当前位置:网站首页>Come in and teach you how to solve the problem of port occupation
Come in and teach you how to solve the problem of port occupation
2022-04-23 20:31:00 【Different 213】
List of articles
close windows Port occupied in , Like the ones that we see all the time 8080 The port is occupied , Solve the problem easily in two steps .
One : Find port PID( The following contents are as follows 8080 For example, the port is occupied )
Open the command line tool , Input :netstat -aon|findstr "8080"
Get the information shown in the figure below :

- TCP For the agreement
- 0.0.0.0:8080 For local address
- 0.0.0.0:0 Is the external address
- LISTENING Indicates that the port is listening
- 10224 That's what we're looking for PID
Two : close PID process
Open Task Manager , find PID Corresponding process location , End the process .
As shown in the figure below :
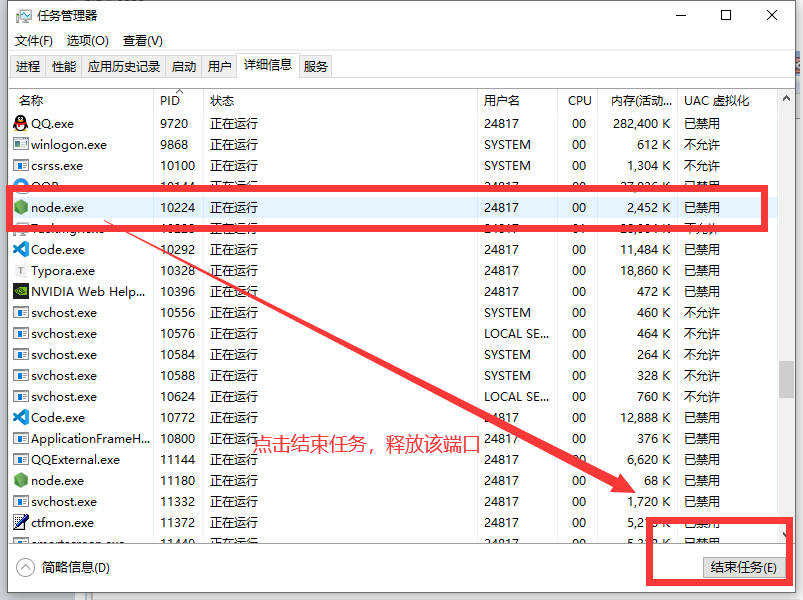
At this point, the problem of port occupation is solved ! Want to continue to learn more about how to query ports PID Problem partner , You can continue to read article 3 .
3、 ... and : netstat command ( Check the port )
netstat Commands are used to display and IP 、TCP 、UDP and ICMP Protocol related statistics , Generally used to check the network connection of each port of the machine , have access to netstat Command to view the ports in the computer .
Use netstat /? You can see netstat All arguments to the command :

The common parameters are as follows :
-a : Show all active tcp Connect , And computer monitoring tcp and udp port .
-e : Displays the number of bytes sent and received by Ethernet 、 Number of digital packets, etc .
-n : Show all active in numeric form only tcp The address and port number of the connection .
-o : Show active tcp Connect and include processes for each connection id.
-s : Display statistics of various connections by protocol , Including port number .
Among them, there are -a 、-n 、-o Especially commonly used .
What we use netstat -aon|findstr "8080" Orders are based on netstat Command implemented .
findstr yes Window The system's own commands , The purpose is to find one or more specified files, which contain ( Or through parameters /V To control the exclusion of ) Lines of certain strings , And print out the complete information of the line , Or print the file name where the query string is located .
版权声明
本文为[Different 213]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204210550450869.html
边栏推荐
- RT-1052学习笔记 - GPIO架构分析
- 2022DASCTF Apr X FATE 防疫挑战赛 CRYPTO easy_real
- Numpy sort search count set
- Zdns was invited to attend the annual conference of Tencent cloud basic resources and share the 2020 domain name industry development report
- SQL: query duplicate data and delete duplicate data
- Linux64Bit下安装MySQL5.6-不能修改root密码
- Implementation of mypromise
- Commit and rollback in DCL of 16 MySQL
- Solution: NPM err! code ELIFECYCLE npm ERR! errno 1
- 三十一. `prototype`显示原型属性和`__proto__`隐式原型属性
猜你喜欢

Devaxpress report replay: complete the drawing of conventional two-dimensional report + histogram + pie chart
DNS cloud school | analysis of hidden tunnel attacks in the hidden corner of DNS
JDBC tool class jdbcfiledateutil uploads files and date format conversion, including the latest, simplest and easiest way to upload single files and multiple files
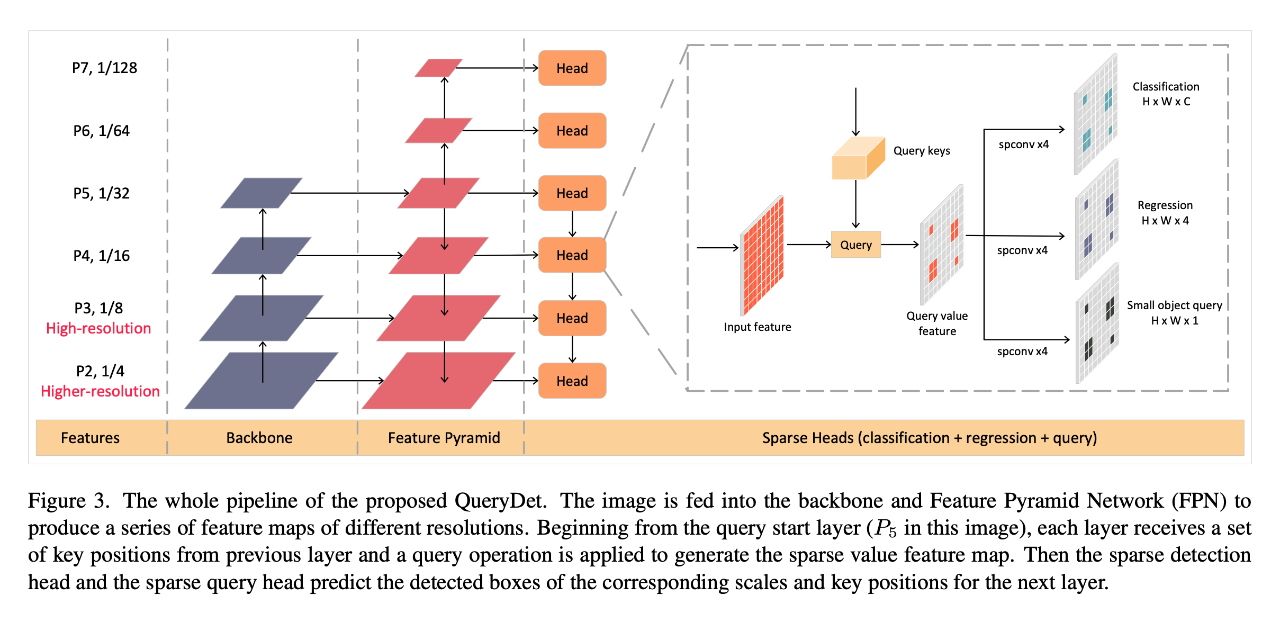
CVPR 2022 | querydet: use cascaded sparse query to accelerate small target detection under high resolution

. Ren -- the intimate artifact in the field of vertical Recruitment!
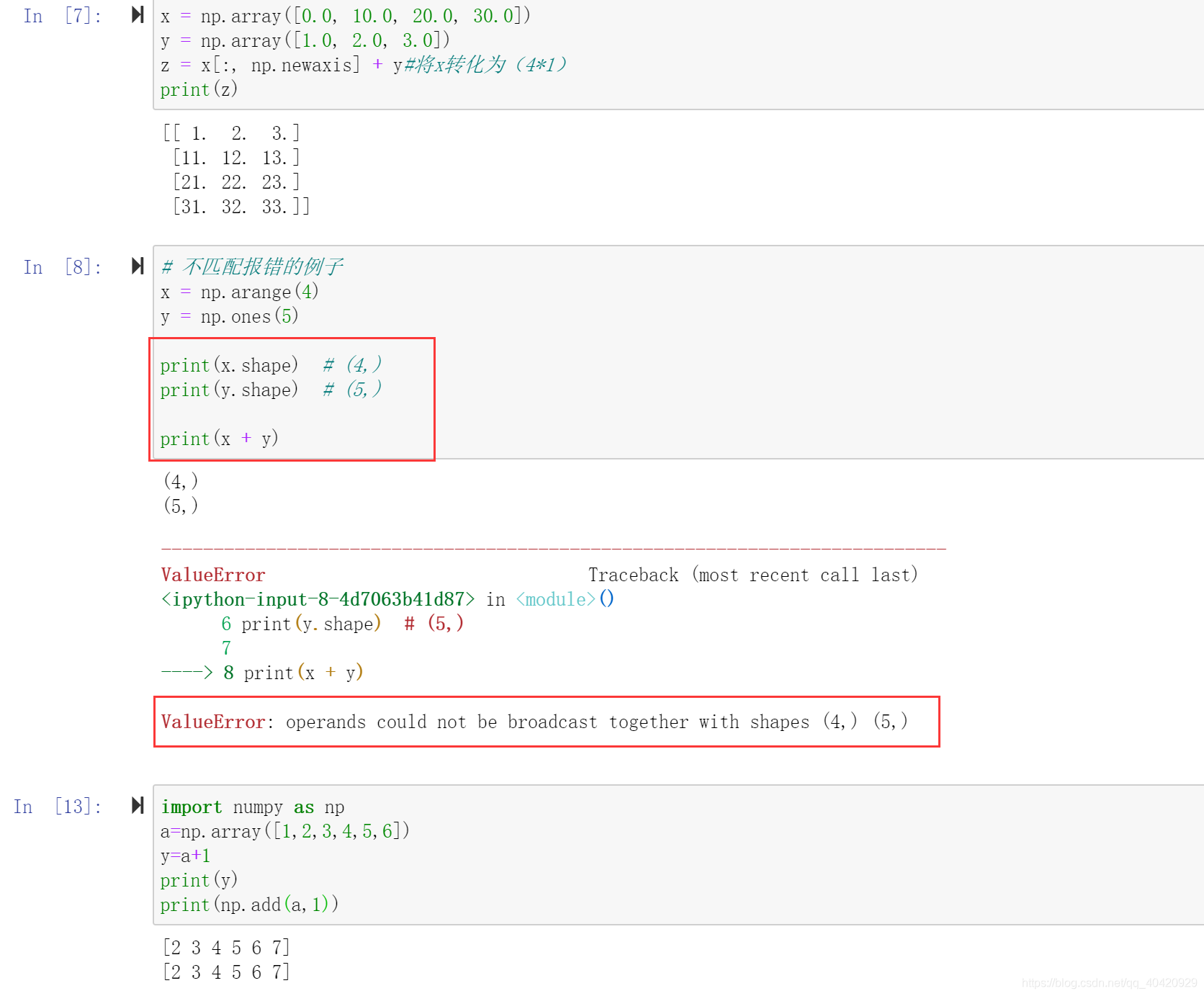
Numpy mathematical function & logical function
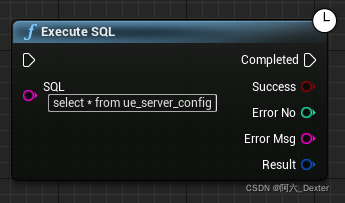
SQL Server connectors by thread pool 𞓜 instructions for dtsqlservertp plug-in
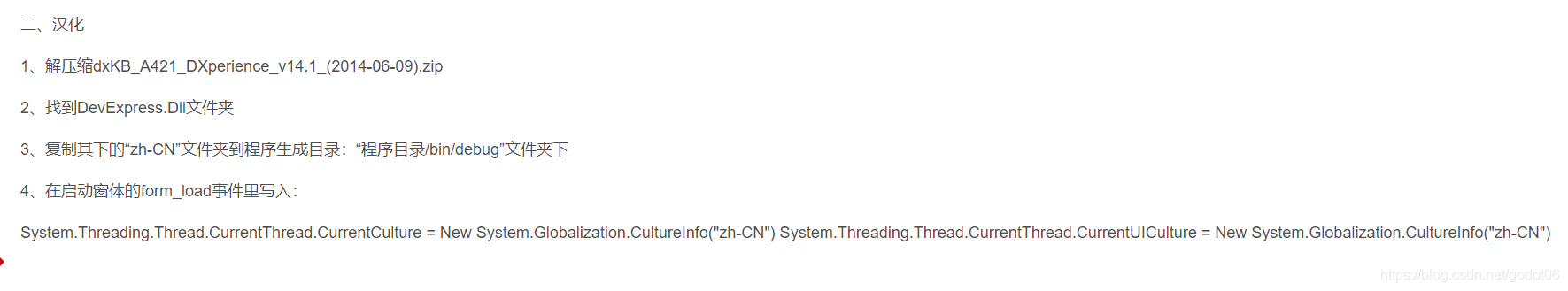
Devexpress 14.1 installation record
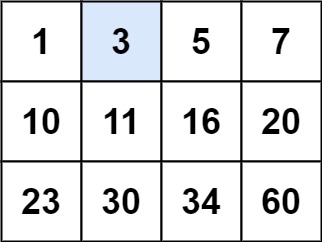
Leetcode 74. Search two-dimensional matrix
LeetCode 542、01 矩阵
随机推荐
Research on open source OCR engine
Solution to PowerDesigner's failure to connect to MySQL in x64 system
Rt-1052 learning notes - GPIO architecture analysis
SQL: query duplicate data and delete duplicate data
Identification of bolt points in aerial photography based on perception
內網滲透之DOS命令
Plato Farm元宇宙IEO上线四大,链上交易颇高
DOS command of Intranet penetration
Some basic knowledge of devexpress report development
堡垒机、跳板机JumpServer的搭建,以及使用,图文详细
How to protect ECs from hacker attacks?
[PTA] l1-002 printing hourglass
Matlab analytic hierarchy process to quickly calculate the weight
Rédaction de thèses 19: différences entre les thèses de conférence et les thèses périodiques
star
Operation of numpy array
三十.什么是vm和vc?
PostgreSQL basic functions
Leetcode 1346. Check whether integers and their multiples exist
The market share of the financial industry exceeds 50%, and zdns has built a solid foundation for the financial technology network