当前位置:网站首页>Detailed explanation of information abstract, digital signature, digital certificate, symmetric encryption and asymmetric encryption
Detailed explanation of information abstract, digital signature, digital certificate, symmetric encryption and asymmetric encryption
2022-04-23 16:40:00 【GokuCode】
The information in this paper, 、 digital signature 、 digital certificate 、 Symmetric encryption and asymmetric encryption
Anti theft statement : Other websites found that they were pirated
The only link to this article :https://blog.csdn.net/weixin_44331765/article/details/124220044
1. Problem description
- The information in this paper, 、 digital certificate 、 What is the use of symmetric encryption and asymmetric encryption , Why do you need these .
2. Problem solving
Let's use a small example to illustrate .
Three characters : the Red Army 1、 the Red Army 2、 Blue army
Scenario description : the Red Army 1 To the Red Army 2 Send a message saying to launch an attack , With the sending scenario .
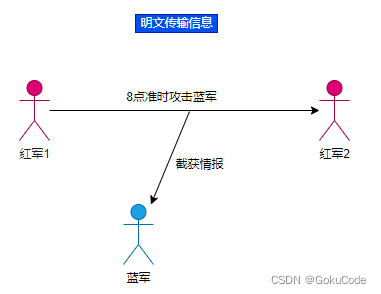
scene 1: Plaintext transmission information
At first , The Red Army did not realize the importance of information security , So direct plaintext transmission of information . therefore , It was soon acquired by the Blues , Then the red army fought and lost again and again .
You can see that if the blue army intercepts intelligence , You can immediately see what the content is , Because the red army uses clear text transmission .
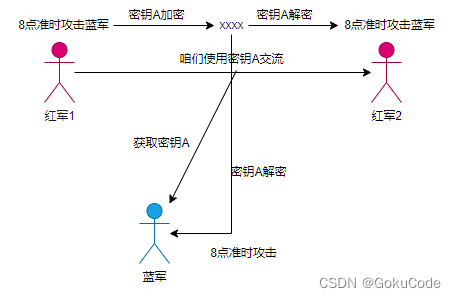
scene 2: Symmetric encryption
Symmetric encryption : Use key A encryption , Decryption also uses A The key is symmetric encryption . Specific details can be searched by yourself .
Then tell the story , After the Red Army found that it was intercepted by the blue army , Prepare to use symmetric encryption . So the key is used A. As a result, the key was monitored during transmission . The blues got the key A.
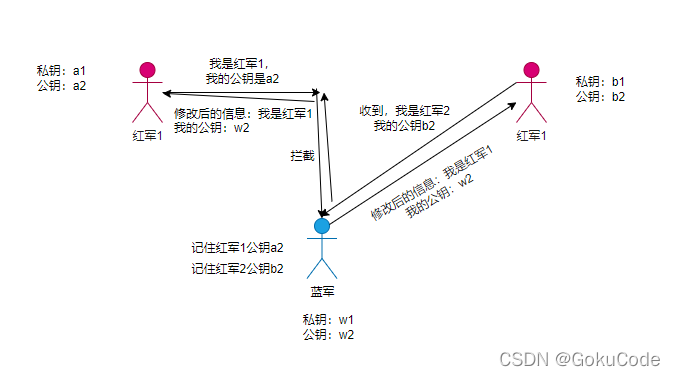
scene 3: Use asymmetric encryption
Asymmetric encryption : Use public key encryption ( In fact, it's not called encryption , Because it's a public key , So it's an open secret , So it's called signature , That is, digital signature ), Only the private key can be decrypted , Similarly, using the private key to encrypt , Only public key decryption can be used .
Realization principle :
the Red Army 1: Private key a1 Public key a2
the Red Army 2: Private key b1 Public key b2
The Red Army wanted to : Even if the blues get information encrypted with a public key , It can't be cracked , Because it has no private key . The Blues... But they don't , It can do this :
The blues know and make their own Private key w1 Public key w2. So there was a situation .
The Blues have become middlemen , There will be such a process of sending messages
the Red Army 1: Use w2 Encrypted messages
Blue army : After receiving the message, use w1 Decrypt
Use b2 The encrypted message is sent to the user 2
the Red Army 2: Received and used b1 Decrypt
The middle Red Army 12 No problem , The blue army can also get information .
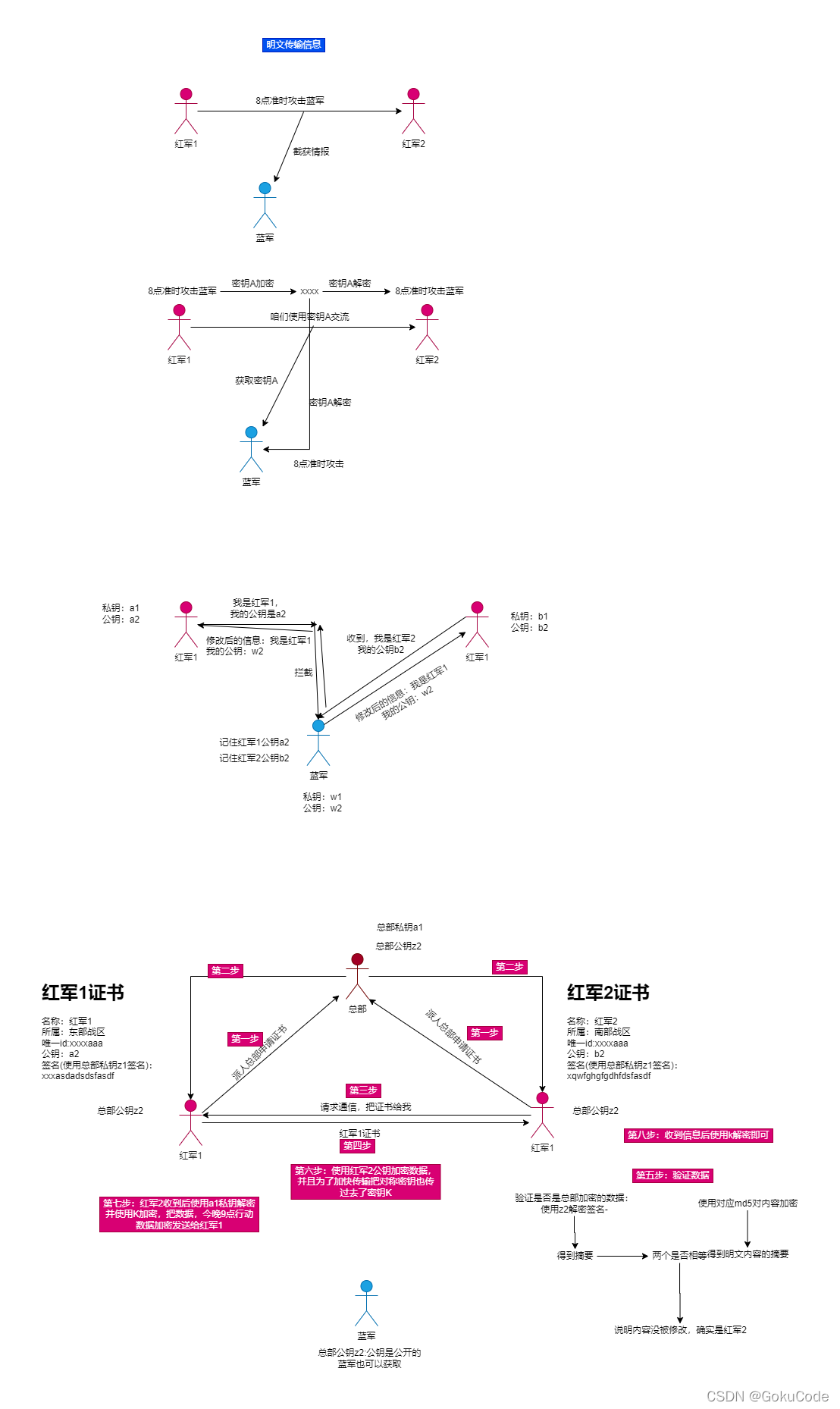
scene 4: Using digital certificates
The Red Army found a blue middleman , So we need to improve the encryption method , In order to let the other party know that the public key is his own , The public key cannot be tampered with , So digital certificates are used . the Red Army 1 Certificate used , Certificate information mainly includes the following contents :
Digital certificate version :1.0
name : the Red Army 1
Belongs to : World War II
only id:xxxxa1
Public key :a1
Detailed introduction : The army is xxxx Omit here 1 swastika
Certificate size :100M
But to the Red Army 2, Not yet. , Because of this, if some part of the certificate, especially the public key, is tampered with , What if it's forged by the blue army . Still can't prove . Then you need to use encryption to ensure that the data is not tampered with . Use md5 To encrypt , If one content is changed , that md5 The value will also change .
Digital certificate version :1.0
name : the Red Army 1
Belongs to : World War II
only id:xxxxa1
Public key :a1
Detailed introduction : The army is xxxx Omit here 1 ten thousand
Certificate size :100M
Yes 100M After data encryption :xjajaksd89as7df89asdf67asd78a7ds
For the above encryption , the Red Army 1 Find out , The encrypted content is too long , A certificate 1 More than ten thousand words , It takes half an hour to complete the encryption . Too slow , Can you put forward some important , To encrypt , Improve encryption speed . So there was The information in this paper, , We propose to use the private key to sign hundreds of words, that is, digital signature , It's like an abstract in a paper , As long as we read a few hundred word abstract, we will know what this paper is about .
So this also needs the algorithm of information summary extraction ( Interested in self searching )
The encrypted content becomes smaller , Encryption speed is also fast . It can also ensure data integrity
Digital certificate version :1.0
name : the Red Army 1
Belongs to : World War II
only id:xxxxa1
Public key :a2
Detailed introduction : The army is xxxx Omit here 1 ten thousand
Certificate size :100M
The information in this paper, :1kb
the Red Army 1 Use the private key pair 1kb Data signature :xjajaksd89as7df89asdf67asd78a7ds
But to prove this certificate is the Red Army 1 Yes or no , Because if the middle is modified by the Blues , the Red Army 2 I can't find out .
Digital certificate version :1.0
name : the Red Army 1
Belongs to : World War II
only id:xxxxa1
The blue army modified the public key :w2 <---------------- The blues moved their hands and feet
Detailed introduction : The army is xxxx Omit here 1 ten thousand
Certificate size :100M
The information in this paper, :1kb
Blue army private key re signature :xwwwwksd8wwdf89asdf67asd78a7ds <---------------- The blues moved their hands and feet
To the Red Army 2, the Red Army 2 I can't find out .
This is the time , The Red Army is going to find the headquarters . Everyone at headquarters has a public key , Can be obtained from the Red Army Headquarters . That is, the Red Army 2 The headquarters knows in advance z2
So the Red Army 1 Give the certificate to the headquarters , The headquarters signs with its own private key
Digital certificate version :1.0
name : the Red Army 1
Belongs to : World War II
only id:xxxxa1
the Red Army 1 Public key :a2
Detailed introduction : The army is xxxx Omit here 1 ten thousand
Certificate size :100M
The information in this paper, :1kb
Headquarters private key signature :xwwwwksd8wwdf89asdf67asd78a7ds
This is the time , Even if the blues get it, they can't modify it , Because the Red Army 2 There is a public key of the headquarters , If the information is modified , The Blues have no headquarters , So I can't sign , Even if you sign , Public key z2 Can't decrypt the signature , So the Red Army 2 It can be said that this is not the Red Army 1 Certificate
The general picture
3. reminder , See you in the comment area if you have any questions
版权声明
本文为[GokuCode]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204231640214922.html
边栏推荐
- How to conduct application security test (AST)
- Day 10 abnormal mechanism
- Government cloud migration practice: Beiming digital division used hypermotion cloud migration products to implement the cloud migration project for a government unit, and completed the migration of n
- Force buckle-746 Climb stairs with minimum cost
- Report FCRA test question set and answers (11 wrong questions)
- G008-hwy-cc-estor-04 Huawei Dorado V6 storage simulator configuration
- JSP learning 2
- Set cell filling and ranking method according to the size of the value in the soft report
- Detailed explanation of file operation (2)
- Dlib of face recognition framework
猜你喜欢

299. Number guessing game
英语 | Day15、16 x 句句真研每日一句(从句断开、修饰)
Use case labeling mechanism of robot framework
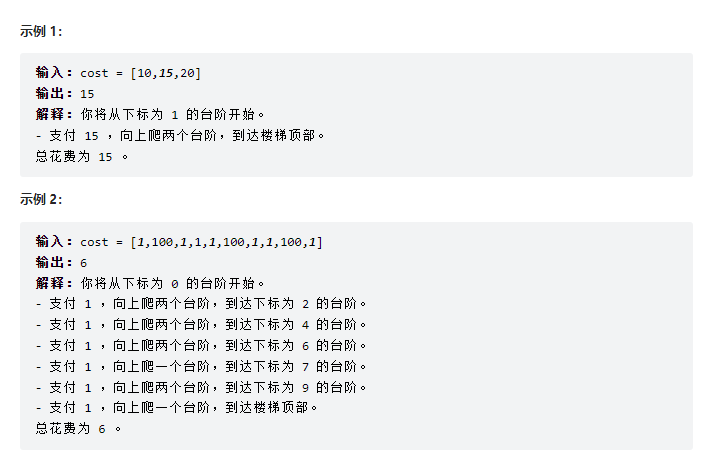
Force buckle-746 Climb stairs with minimum cost

安装及管理程序
DanceNN:字节自研千亿级规模文件元数据存储系统概述

Zhongang Mining: Fluorite Flotation Process
DDT + Excel for interface test
Day 10 abnormal mechanism
RAID磁盘阵列与RAID5的创建
随机推荐
Disk management and file system
How magical is the unsafe class used by all major frameworks?
Dancenn: overview of byte self-developed 100 billion scale file metadata storage system
PHP 零基础入门笔记(13):数组相关函数
JIRA screenshot
Use itextpdf to intercept the page to page of PDF document and divide it into pieces
力扣-746.使用最小花费爬楼梯
NVIDIA graphics card driver error
JMeter setting environment variable supports direct startup by entering JMeter in any terminal directory
New project of OMNeT learning
ByteVCharts可视化图表库,你想要的我都有
Differences between MySQL BTREE index and hash index
Construction of promtail + Loki + grafana log monitoring system
深入了解3D模型相关知识(建模、材质贴图、UV、法线),置换贴图、凹凸贴图与法线贴图的区别
JMeter installation tutorial and solutions to the problems I encountered
Hypermotion cloud migration completes Alibaba cloud proprietary cloud product ecological integration certification
Findstr is not an internal or external command workaround
磁盘管理与文件系统
Sail soft segmentation solution: take only one character (required field) of a string
The most detailed Backpack issues!!!