当前位置:网站首页>Feign源码分析
Feign源码分析
2022-04-23 06:32:00 【梦江河梦】
GitHub github = Feign.builder()
.decoder(new GsonDecoder())
.target(GitHub.class, "https://api.github.com");
public interface GitHub {
@RequestLine("GET /repos/{owner}/{repo}/contributors")
List<Contributor> contributors(@Param("owner") String owner, @Param("repo") String repository);
class Contributor {
String login;
int contributions;
}
}
上面会生成Github接口的实现类,下面来一探究竟
1)Feign.builder()会new出Feign的一个内部类feign.Feign.Builder;
2)通过target方法,将参数包装成Target类,然后是build方法
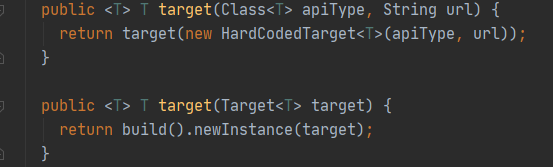

上面把Contract类传入到ParseHandlersByName中,最后new出一个
Feign接口的实现类


版权声明
本文为[梦江河梦]所创,转载请带上原文链接,感谢
https://blog.csdn.net/weixin_42002747/article/details/121435942
边栏推荐
- Chapter V investment real estate
- Three minutes to teach you to use Houdini fluid > > to solve particle fluid droplets
- TA notes of Zhuang understand (zero) < bedding and learning methods >
- C # control the camera, rotate and drag the observation script (similar to scenes observation mode)
- Internal network security attack and defense: a practical guide to penetration testing (VII): cross domain attack analysis and defense
- C read INI file and write data to INI file
- Mongodb starts warning information processing
- Personality charm of high paid it workers
- Nodejs (VI) sub process operation
- 【编程实践/嵌入式比赛】嵌入式比赛学习记录(二):基于TCP的图片流传输
猜你喜欢

第五章 投资性房地产

庄懂的TA笔记(七)<Lambert+Phong+Shadow+3EvColor+AO>
![MySQL8. 0 installation / uninstallation tutorial [window10 version]](/img/9c/1acf153b410f0d2eb6a23dcdbabb88.png)
MySQL8. 0 installation / uninstallation tutorial [window10 version]

Apache Hudi 如何加速传统的批处理模式?

Intranet penetration series: icmpsh of Intranet tunnel

《内网安全攻防:渗透测试实战指南》读书笔记(八):权限维持分析及防御
![[unity VFX] Introduction notes of VFX special effects - spark production](/img/bb/a6c637d025dfb8877e6b85e7f39d6b.png)
[unity VFX] Introduction notes of VFX special effects - spark production

内网渗透系列:内网隧道之dnscat2

Dictionary & lt; T1,T2&gt; Sorting problem

Houdini地形与流体解算(模拟泥石流)
随机推荐
Internal network security attack and defense: a practical guide to penetration testing (IV): Authority improvement analysis and defense
Complete learning from scratch, machine learning and deep learning, including theory and code implementation, mainly using scikit and mxnet, and some practices (on kaggle)
Index locked data cannot be written to es problem handling
从ES、MongoDB、Redis、RocketMQ出发谈分布式存储
Simplify exporting to SVG data files and all images in SVG folder
Mongodb starts warning information processing
Internal network security attack and defense: a practical guide to penetration testing (8): Authority maintenance analysis and defense
Online Safe Trajectory Generation For Quadrotors Using Fast Marching Method and Bernstein Basis Poly
内网渗透系列:内网隧道之dnscat2
[NLP notes] preliminary study on CRF principle
Read and modify the JSON file under the resource folder
Gets the maximum getmaxpoint in the list of all points
C problem of marking the position of polygons surrounded by multiple rectangles
三分钟教你用Houdini流体>>解算粒子流体水滴
When using flash, the code ends automatically without an error, the connection cannot be maintained, and the URL cannot be accessed.
SAP自建表log功能开启
关于unity获取真实地理地图转3D化的相关链接
Mysql database backup and recovery under Linux (full + incremental)
Teach-Repeat-Replan: A Complete and Robust System for Aggressive Flight in Complex Environments
SAP TR手动导入系统操作手册