当前位置:网站首页>Face to face summary 2
Face to face summary 2
2022-04-23 08:05:00 【Pen drawing Acacia】
1: Realization sleep function .
Wait for the specified time before executing
function spleep1(ms,fun)
{
setTimeout(() => {
fun();
}, ms);
}
spleep1(1000,()=>{
console.log("132");
})
2:css The priority of the
a, Different levels of priority :
!important > Inline style >ID Selectors > Class selectors > label > wildcard > Inherit > Browser default properties
b, Peer priority :
The later written style in the same level will overwrite the first written style
c, When multiple levels are added up
**3:DNS What is it? ? **
CDN It is to allocate the nearest resource according to the user's location , Users don't need to visit the source station directly when they surf the Internet , It's a visit away from him “ Current ” One CDN node , The term is edge node , In fact, it is a proxy server that caches the content of the source site .
Principle analysis :
adopt DNS What you get is no longer ip Address , It is a CNAME(Canonical Name ) Alias record , Point to CDN Global load balancing
effect :
Improve the speed of user access
3:background-size Of cover and content Usage of
background-size:cover; Represents the stretching of the background picture , If you do it on your cell phone , The background picture will be enlarged , The distortion . This is not right
background-size:content; Indicates that the background picture is normally displayed in the content area , stay pc Stretch end will be covered , But the phone normally displays
4: Block-level elements , Inline elements , The difference between inline block elements
6:commonjs and es6 The difference between modularity
7:
版权声明
本文为[Pen drawing Acacia]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204230624332917.html
边栏推荐
- 数据库之MySQL——基础篇
- C smoothprogressbar custom progress bar control
- Buuctf misc brush questions
- How does feign integrate hystrix
- 云计算技能大赛 -- openstack私有云环境 第一部分
- Internal network security attack and defense: a practical guide to penetration testing (IV): Authority improvement analysis and defense
- Cloud computing skills competition -- Part 2 of openstack private cloud environment
- 内网渗透系列:内网隧道之icmp_tran
- [programming practice / embedded competition] learning record of embedded competition (I): establishment of TCP server and web interface
- C 输出一种二维数组,特点如下。
猜你喜欢

Intranet penetration series: dns2tcp of Intranet tunnel
![[programming practice / embedded competition] learning record of embedded competition (II): picture streaming based on TCP](/img/6c/7408180d0c24560b4a68982635520e.jpg)
[programming practice / embedded competition] learning record of embedded competition (II): picture streaming based on TCP

SAP GUI security

C # control the camera, rotate and drag the observation script (similar to scenes observation mode)

Concours de compétences en informatique en nuage - - première partie de l'environnement cloud privé openstack
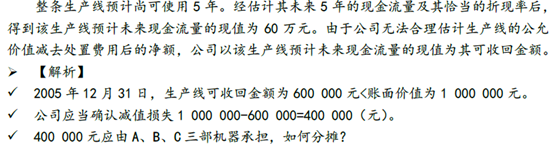
Chapter VII asset impairment

Redis--为什么字符串emstr的字符串长度是44字节上限?

Intranet penetration series: icmptunnel of Intranet tunnel (by master dhavalkapil)
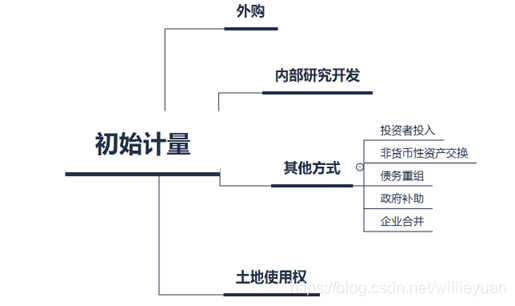
第四章 无形资产

When using flash, the code ends automatically without an error, the connection cannot be maintained, and the URL cannot be accessed.
随机推荐
Intranet penetration series: dnscat2 of Intranet tunnel
Automatically fit single line text into the target rectangle
Internal network security attack and defense: a practical guide to penetration testing (IV): Authority improvement analysis and defense
内网渗透系列:内网隧道之icmp_tran
Research on system and software security (5)
[NLP notes] preliminary study on CRF principle
The displayed amount of ABAP ALV is inconsistent with the exported amount
惨了,搞坏了领导的机密文件,吐血分享备份文件的代码技巧
Cloud computing skills competition -- the first part of openstack private cloud environment
SAP tr manual import system operation manual
Three minutes to teach you to use Houdini fluid > > to solve particle fluid droplets
【编程实践/嵌入式比赛】嵌入式比赛学习记录(一):TCP服务器和web界面的建立
Reptile learning notes, learning reptile, read this article is enough
第五章 投资性房地产
Intranet penetration series: pingtunnel of Intranet tunnel
在线YAML转XML工具
Ctf-misc learning from start to give up
LeetCode15. 三数之和
Research on software security based on NLP (2)
数据库之Mysql——概述安装篇