当前位置:网站首页>2021 Great Wall Cup WP
2021 Great Wall Cup WP
2022-04-23 17:39:00 【Xiao Lan`】
2021 Great Wall Cup WP
MISC
You this flag Is it cooked ?
Open and find two pictures. One is a compressed package , After looking at the two pictures, I found that there is additional compressed packet data , extracted .
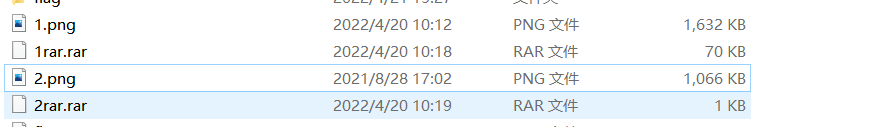
And unpack it , You'll get one xls Documents and a txt file , according to txt File to draw this curve and find it a bit like Hilbert curve , So the relevant characters are extracted according to the meaning of the curve .
import numpy as np
from PIL import Image
from hilbertcurve.hilbertcurve import HilbertCurve
import pandas as pd
arr = pd.read_excel('./password.xls',header=None)
hilbert_curve = HilbertCurve(17, 2)
s = ''
for i in range(np.size(arr)):
[x,y] = hilbert_curve.point_from_distance(i)
s += str(arr[y][x])
#print(s) # written words
with open('flag.txt','w') as f:
f.write(s)
with open("flag.txt",'r') as f:
a = f.read()
import base64
while True:
a = base64.b64decode(a)
print(a)
Write the document and continue to base64 decode .
Finally get :

And then to flag.rar Enter our password and unzip successfully , Find out flag.php It's in the file brainfuck character , After input, it is found that it can't run , It's embarrassing . After debugging under the guidance of the eight gods, I saw a wave of files that were really output errpr, But here we need to look at the variables in the middle .
8 god : If it counts for half a day but doesn't . Then the result will stay in cell in , You can't see it.
Just look for a decent interpreter bf The real-time memory in the code running is OK
Is equivalent to print Delete everything , The contents of the operation are kept in temporary variables

Decrypt online .

Xiao Ming's computer
A memory forensics problem , The first is given fl4g The file is not only in reverse order, but also two bytes are in reverse order with each other , Then you need to use script to restore .
import binascii
from heapq import _heapify_max
hexdata_all=''
with open('fl4g','rb') as f: # The file directory can be changed
hexdata_all=f.read().hex()
hexdata_all = hexdata_all[::-1]
hexdata_all = list(hexdata_all)
print(type(hexdata_all))
for num in range(0,len(hexdata_all),2):
hexdata_all[num],hexdata_all[num+1] = hexdata_all[num+1],hexdata_all[num]
hexdata_all = ''.join(hexdata_all)
with open('fl4ggg.zip','wb') as f: # The file directory can be changed
f.write(binascii.unhexlify(hexdata_all))
Then there are all kinds of decoding , To get to the last level, you need a password , At this time, let's see what's on the mirror .
View basic information :

Check some information :

Just put this png To take out : ( After you take it out, you need to .dat Change the document to png file )

Put it in Zsteg Direct violence in search of , Find the account password .

WEB
版权声明
本文为[Xiao Lan`]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204231732043429.html
边栏推荐
- XTask与Kotlin Coroutine的使用对比
- Self use learning notes - connected and non connected access to database
- Perception of linear algebra 2
- ClickHouse-SQL 操作
- Seven cattle upload pictures (foreground JS + background C API get token)
- Router object, route object, declarative navigation, programmed navigation
- 394. 字符串解码-辅助栈
- Abnormal resolution of Xiaomi camera
- Future 用法详解
- 402. Remove K digits - greedy
猜你喜欢

Qt error: /usr/bin/ld: cannot find -lGL: No such file or directory

SiteServer CMS5. 0 Usage Summary
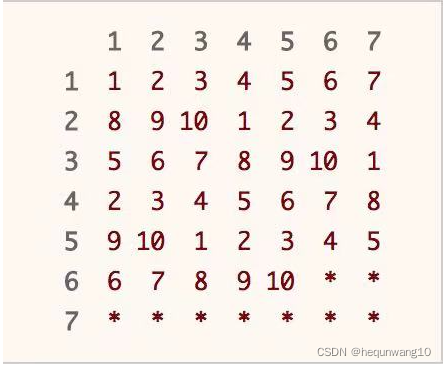
470. Rand10() is implemented with rand7()
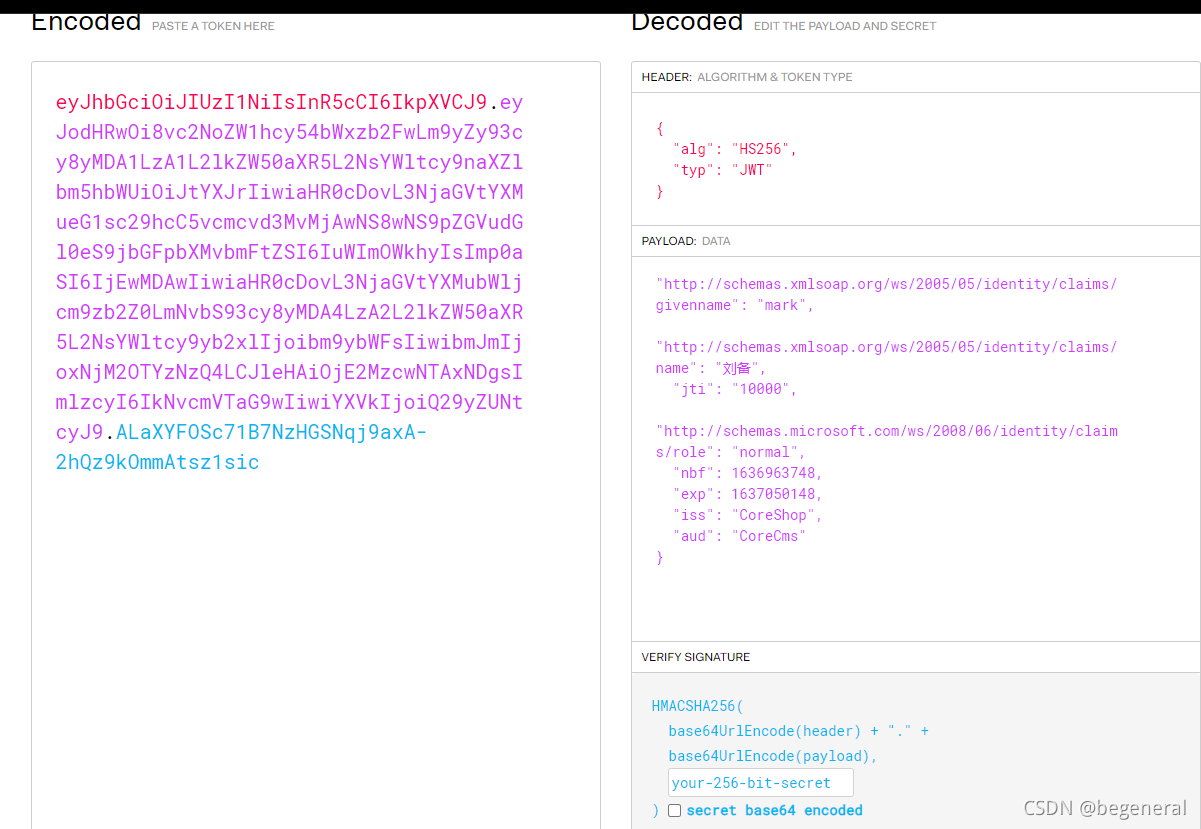
ASP. Net core JWT certification
![Using quartz under. Net core - [1] quick start](/img/80/b99417e88d544ca6e3da4c0c1625ce.png)
Using quartz under. Net core - [1] quick start

干货 | 快速抽取缩略图是怎么练成的?
2.Electron之HelloWorld
MySQL进阶之索引【分类,性能分析,使用,设计原则】
In embedded system, must the program code in flash be moved to ram to run?

HCIP第五次实验
随机推荐
958. 二叉树的完全性检验
Change Oracle to MySQL
If you start from zero according to the frame
超分之TDAN
Exercise: even sum, threshold segmentation and difference (two basic questions of list object)
Double pointer advanced -- leetcode title -- container with the most water
2.Electron之HelloWorld
386. Dictionary order (medium) - iteration - full arrangement
Understanding of RPC core concepts
Use of todesk remote control software
198. Looting - Dynamic Planning
1217_ Generating target files using scons
ECMAScript history
剑指 Offer 03. 数组中重复的数字
How to manually implement the mechanism of triggering garbage collection in node
The system cannot be started after AHCI is enabled
Websocket (basic)
Devexpress GridView add select all columns
Matlab / Simulink simulation of double closed loop DC speed regulation system
MySQL进阶之索引【分类,性能分析,使用,设计原则】