当前位置:网站首页>x509解析
x509解析
2022-04-23 06:13:00 【MyeDy】
文章目录
X509
X509的ASN.1定义
[Certificate ::= SEQUENCE {
tbsCertificate TBSCertificate,
signatureAlgorithm AlgorithmIdentifier,
signature BIT STRING
}
首先,一张x509证书最顶层包含三个东西。
- TBSCertificate是X509里最重要的主体,也就是证书内容。
- AlgorithmIdentifier记录的是该证书被CA所签的算法。
- BIT STRING记录的是CA对该证书的签名。
TBSCertificate ::= SEQUENCE {
version [0] EXPLICIT Version DEFAULT v1,
serialNumber CertificateSerialNumber,
signature AlgorithmIdentifier,
issuer Name,
validity Validity,
subject Name,
subjectPublicKeyInfo SubjectPublicKeyInfo,
issuerUniqueID [1] IMPLICIT UniqueIdentifier OPTIONAL,-- If present, version must be v2or v3
subjectUniqueID [2] IMPLICIT UniqueIdentifier OPTIONAL,-- If present, version must be v2or v3
extensions [3] EXPLICIT Extensions OPTIONAL-- If present, version must be v3
}
那TBSCertificate中包含了以上的字段:
- Version:证书版本号
- CertificateSerialNumber:证书序列号
- AlgorithmIdentifier:证书中签名的算法
- issuer Name:发布者的名字,即签名者
- validity Validity:证书的有效期,包含起始时间和过期时间
- subject Name:主体名字,即被签名者
- subjectPublicKeyInfo SubjectPublicKeyInfo:签名算法的公钥信息
- issuerUniqueID: 发布者的唯一序列号
- subjectUniqueID:被签者的唯一序号
- extensions:签名扩展内容,不知道用来干啥
Version ::= INTEGER {
v1(0), v2(1), v3(2)
}
版本号字段就三种选项,V1, V2, V3
CertificateSerialNumber ::= INTEGER
版本序列号是一个整形变量
Validity ::= SEQUENCE {
notBefore CertificateValidityDate,
notAfter CertificateValidityDate
}
CertificateValidityDate ::= CHOICE {
utcTime UTCTime,
generalTime GeneralizedTime
}
证书有效时间包含证书的起始时间notBefore 和证书的过期时间notAfter
UniqueIdentifier ::= BIT STRING
SubjectPublicKeyInfo ::= SEQUENCE {
algorithm AlgorithmIdentifier,
subjectPublicKey
}
证书公钥信息包含两部分
- AlgorithmIdentifier签名算法
- 签名内容本身subjectPublicKey
Extensions ::= SEQUENCE OF Extension
Extension ::= SEQUENCE {
extnID OBJECT IDENTIFIER,
critical BOOLEAN DEFAULT FALSE,
extnValue OCTET STRING
}
扩展不知道用来干啥
实际X509证书长什么样
先上传一个X509证书,来实际分析一下X509证书。这里第一种是ASN.1的二进制格式cert.der,第二种是openssl的PEM格式cert.pem。PEM格式的证书可以直接用文本编辑器看,而ASN.1格式的证书需要用asn1dump来查看。
cert.pem和cert.der下载
提取码:s36x
PEM格式
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 826366320 (0x31415970)
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=SRK1_sha256_1024_65537_v3_ca
Validity
Not Before: Jun 27 11:46:11 2018 GMT
Not After : Jun 25 11:46:11 2026 GMT
Subject: CN=IMG1_1_sha256_1024_65537_v3_usr
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (1024 bit)
Modulus:
00:a9:9f:5e:de:64:b8:28:30:be:37:07:e3:ef:f4:
05:83:8f:96:b0:f2:60:76:13:60:61:84:e6:06:b0:
f7:fb:6d:8e:cb:cd:41:6b:21:60:7a:94:46:7c:99:
d8:e9:d6:31:01:a9:fc:36:88:b4:9e:85:58:40:d1:
33:0c:55:95:ba:bd:a5:30:a5:1f:ba:a0:d0:62:a1:
48:4c:83:e0:75:b2:51:55:11:b6:27:1f:8a:1c:d8:
80:15:0f:ab:c7:4a:37:e6:31:7f:43:dd:c0:4d:ed:
60:eb:88:a3:6d:9b:0c:c9:fa:96:57:97:71:48:65:
9c:70:e3:4e:d2:be:14:8d:8b
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
6B:5D:F5:7E:3D:73:AE:49:6E:C7:E1:98:11:96:7E:D1:43:48:F1:00
X509v3 Authority Key Identifier:
keyid:A3:41:D3:85:05:17:C0:90:1F:BE:AD:C1:50:04:E5:1C:01:79:6F:D2
Signature Algorithm: sha256WithRSAEncryption
9a:47:77:4b:ce:f8:0d:f3:e1:68:64:52:3e:9b:95:76:e7:cd:
9f:35:c7:eb:73:eb:f2:6d:6e:2d:db:a3:51:e3:1f:98:12:2a:
92:ff:58:b9:1c:39:a1:79:27:c1:80:76:cb:09:0a:35:e2:5f:
ca:55:37:b7:9d:03:5a:09:8d:df:e6:34:4b:77:fe:47:0c:45:
1c:27:60:bf:47:44:ba:3c:33:c1:5f:05:0b:0f:44:ec:16:33:
1e:75:96:26:cb:5d:2f:1a:c9:d4:f2:4d:12:84:f8:1e:91:3f:
de:07:3c:9f:71:8c:07:e0:a4:89:e2:f4:f0:e5:7c:8a:c5:9b:
11:bf
-----BEGIN CERTIFICATE-----
MIICRTCCAa6gAwIBAgIEMUFZcDANBgkqhkiG9w0BAQsFADAnMSUwIwYDVQQDDBxT
UksxX3NoYTI1Nl8xMDI0XzY1NTM3X3YzX2NhMB4XDTE4MDYyNzExNDYxMVoXDTI2
MDYyNTExNDYxMVowKjEoMCYGA1UEAwwfSU1HMV8xX3NoYTI1Nl8xMDI0XzY1NTM3
X3YzX3VzcjCBnzANBgkqhkiG9w0BAQEFAAOBjQAwgYkCgYEAqZ9e3mS4KDC+Nwfj
7/QFg4+WsPJgdhNgYYTmBrD3+22Oy81BayFgepRGfJnY6dYxAan8Noi0noVYQNEz
DFWVur2lMKUfuqDQYqFITIPgdbJRVRG2Jx+KHNiAFQ+rx0o35jF/Q93ATe1g64ij
bZsMyfqWV5dxSGWccONO0r4UjYsCAwEAAaN7MHkwCQYDVR0TBAIwADAsBglghkgB
hvhCAQ0EHxYdT3BlblNTTCBHZW5lcmF0ZWQgQ2VydGlmaWNhdGUwHQYDVR0OBBYE
FGtd9X49c65JbsfhmBGWftFDSPEAMB8GA1UdIwQYMBaAFKNB04UFF8CQH76twVAE
5RwBeW/SMA0GCSqGSIb3DQEBCwUAA4GBAJpHd0vO+A3z4WhkUj6blXbnzZ81x+tz
6/Jtbi3bo1HjH5gSKpL/WLkcOaF5J8GAdssJCjXiX8pVN7edA1oJjd/mNEt3/kcM
RRwnYL9HRLo8M8FfBQsPROwWMx51libLXS8aydTyTRKE+B6RP94HPJ9xjAfgpIni
9PDlfIrFmxG/
-----END CERTIFICATE-----
在-----BEGIN CERTIFICATE-----上面是一段可以人肉读的描述文字,主要描述了TBSCertificate这个结构,可以看出它的版本号是x509v3, 序列号是826366320
Data:
Version: 3 (0x2)
Serial Number: 826366320 (0x31415970)
签名算法是sha256WithRSAEncryption
Signature Algorithm: sha256WithRSAEncryption
发布者是SRK1_sha256_1024_65537_v3_ca,被签者是IMG1_1_sha256_1024_65537_v3_usr
Issuer: CN=SRK1_sha256_1024_65537_v3_ca
Subject: CN=IMG1_1_sha256_1024_65537_v3_usr
有效期是从2018-6-27到2026-6-25
Validity
Not Before: Jun 27 11:46:11 2018 GMT
Not After : Jun 25 11:46:11 2026 GMT
公钥是RSA 1024bit,公钥的moduls和exponent都列出来了:
Public Key Algorithm: rsaEncryption
Public-Key: (1024 bit)
Modulus:
00:a9:9f:5e:de:64:b8:28:30:be:37:07:e3:ef:f4:
05:83:8f:96:b0:f2:60:76:13:60:61:84:e6:06:b0:
f7:fb:6d:8e:cb:cd:41:6b:21:60:7a:94:46:7c:99:
d8:e9:d6:31:01:a9:fc:36:88:b4:9e:85:58:40:d1:
33:0c:55:95:ba:bd:a5:30:a5:1f:ba:a0:d0:62:a1:
48:4c:83:e0:75:b2:51:55:11:b6:27:1f:8a:1c:d8:
80:15:0f:ab:c7:4a:37:e6:31:7f:43:dd:c0:4d:ed:
60:eb:88:a3:6d:9b:0c:c9:fa:96:57:97:71:48:65:
9c:70:e3:4e:d2:be:14:8d:8b
Exponent: 65537 (0x10001)
接下来是扩展项和签名本身:
Signature Algorithm: sha256WithRSAEncryption
9a:47:77:4b:ce:f8:0d:f3:e1:68:64:52:3e:9b:95:76:e7:cd:
9f:35:c7:eb:73:eb:f2:6d:6e:2d:db:a3:51:e3:1f:98:12:2a:
92:ff:58:b9:1c:39:a1:79:27:c1:80:76:cb:09:0a:35:e2:5f:
ca:55:37:b7:9d:03:5a:09:8d:df:e6:34:4b:77:fe:47:0c:45:
1c:27:60:bf:47:44:ba:3c:33:c1:5f:05:0b:0f:44:ec:16:33:
1e:75:96:26:cb:5d:2f:1a:c9:d4:f2:4d:12:84:f8:1e:91:3f:
de:07:3c:9f:71:8c:07:e0:a4:89:e2:f4:f0:e5:7c:8a:c5:9b:
11:bf
-----BEGIN CERTIFICATE-----到-----END CERTIFICATE-----存放的是整个证书的BASE64编码。用BASE64解码后就可以得到ASN.1编码的证书。 下面来看下解析ASN.1 格式的证书。
ASN.1格式
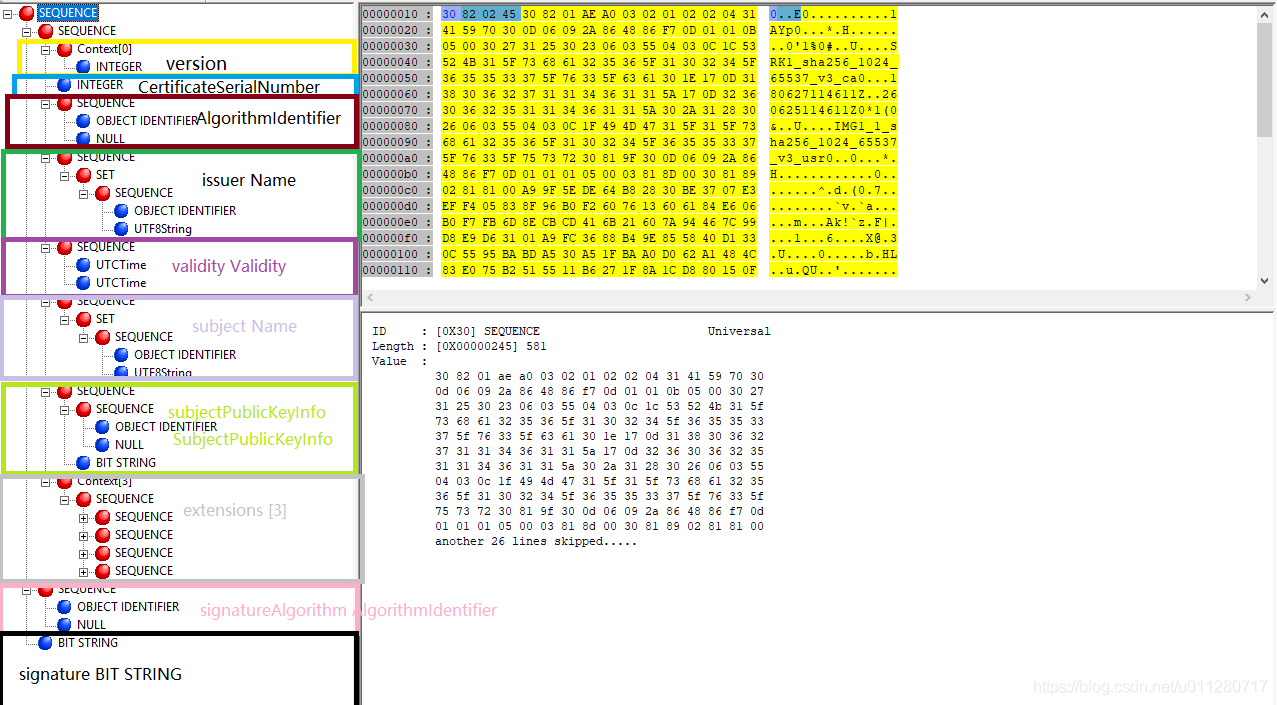
用ASN1DUMP打开cert.der, 可以看到根据这个二进制文件解析出了一颗树状结构体。这棵树的结构就跟Certificate ::= SEQUENCE定义是一模一样的。接下来我们一个个看看每一个ASN1条目中的东西,其中的内容跟pem格式文件里的内容可以一一对应上。
version
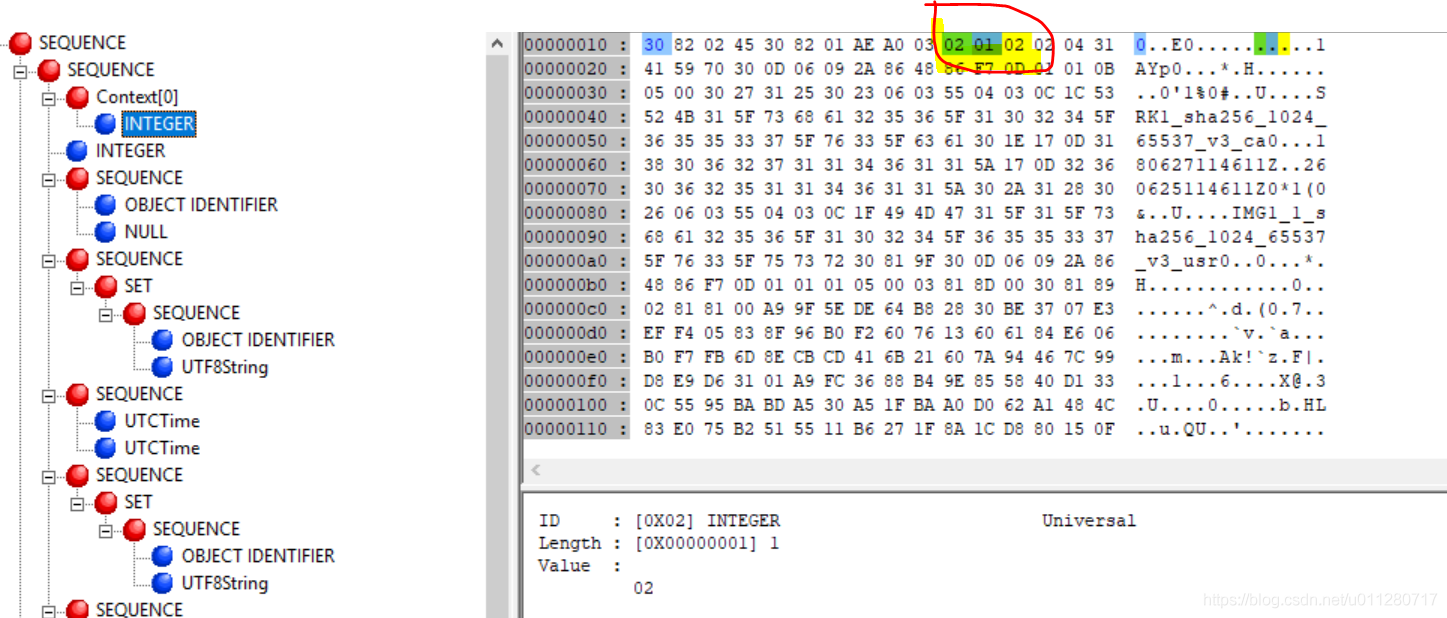
version 是一个ASN1 INTEGER类型(0x02),长度是1(0x1), 数据是0x2,说明版本号是x509v3。
CertificateSerialNumber
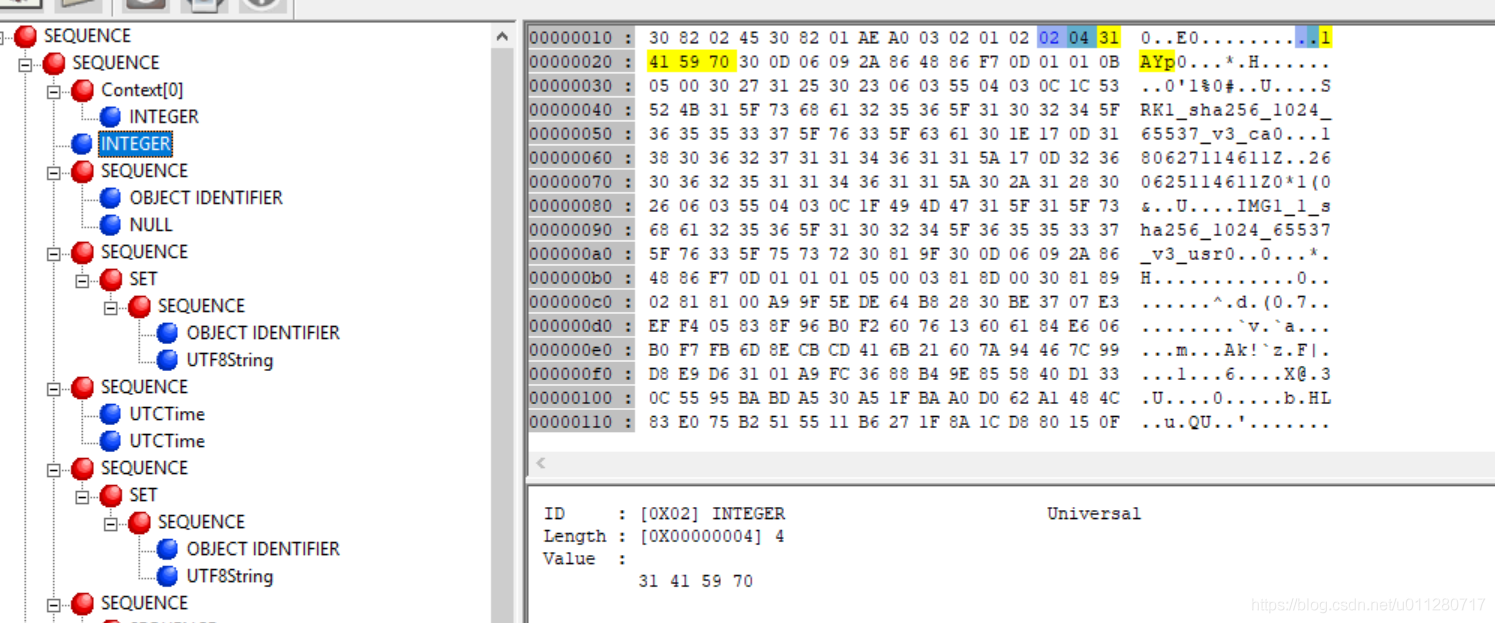
序列号也是一个ASN1 INTEGER类型,长度是4, 数据是0x31415970就是826366320。
AlgorithmIdentifier

在www.oid-info.com上查询这个OID的结果,它代表的是sha256-with-rsa-signature,即使用了SHA1摘要算法的RSA签名算法。
issuer

issuer由一个sequence组成,sequence下面有一个set,set下面又跟了一个sequence。最后的sequence包含了两个东西,一个是OID,解析出来是commonName,另外一个UTF8String是issuer的名字,这里就是SRK1_sha256_1024_65537_v3_ca。
subject Name

subject由一个sequence组成,sequence下面有一个set,set下面又跟了一个sequence。最后的sequence包含了两个东西,一个是OID,解析出来是commonName,另外一个UTF8String是issuer的名字,这里就IMG1_1_sha256_1024_65537_v3_ca。
Subject Public Key Info
接下来是Subject Public Key Info,首先oid是rsaEncryption

Subject Public Key Info中的BIT STRING就是公钥的二进制,包含Modulus和Exponent,可以看到其内容和PEM里面存放的key是一样

CA对该证书的签名
证书的最后一段放的就是签名内容

python 解析x509证书
#!/usr/bin/python
import OpenSSL
import time
from dateutil import parser
def main():
x509_cert_file = open('IMG1_1_sha256_1024_65537_v3_usr_crt.pem')
x509_cert_payload = x509_cert_file.read()
x509_cert_file.close()
x509_cert = OpenSSL.crypto.load_certificate(OpenSSL.crypto.FILETYPE_PEM, x509_cert_payload)
print('verison:{}'.format(x509_cert.get_version() + 1))
print('serial_number:{}'.format(x509_cert.get_serial_number()))
print('algorithm:{}'.format(x509_cert.get_signature_algorithm().decode("UTF-8")))
print('issuer:.{}'.format(x509_cert.get_issuer().commonName))
datetime_struct = parser.parse(x509_cert.get_notBefore().decode("UTF-8"))
print('not before:{}'.format(datetime_struct.strftime('%Y-%m-%d %H:%M:%S')))
datetime_struct = parser.parse(x509_cert.get_notAfter().decode("UTF-8"))
print('not after:{}'.format(datetime_struct.strftime('%Y-%m-%d %H:%M:%S')))
print('is_expired:{}'.format(x509_cert.has_expired()))
print('public key:{}'.format(OpenSSL.crypto.dump_publickey(OpenSSL.crypto.FILETYPE_PEM, x509_cert.get_pubkey()).decode("utf-8")))
main()
运行结果
:~/my_scripts$./openssl_x509.py
verison:3
serial_number:826366320
algorithm:sha256WithRSAEncryption
issuer:.SRK1_sha256_1024_65537_v3_ca
not before:2018-06-27 11:46:11
not after:2026-06-25 11:46:11
is_expired:False
public key:-----BEGIN PUBLIC KEY-----
MIGfMA0GCSqGSIb3DQEBAQUAA4GNADCBiQKBgQCpn17eZLgoML43B+Pv9AWDj5aw
8mB2E2BhhOYGsPf7bY7LzUFrIWB6lEZ8mdjp1jEBqfw2iLSehVhA0TMMVZW6vaUw
pR+6oNBioUhMg+B1slFVEbYnH4oc2IAVD6vHSjfmMX9D3cBN7WDriKNtmwzJ+pZX
l3FIZZxw407SvhSNiwIDAQAB
-----END PUBLIC KEY-----
C语言解析X509证书
#include <openssl/x509.h>
int main()
{
X509 *x509_cert;
FILE *fp;
unsigned char buf[5000], *p;
int len, ret;
BIO *b;
fp = fopen("cert.der", "rb");
if (!fp)
return -1;
len = fread(buf, 1, 5000, fp);
fclose(fp);
p = buf;
x509_cert = X509_new();
d2i_X509(&x509_cert, (const unsigned char **)&p, len);
b = BIO_new(BIO_s_file());
BIO_set_fp(b, stdout, BIO_NOCLOSE);
ret =X509_print(b, x509_cert);
BIO_free(b);
X509_free(x509_cert);
return 0;
}
运行结果
gcc openssl_x509.c -lcrypto -lssl;./a.out
Certificate:
Data:
Version: 3 (0x2)
Serial Number: 826366320 (0x31415970)
Signature Algorithm: sha256WithRSAEncryption
Issuer: CN=SRK1_sha256_1024_65537_v3_ca
Validity
Not Before: Jun 27 11:46:11 2018 GMT
Not After : Jun 25 11:46:11 2026 GMT
Subject: CN=IMG1_1_sha256_1024_65537_v3_usr
Subject Public Key Info:
Public Key Algorithm: rsaEncryption
Public-Key: (1024 bit)
Modulus:
00:a9:9f:5e:de:64:b8:28:30:be:37:07:e3:ef:f4:
05:83:8f:96:b0:f2:60:76:13:60:61:84:e6:06:b0:
f7:fb:6d:8e:cb:cd:41:6b:21:60:7a:94:46:7c:99:
d8:e9:d6:31:01:a9:fc:36:88:b4:9e:85:58:40:d1:
33:0c:55:95:ba:bd:a5:30:a5:1f:ba:a0:d0:62:a1:
48:4c:83:e0:75:b2:51:55:11:b6:27:1f:8a:1c:d8:
80:15:0f:ab:c7:4a:37:e6:31:7f:43:dd:c0:4d:ed:
60:eb:88:a3:6d:9b:0c:c9:fa:96:57:97:71:48:65:
9c:70:e3:4e:d2:be:14:8d:8b
Exponent: 65537 (0x10001)
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
6B:5D:F5:7E:3D:73:AE:49:6E:C7:E1:98:11:96:7E:D1:43:48:F1:00
X509v3 Authority Key Identifier:
keyid:A3:41:D3:85:05:17:C0:90:1F:BE:AD:C1:50:04:E5:1C:01:79:6F:D2
Signature Algorithm: sha256WithRSAEncryption
9a:47:77:4b:ce:f8:0d:f3:e1:68:64:52:3e:9b:95:76:e7:cd:
9f:35:c7:eb:73:eb:f2:6d:6e:2d:db:a3:51:e3:1f:98:12:2a:
92:ff:58:b9:1c:39:a1:79:27:c1:80:76:cb:09:0a:35:e2:5f:
ca:55:37:b7:9d:03:5a:09:8d:df:e6:34:4b:77:fe:47:0c:45:
1c:27:60:bf:47:44:ba:3c:33:c1:5f:05:0b:0f:44:ec:16:33:
1e:75:96:26:cb:5d:2f:1a:c9:d4:f2:4d:12:84:f8:1e:91:3f:
de:07:3c:9f:71:8c:07:e0:a4:89:e2:f4:f0:e5:7c:8a:c5:9b:
11:bf
版权声明
本文为[MyeDy]所创,转载请带上原文链接,感谢
https://blog.csdn.net/u011280717/article/details/90044347
边栏推荐
- Pytorch model pruning example tutorial III. multi parameter and global pruning
- Chapter 3 pytoch neural network toolbox
- 机器学习 二:基于鸢尾花(iris)数据集的逻辑回归分类
- [dynamic programming] longest increasing subsequence
- ThreadLocal, just look at me!
- 1.1 pytorch and neural network
- C language, a number guessing game
- Unwind 栈回溯详解
- 多机多卡训练时的错误
- Wechat applet uses wxml2canvas plug-in to generate some problem records of pictures
猜你喜欢
1.2 初试PyTorch神经网络

ThreadLocal, just look at me!
【點雲系列】SG-GAN: Adversarial Self-Attention GCN for Point Cloud Topological Parts Generation

机器学习——PCA与LDA

MySQL的安装与配置——详细教程

【点云系列】Pointfilter: Point Cloud Filtering via Encoder-Decoder Modeling
![[point cloud series] pnp-3d: a plug and play for 3D point clouds](/img/83/3662bc668602110236e43ee0b9d7ac.png)
[point cloud series] pnp-3d: a plug and play for 3D point clouds
rearrange 和 einsum 真的优雅吗

c语言编写一个猜数字游戏编写

Chapter 5 fundamentals of machine learning
随机推荐
[dynamic programming] different binary search trees
EasyUI combobox determines whether the input item exists in the drop-down list
Machine learning III: classification prediction based on logistic regression
微信小程序 使用wxml2canvas插件生成图片部分问题记录
Easyui combobox 判断输入项是否存在于下拉列表中
PyTorch 12. hook的用法
第8章 生成式深度学习
PyTorch训练一个网络的基本流程5步法
Five methods are used to obtain the parameters and calculation of torch network model
SSL / TLS application example
深度学习模型压缩与加速技术(一):参数剪枝
Pytorch模型保存与加载(示例)
【動態規劃】不同路徑2
Device Tree 详解
Minesweeping games
Common regular expressions
[point cloud series] pnp-3d: a plug and play for 3D point clouds
Write a wechat double open gadget to your girlfriend
Paddleocr image text extraction
Pytoch model saving and loading (example)