当前位置:网站首页>MySQL -- the secret of lock -- how to lock data
MySQL -- the secret of lock -- how to lock data
2022-04-23 07:59:00 【Dream river dream】
First look at the structure of the watch

Here's the data
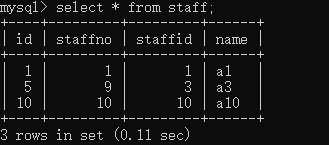
The experiment begins
Business 1

Business 2

Get lock occupancy information of current database

It can be seen that the transaction 1 and 2 Surface operation staffid Index and staffno Indexes , The primary key corresponding to the locked record
版权声明
本文为[Dream river dream]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230629085810.html
边栏推荐
- Chapter VII asset impairment
- Mongodb starts warning information processing
- Gets the maximum getmaxpoint in the list of all points
- 读取修改resource文件夹下的json文件
- 第四章 无形资产
- 爬虫学习笔记,学习爬虫,看本篇就够了
- Unity gets a resource that is referenced by those resources
- ABAP ALV显示金额与导出金额不一致
- Complete learning from scratch, machine learning and deep learning, including theory and code implementation, mainly using scikit and mxnet, and some practices (on kaggle)
- SAP Query增强开发介绍
猜你喜欢

Dictionary & lt; T1,T2> Sorting problem

How does Apache Hudi accelerate traditional batch mode?

Understanding the role of individual units in a deep neural networks

Online Safe Trajectory Generation For Quadrotors Using Fast Marching Method and Bernstein Basis Poly

The projection vector of a vector to a plane

Intranet penetration series: icmpsh of Intranet tunnel

Internal network security attack and defense: a practical guide to penetration testing (5): analysis and defense of horizontal movement in the domain

平面定义-平面方程
Chapter IV intangible assets

Houdini > fluid, rigid body export, learning process notes
随机推荐
SAP自建表log功能开启
关于unity获取真实地理地图转3D化的相关链接
一些关于网络安全的好教程或笔记的链接,记录一下
CTF-MISC学习之从开始到放弃
Houdini > variable building roads, learning process notes
String self generated code within a given range
TA notes of Zhuang understand (zero) < bedding and learning methods >
Idea shortcut
向量到一个平面的投影向量
Zhuang understand's TA notes (VI) < fakeenvreflect & rust, rust effect >
IT高薪者所具备的人格魅力
VBA calls SAP RFC to read & write data
Dictionary & lt; T1,T2&gt; Sorting problem
A series of articles, a summary of common vulnerabilities of Web penetration (continuously updated)
读取修改resource文件夹下的json文件
Link to some good tutorials or notes about network security and record them
Unity C single case mode learning review notes
SQL sorts string numbers
Intranet penetration series: icmpsh of Intranet tunnel
05数组的使用