials or notes about network security and record them
- Research on system and software security (I)
- Research on software security based on NLP (I)
- C read INI file and write data to INI file
- GUI,CLI与Unix哲学
- 从ES、MongoDB、Redis、RocketMQ出发谈分布式存储
- Cloud computing skills competition -- the first part of openstack private cloud environment
- Sto with billing cross company inventory dump return
猜你喜欢

SAP self created table log function is enabled

BUFFCTF文件中的秘密1

Online Safe Trajectory Generation For Quadrotors Using Fast Marching Method and Bernstein Basis Poly

Redis -- why is the string length of string emstr the upper limit of 44 bytes?

Internal network security attack and defense: a practical guide to penetration testing (8): Authority maintenance analysis and defense

BUUCTF MISC刷題

CSV Column Extract列提取
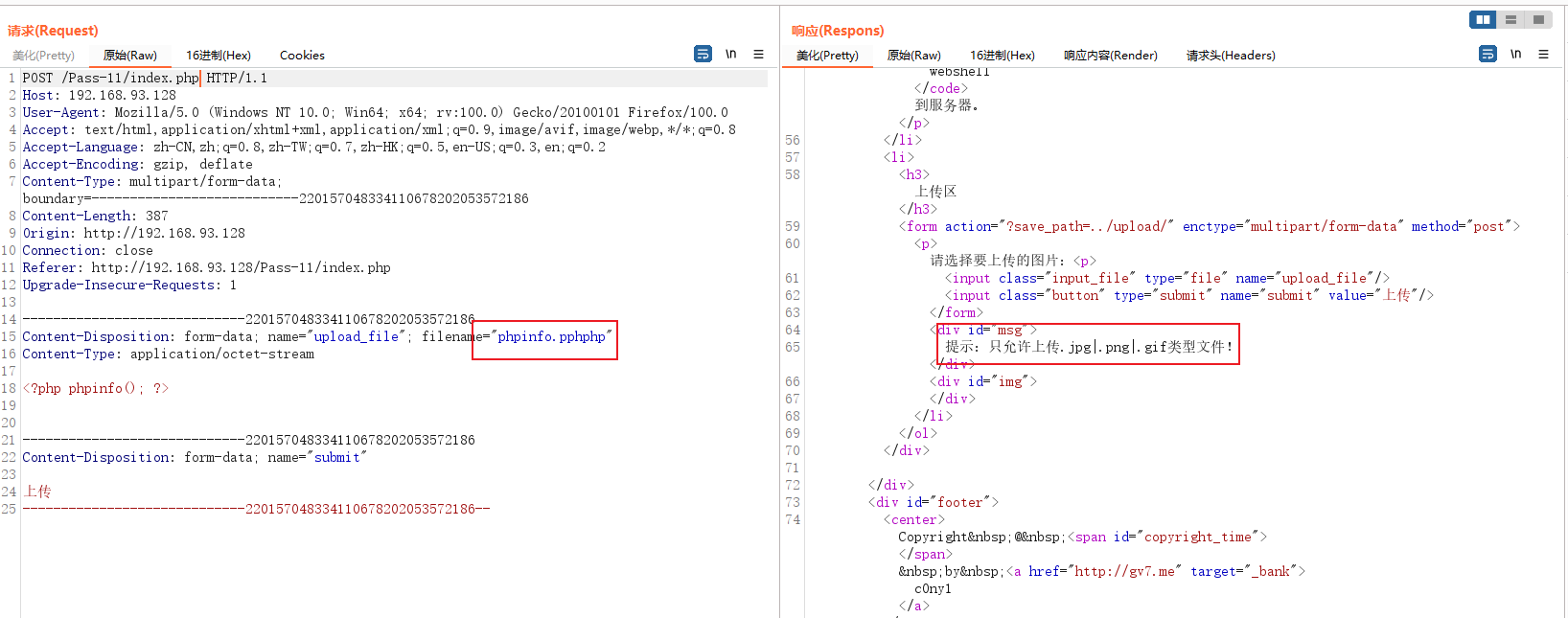
upload-labs 靶场练习

三星,再次“西征”

Buctf MISC brossage
随机推荐
Sto with billing cross company inventory dump return
惨了,搞坏了领导的机密文件,吐血分享备份文件的代码技巧
LeetCode 1611. 使整数变为 0 的最少操作次数
[极客大挑战 2019]Havefun1
1+x云计算中级--脚本搭建读写分离
简述存储器的分级策略
Ignis公链的NFT生态发展:Unicorn.art的捐赠开发之路
FUEL: Fast UAV Exploration using Incremental Frontier Structure and Hierarchical Planning
Simplify exporting to SVG data files and all images in SVG folder
vivo,硬件安全的爱与雷霆
Dvwa 靶场练习记录
MySQL -- the secret of lock -- how to lock data
Interview learning route
How does Apache Hudi accelerate traditional batch mode?
Mysql database backup and recovery under Linux (full + incremental)
Intranet penetration series: dnscat2 of Intranet tunnel
Using lambda expression to solve the problem of C file name sorting (whether it is 100 or 11)
Redis -- why is the string length of string emstr the upper limit of 44 bytes?
Research on system and software security (I)
Codeforces Round #784 (Div. 4)